Streamlining Data Governance at Scale with Identifiers in Domains
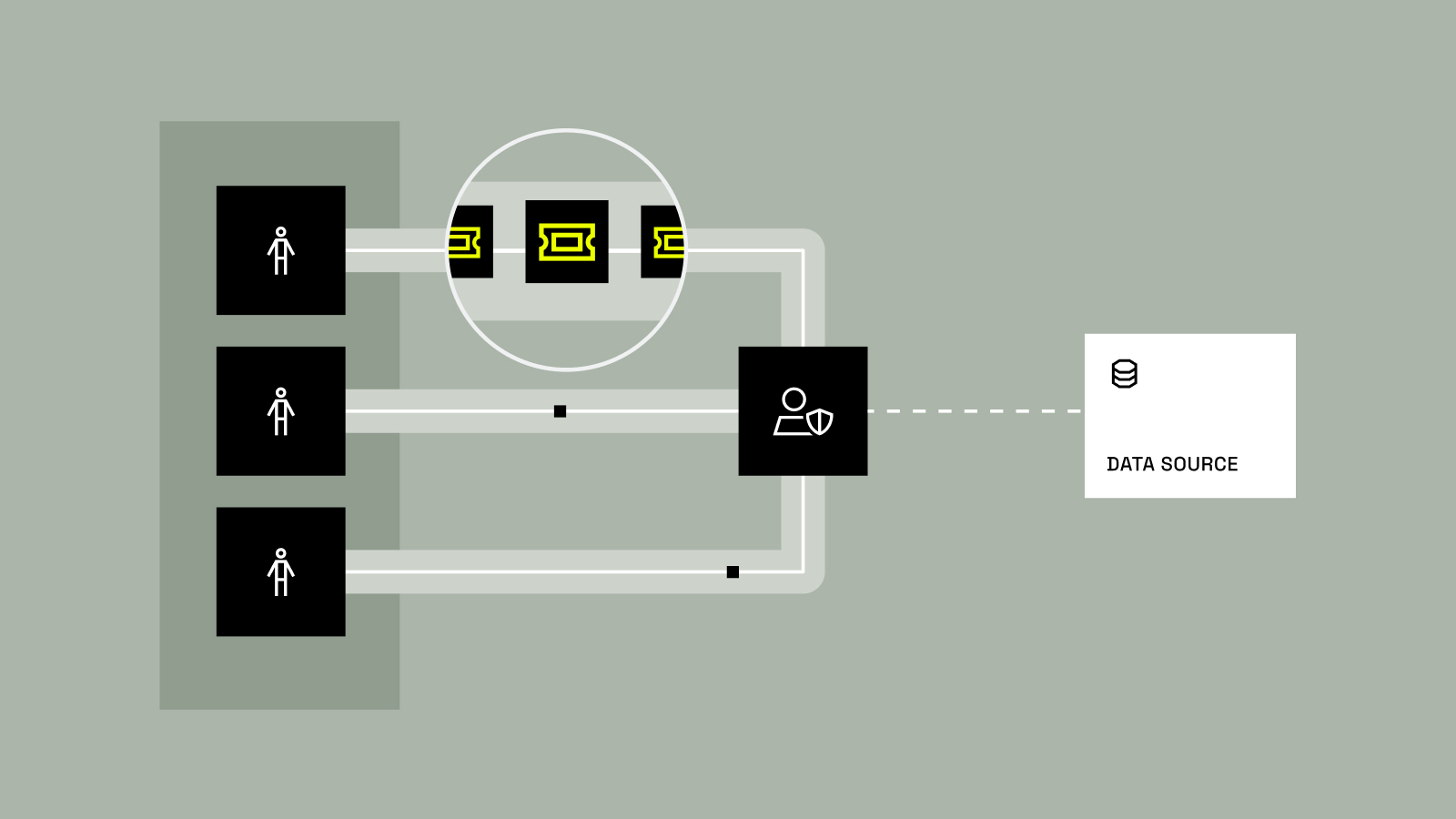
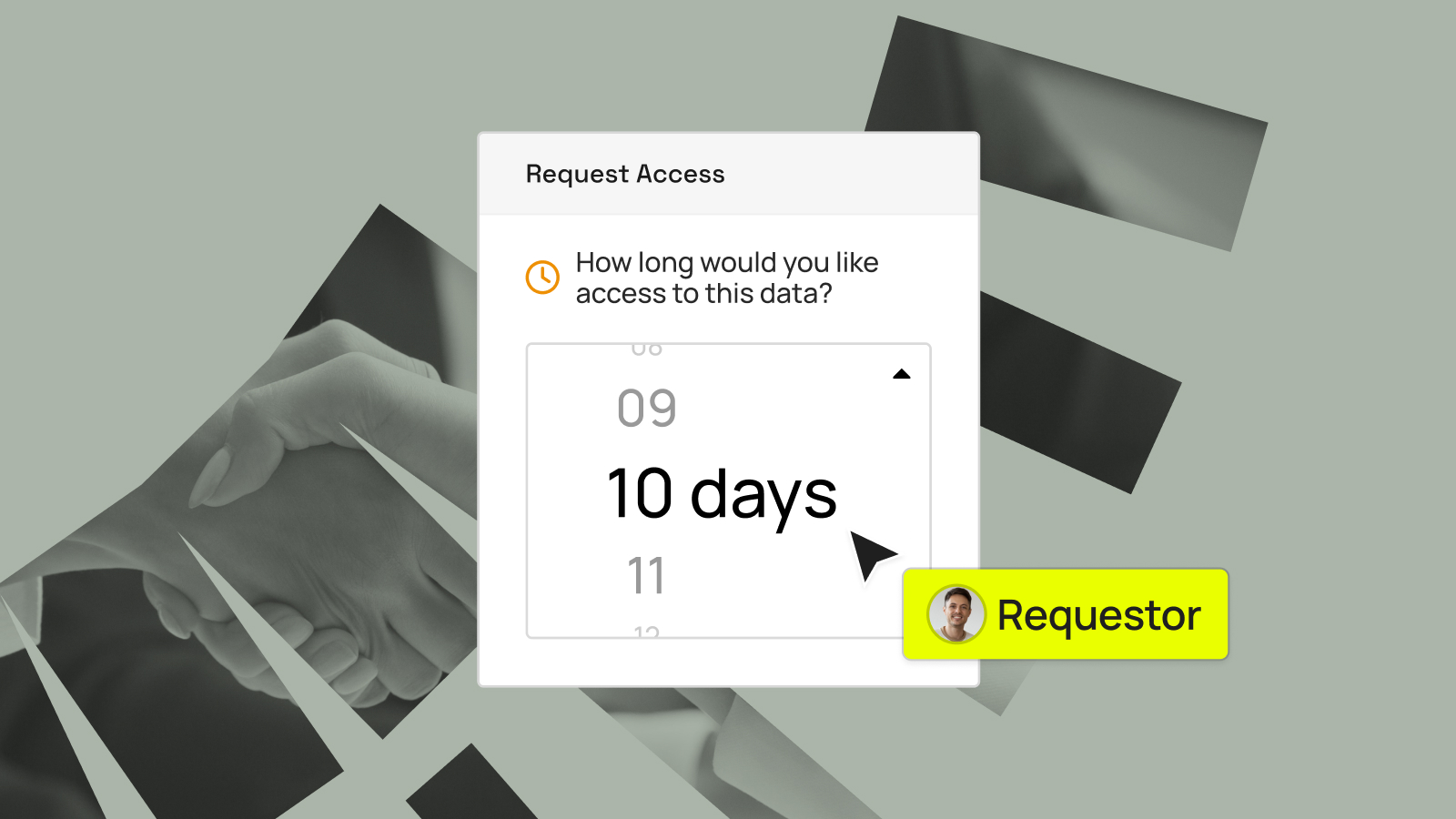
Key Takeaways Immuta’s identifiers in domains feature is now generally available to all global customers. It addresses a critical gap in traditional metadata catalogs by making sensitive data discoverable and governable within domain boundaries, which adds critical context to policy enforcement. This capability empowers domain governors to classify and control...