
In the cloud computing era, ensuring data policy is co-created with data is essential. Historically, data access and security policies were an afterthought, leading to sub-optimal implementations. These implementations give rise to confusion, data leaks, and unsustainable maintenance burdens.
In order to be effective, organizations need to separate policy from cloud platforms. This separation allows the policy to be created at the data curation level, understood and approved by data owners, and audited by compliance teams. In this blog, we will discuss why Immuta provides value to organizations in the era of modern cloud computing.
The Shift to Security-First Architectures
The time for secure data access is now. According to Cybercrime Magazine, the world will store 200 Zettabytes of data by 2025. The sheer amount of information that is now in cloud compute platforms necessitates that we rethink how security is managed. Every data engineer, business analyst, and data consumer is now effectively a steward of privacy: whether bound by a contract or by sharing and using the data in an appropriate manner.
Traditional access control systems are not built for this ever-changing landscape that requires fine-grained authorization. One of Immuta’s customers, Pumpjack Dataworks, illustrates this point perfectly. Corey Zwart, Head of Engineering at Pumpjack, says traditional role-based access control puts users in a “box” by binding user access to static roles. We couldn’t agree more. This automatically makes you less secure as you can no longer make access decisions based on individuals, but rather only on the group as a whole.
Enter Immuta. Our platform was purpose-built in the US intelligence community to ensure each user’s actions, access, and intent are audited and tracked. Immuta does this by taking access control to the lowest common denominator – the user.
In order to move to security-first architectures, organizations must be able to immediately adapt to the shifting threat landscape. Integrating intent-based access, user-level controls, and automation is key to ensuring that all data is accessed and secured appropriately. With Immuta, the policy becomes separated from the underlying data platforms, allowing organizations flexibility while ensuring the same policy in one system will apply consistently across the board. In the modern data landscape, organizations have to be quick to respond to business requirements to stay ahead of the competition, mitigate security risks, and meet legal requirements. Immuta is the key to this future.
Create Policy-as-Code Once, and Apply it Everywhere
Immuta enables users of any skill level to build a policy and enable it on every cloud platform in their organization. In order to prevent data leaks, unnecessary policy duplication, and overall confusion on access controls, it is essential to have a centralized place to create and manage these policies. Immuta is that place.
Immuta’s policy enforcement engine translates understandable, human-readable policies into underlying, platform-specific code. This is important because protecting your data from risk in the cloud is paramount. Imagine a scenario where you have Databricks, Snowflake, and Starburst. Today, users would have to create a policy for each of those systems in the syntax, technology, or platform-specific implementations. Each of these implementations could require specific skill sets that may or may not be available for your organization. With Immuta, a single policy can cascade across all cloud compute environments in a consistent manner, all while allowing users to prove intent and purpose while accessing data.
