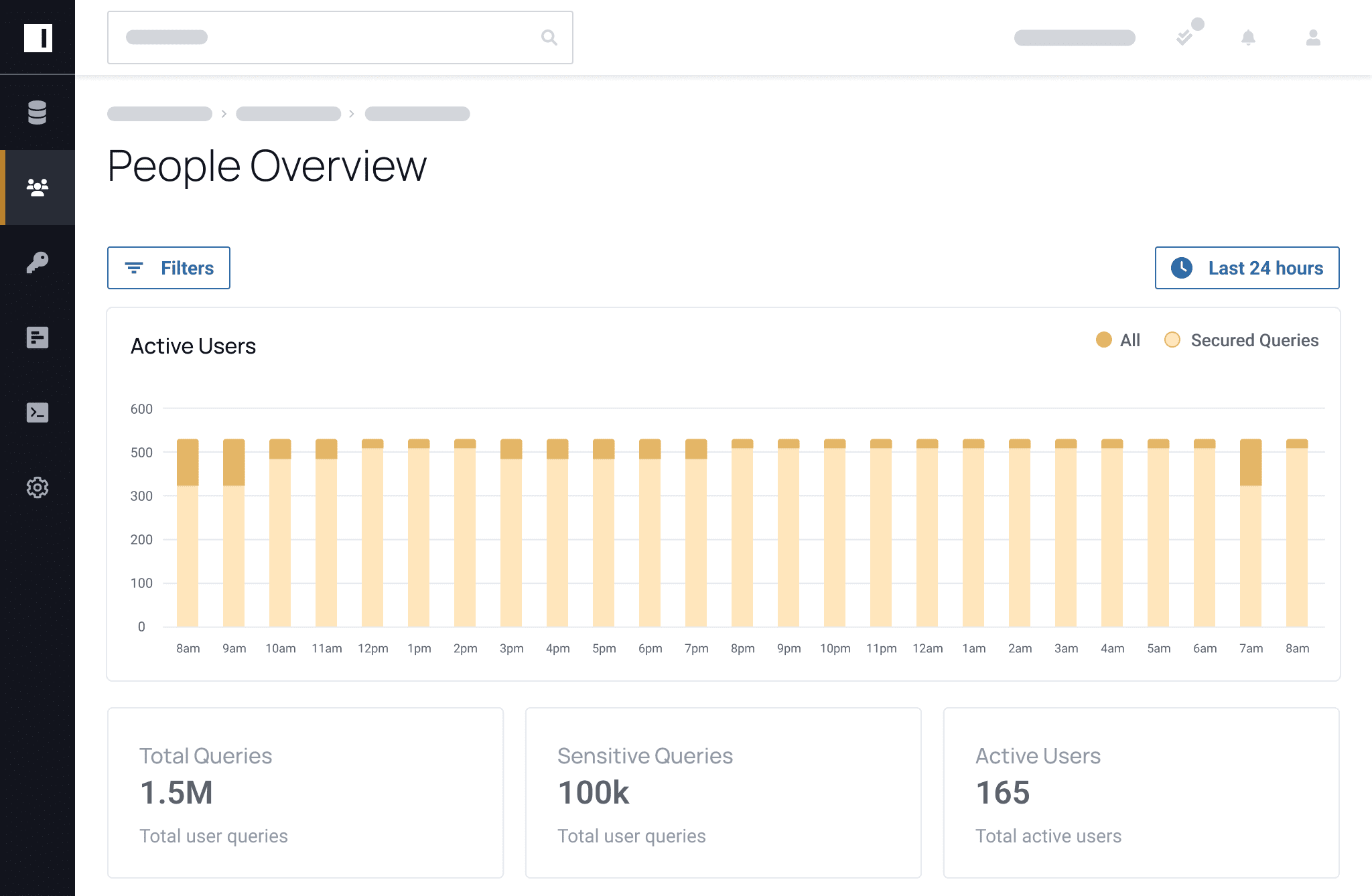
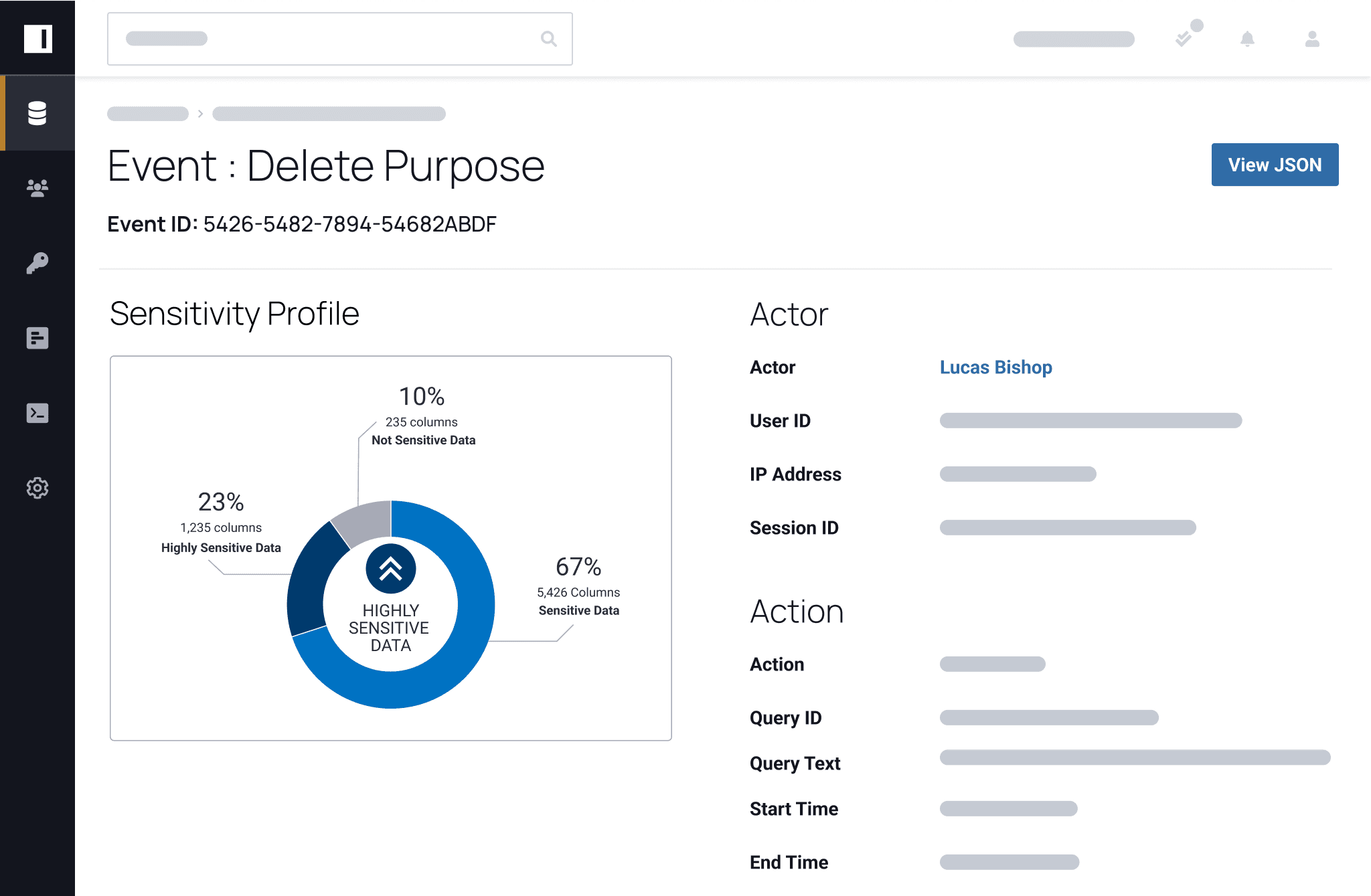
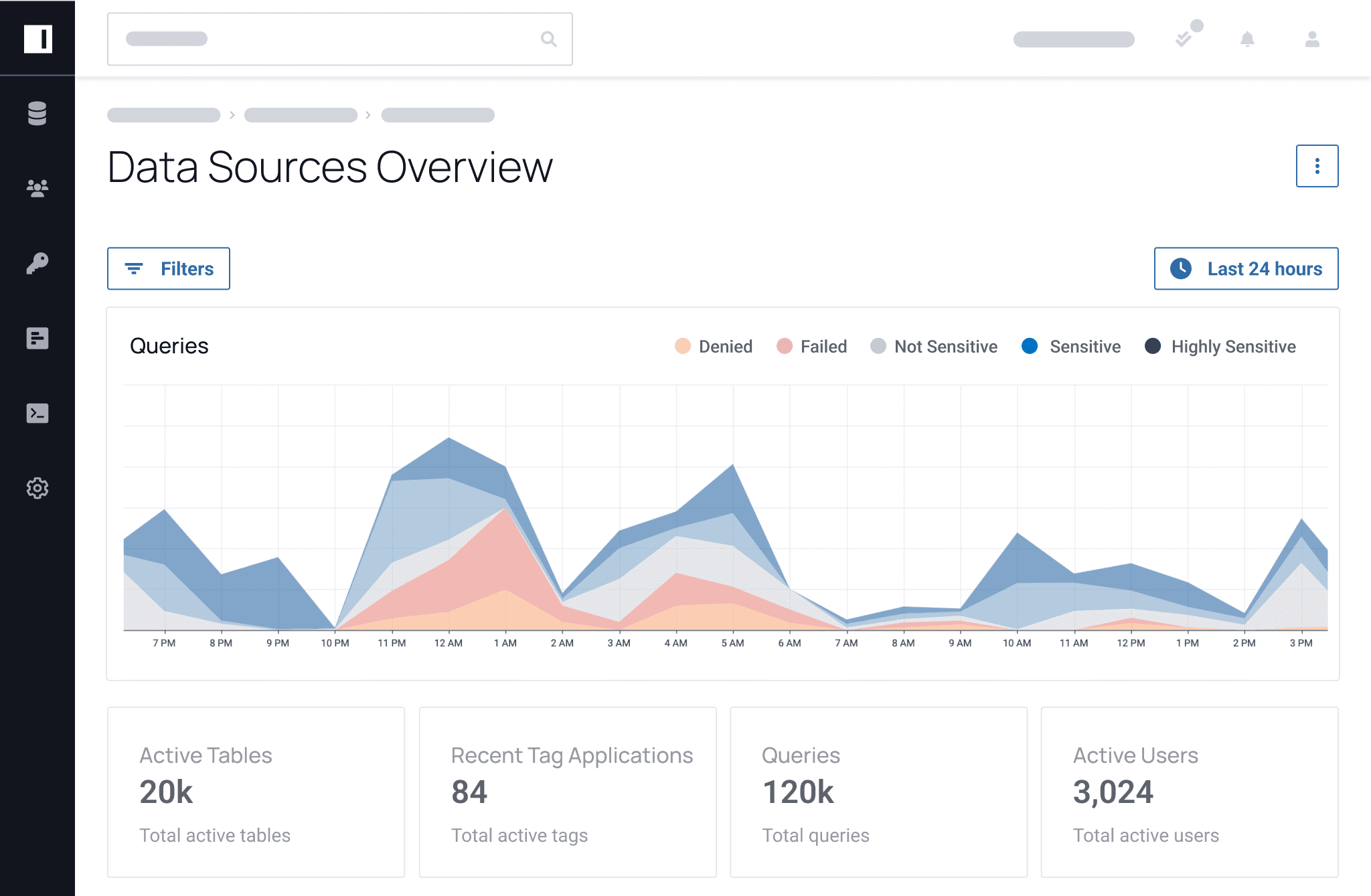
Before Immuta, we could not make our data widely available to the users due to security concerns. Immuta has allowed us to open up the data to a wide variety of users.
Covering the Full Data Security Spectrum
Once you know your potential risks, you can take action to mitigate them before they start. Knowing what data you have, where it resides, and what policies are in place to protect can increase your data security posture management and give you peace of mind that your data is protected from end to end.