With massive amounts of data being generated each day, and an increasing number of people accessing, analyzing, and sharing that data, understanding all data access activity is more than a full-time job. In fact, it can feel downright unmanageable.
The good news? With the right tools, you can get the insights you need to ensure data access is secure, compliant, and auditable.
What is Data Access Auditing?
In the data realm, access auditing refers to the ability to monitor, inspect, and document how data is being accessed by users across an organization. It is a key to building data audit trails, which are detailed logs of every action or activity taken related to data.
Access auditing is critical in proving compliance with regulations like the GDPR and HIPAA, as well as with data use agreements. In addition, it can help proactively identify anomalies and potential threats within your ecosystem, so you can take steps to mitigate or remediate them.
Access Auditing Challenges
The amount of data and number of data users continues to grow at an exponential rate, increasing the risk of unauthorized access. Data teams are grappling with the challenge of sieving through an enormous amount of audit data across a disparate set of external systems, correlating the logs across the systems like Snowflake and Databricks, and determining who accessed what data and when.
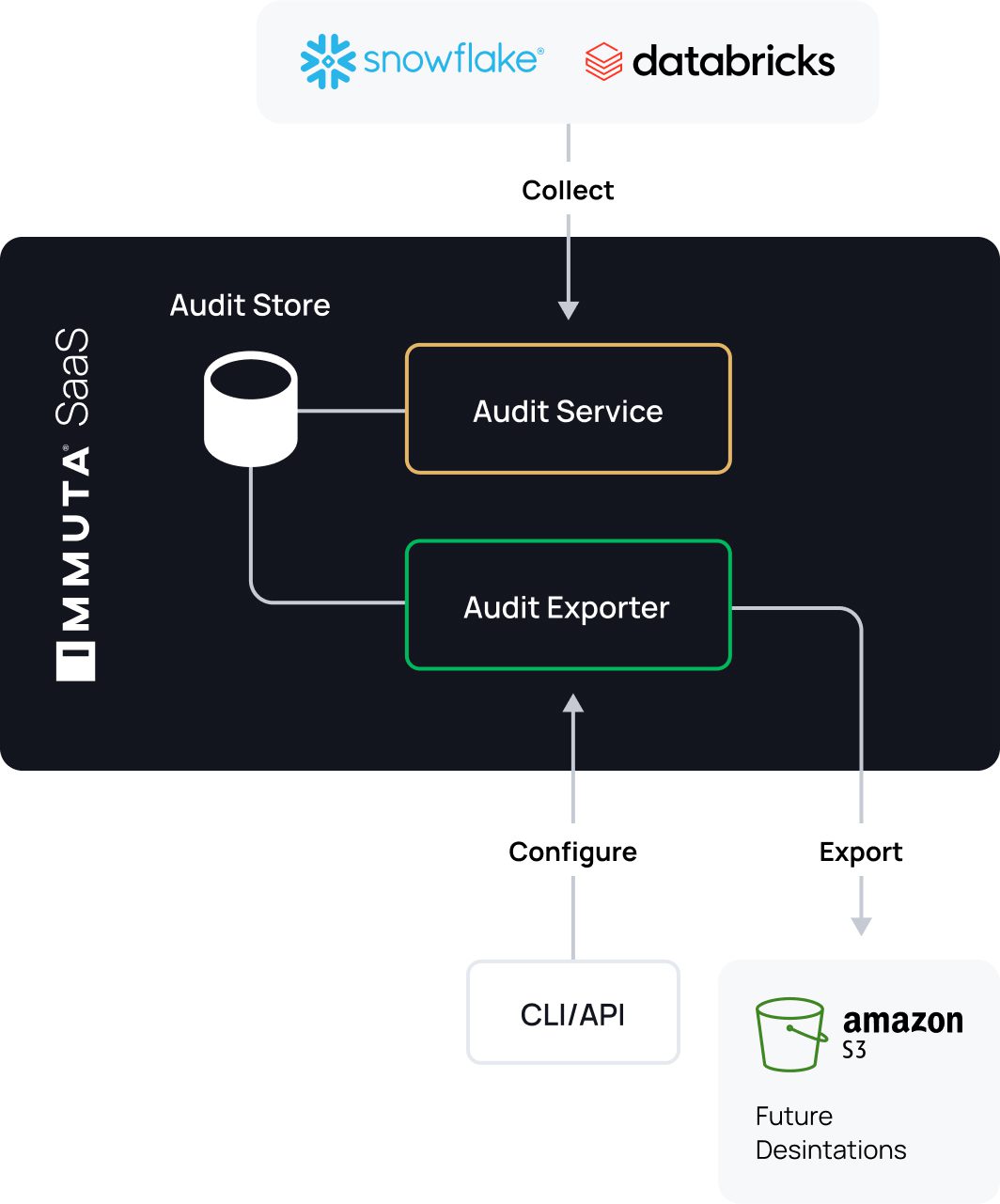
With Immuta’s Unified Audit Model (UAM), you can now quickly and easily push a consistent audit log structure and metadata from various systems to storage platforms including Amazon S3, and then to cloud SIEMs like Splunk or even platforms such as Snowflake, for simplified filtering and analysis across a range of events.