This policy can be created as simple YAML or JSON specifications, and then approved by data owners in a plain language manner that reduces policy confusion and risk of duplication. For example, consider a situation where we need to protect personally identifiable information (PII). In Immuta, creating a policy is logical, understandable, and scalable. The below policy will mask all PII in tables where Immuta has found it:
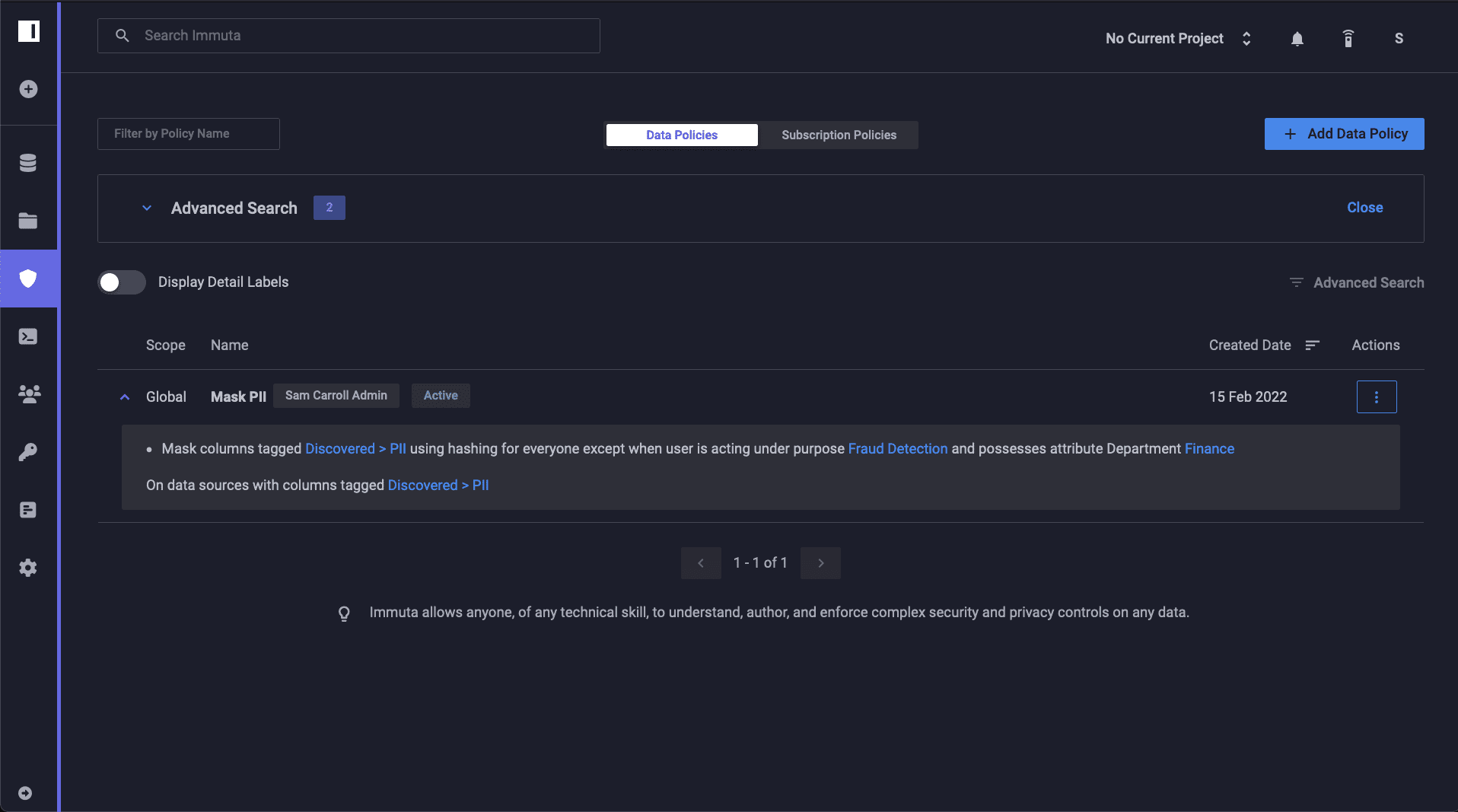
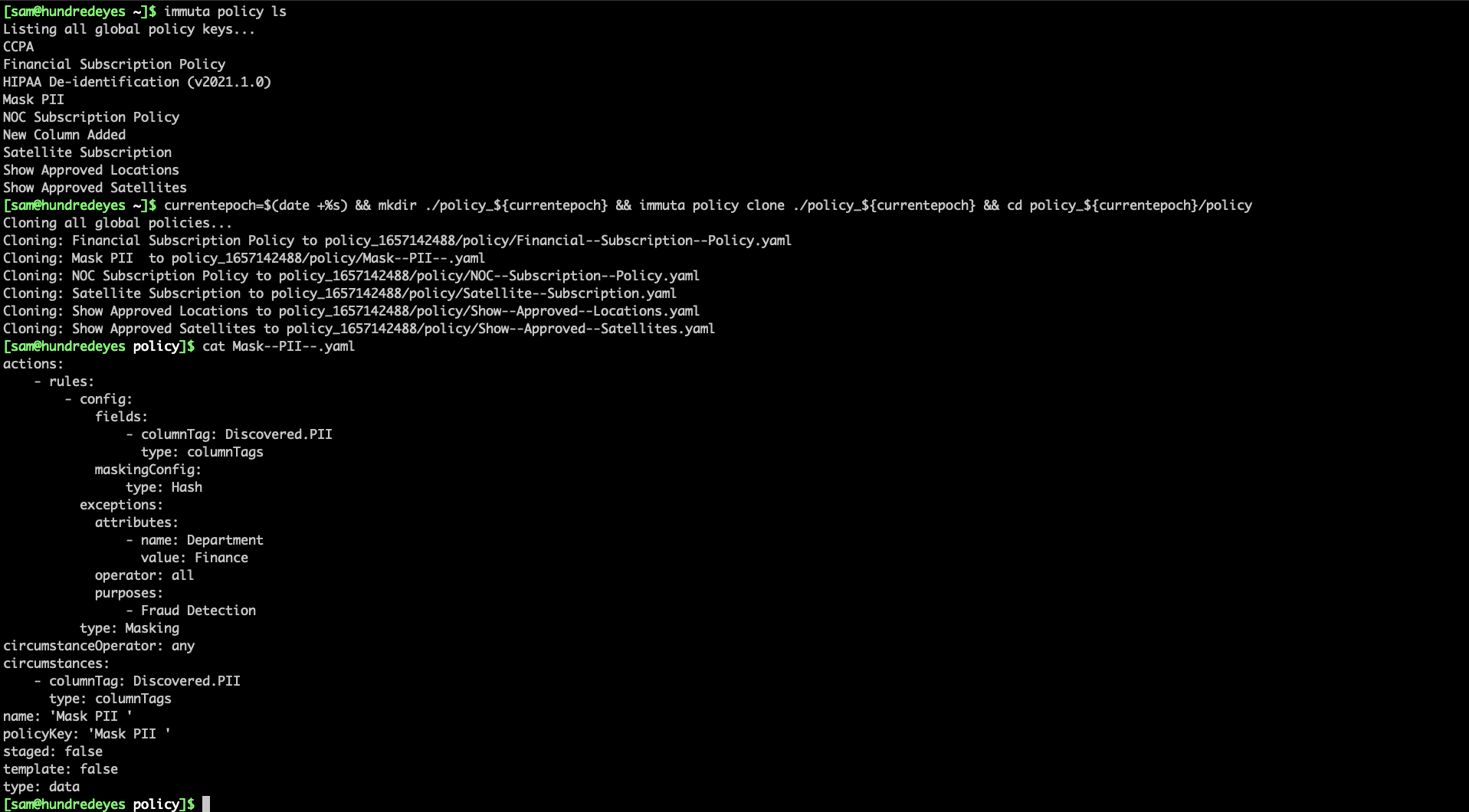
Note how easy to understand this policy is for data owners – this is the key to a successful platform. Data owners must be able to understand the rules while allowing data engineering teams the flexibility they need to enforce a policy. Below is an example of this policy in YAML format. This policy can be defined and pushed via the Immuta CLI, Python, or any tool that can call restful web services:
Now that the policy has been enabled, you will notice it applies against 15 tables that contain PII:
Immuta lets you quickly see how this was applied. Note the various systems: Snowflake, Databricks, Redshift, Starburst, Synapse:
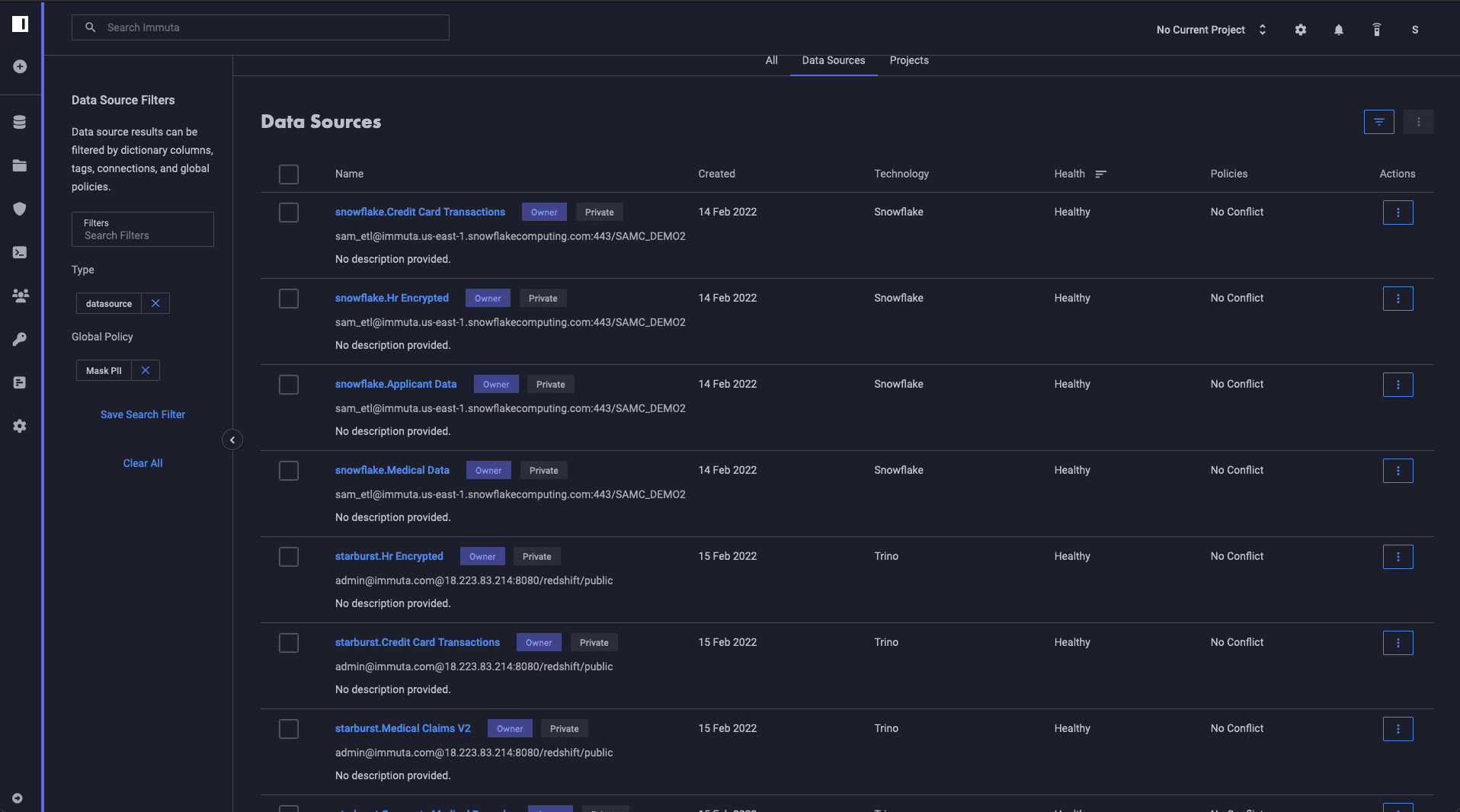
This single policy is now managing 15 tables and can scale to as many tables as needed. This provides data owners the ability to rapidly adjust, audit, and enforce rules to prevent unintended data access.
Reducing Policy Burdens and Security Risks