In this blog, we’ll explore the access auditing objectives of Immuta’s UAM, how it works in practice, and what it can mean for your team’s cloud data management and security.
Why Comprehensive Access Auditing is Essential
The goal of a unified audit model is predicated on having comprehensive data access management for the enterprise that spans three key pillars: data discovery, data security, and data monitoring. With that in mind, Immuta is continuously working to innovate around each of those pillars.
To improve data monitoring and threat detection capabilities, governance, risk, and compliance (GRC) stakeholders, audit teams, and security teams need an easier and more efficient way to leverage all of the information captured in audit logs that solutions like Immuta generate. However, users often manually load data into their analytics tool of choice and sieve through a massive amount of log data for arduous but necessary tasks like compliance verification.
Simplifying Access Auditing with Immuta’s Unified Audit Model
Immuta’s UAM provides a stepping stone towards comprehensive access auditing and management by providing:
- Consistent audit log structure and metadata across audit events
- Simple search and filtering capabilities
- Automatic pushes of data into choice systems for storage and analysis
This helps simplify and accelerate data teams’ ability to filter and analyze audit data, while also empowering GRC, audit, and security teams to do so. Immuta’s UAM comes with a new API, audit log exporter, and command line interface (CLI). Initially, it will provide audit events for Snowflake and Databricks, but will be rolled out for other platforms over time.
Some of the key capabilities and attributes of Immuta’s UAM include:
Consistent Audit Log Structures and Metadata
By enabling a consistent audit log structure and metadata across access auditing events, both from Immuta and all connected platforms, Immuta’s UAM centralizes and simplifies filtering and analysis. Immuta policy configuration events are also forthcoming.
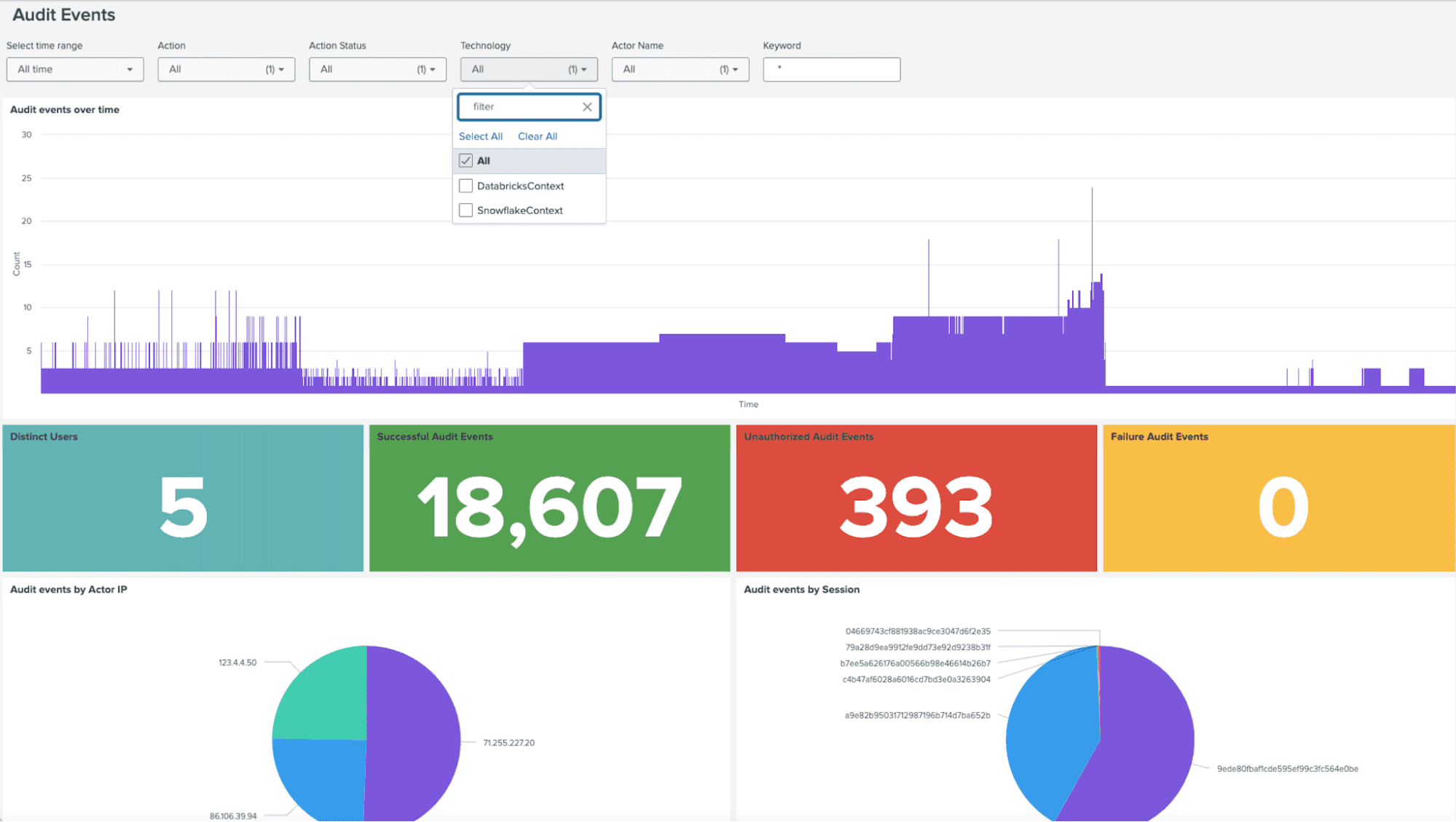
Below is an example of how the audit events that Immuta generates would appear for users:
Data Access Audit Events
- Action Names (e.g QUERY) + Target (e.g. data source)
- Action Status (SUCCESS, FAILED, UNAUTHORIZED)
- Action Status Reason (why something failed)
- Actor IP (when available)
- Session ID (when available, enables chaining events together during the same session)
- Start/End Time for the query (now only in Snowflake)
- DENIED logs for Databricks
- Policy Set – now embedded in Databricks audit events so customers can perform root cause analysis of why a user was able (or not able) to query. UAM will support any other native integration that enables this.
Support for Additional Event Metadata
When more detail can be derived from fields, Immuta’s UAM is able to incorporate the additional audit event metadata, enabling a richer, more holistic analysis. This includes user attributes, impersonated users, session IDs, Actor IPs, table names, and technologies.
Search and Filtering Capabilities
Integrating consistent metadata enables support for advanced filtering, as well as grouping by variables like action and target. This increases efficiency by returning only the requested information, which in turn reduces payload. As functionality is further developed, Immuta’s UAM will also enable custom queries.
Audit Log Export for SaaS
Immuta’s UAM acts as a push mechanism for audit information from Immuta’s SaaS data security environment. This includes a scheduled export capability, as well as a generic audit exporter that is ready to support additional destinations.
Next Steps
To get an in-depth look at UAM and other capabilities, book a demo with our team.