According to UK Law Firm DPP-DGPR, data owners are the ones held responsible for data security in the case of breaches or misuses. In traditional organizations, users are grouped into roles based on the type of access they need. In turn, those roles are mapped to data objects (views, stored procedures, filtered copies of tables, etc). The challenge is that after the users are added to these roles, the membership is hardly manageable.
At Immuta, we argue that data security is the responsibility of everyone in the organization. It starts with looking at who the user is, why they are running the query, and what data they should be allowed to access. In the paradigm above, this is virtually impossible in any organization with information stored on cloud platforms. Immuta’s three-tiered approach of discovering, securing, and monitoring data allows organizations to track policy from inception to implementation – all from a single application. With policy-as-code, you can deploy logic with your ETL pipeline, have the policy understood/approved by the data owner, and then transparently applied to the data consumer’s tables without writing platform-specific code.
How Does Immuta’s Policy-as-Code Help?
Immuta enables organizations to implement security by design for cloud data. Enabling data teams to collaborate with data owners is an essential part of how our Data Access Platform enables this. Immuta’s implementation prevents confusion, data leaks, and unsustainable maintenance burdens. Removing the tight coupling of security policies with cloud platforms is the way that organizations will achieve security at scale with Immuta.
To create a policy for yourself, try our self-guided walkthrough demos with Databricks and Snowflake.








