Solving the Data Provisioning Crisis That’s Crushing Enterprises – With AI
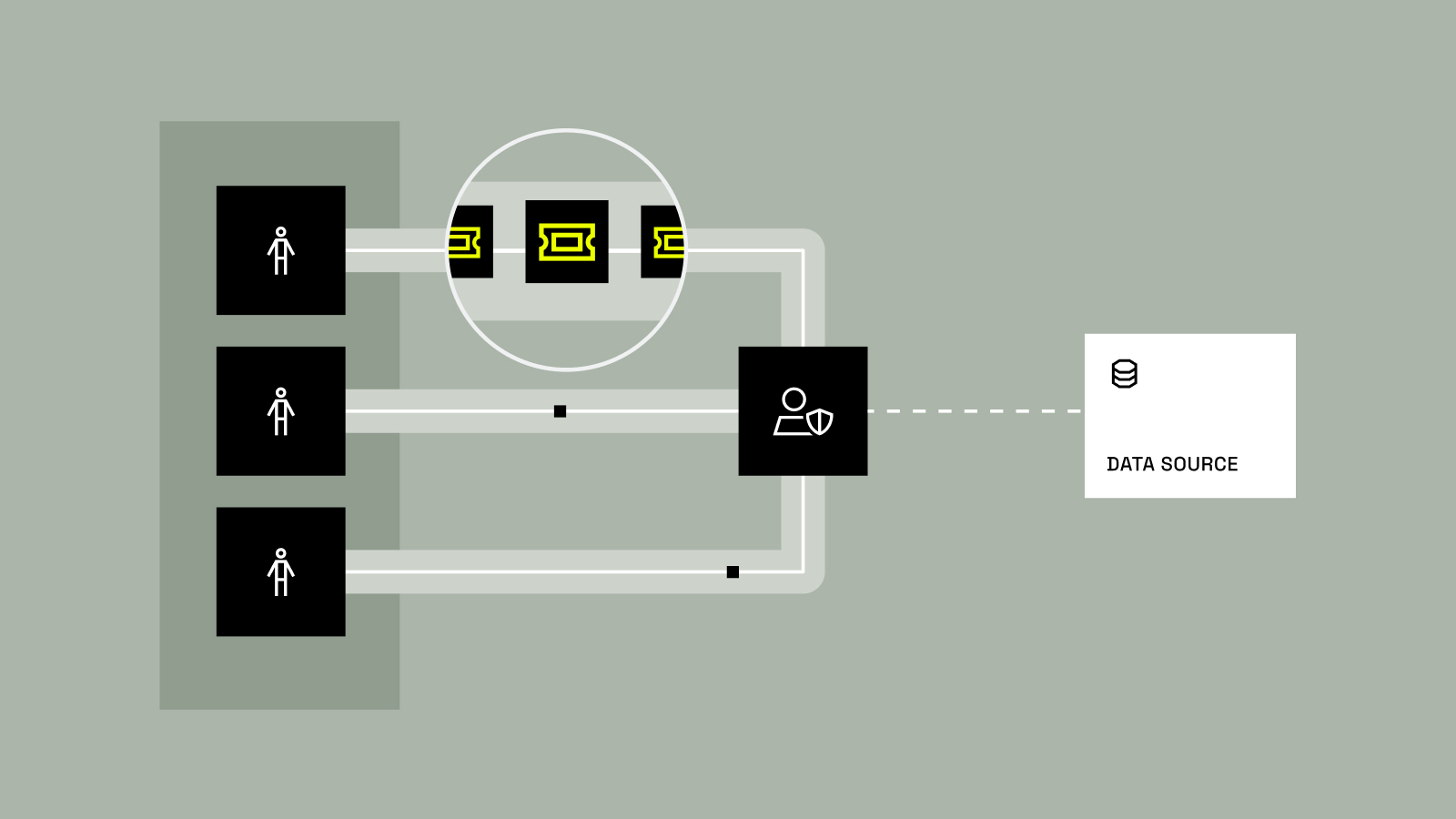
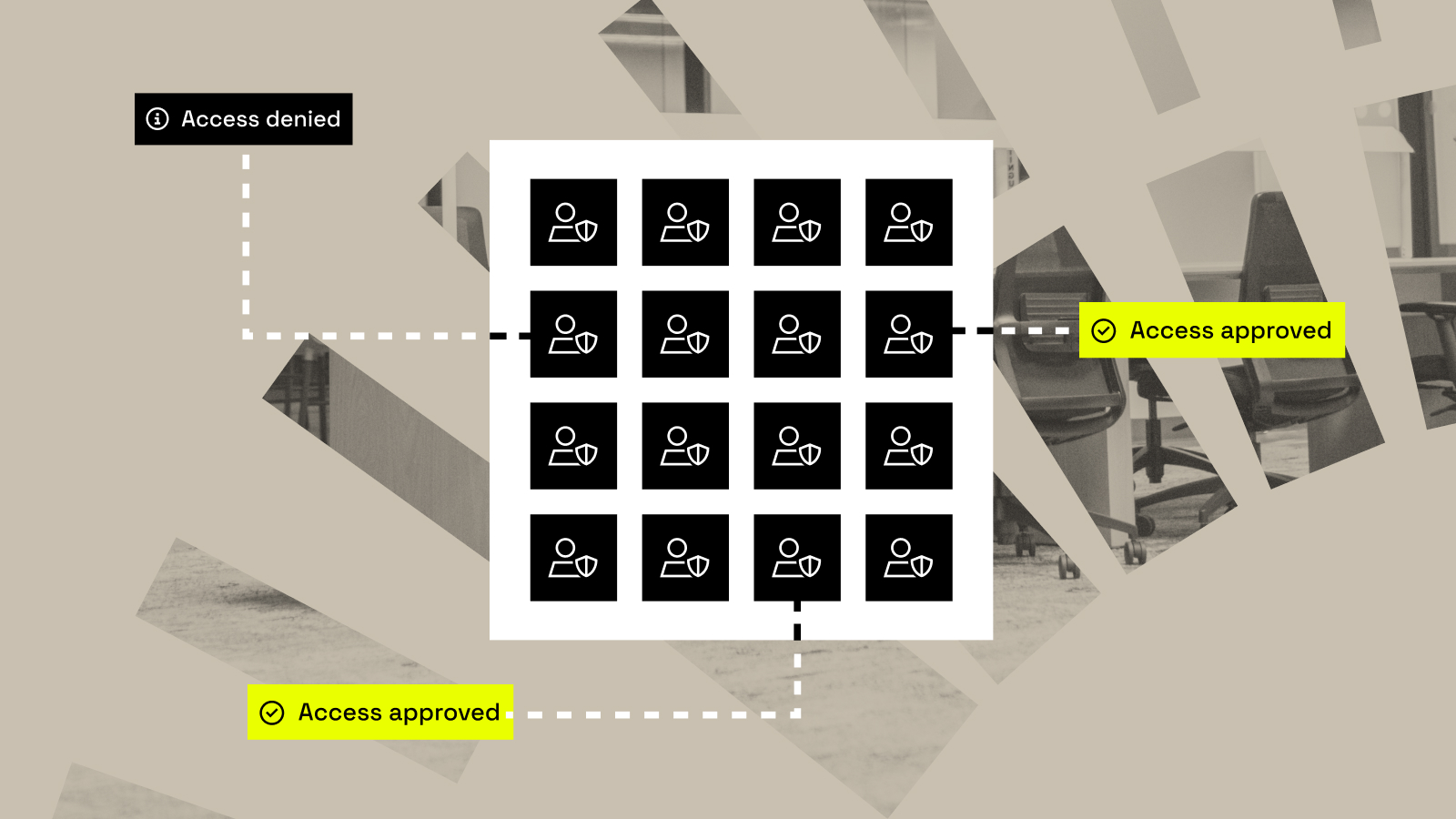
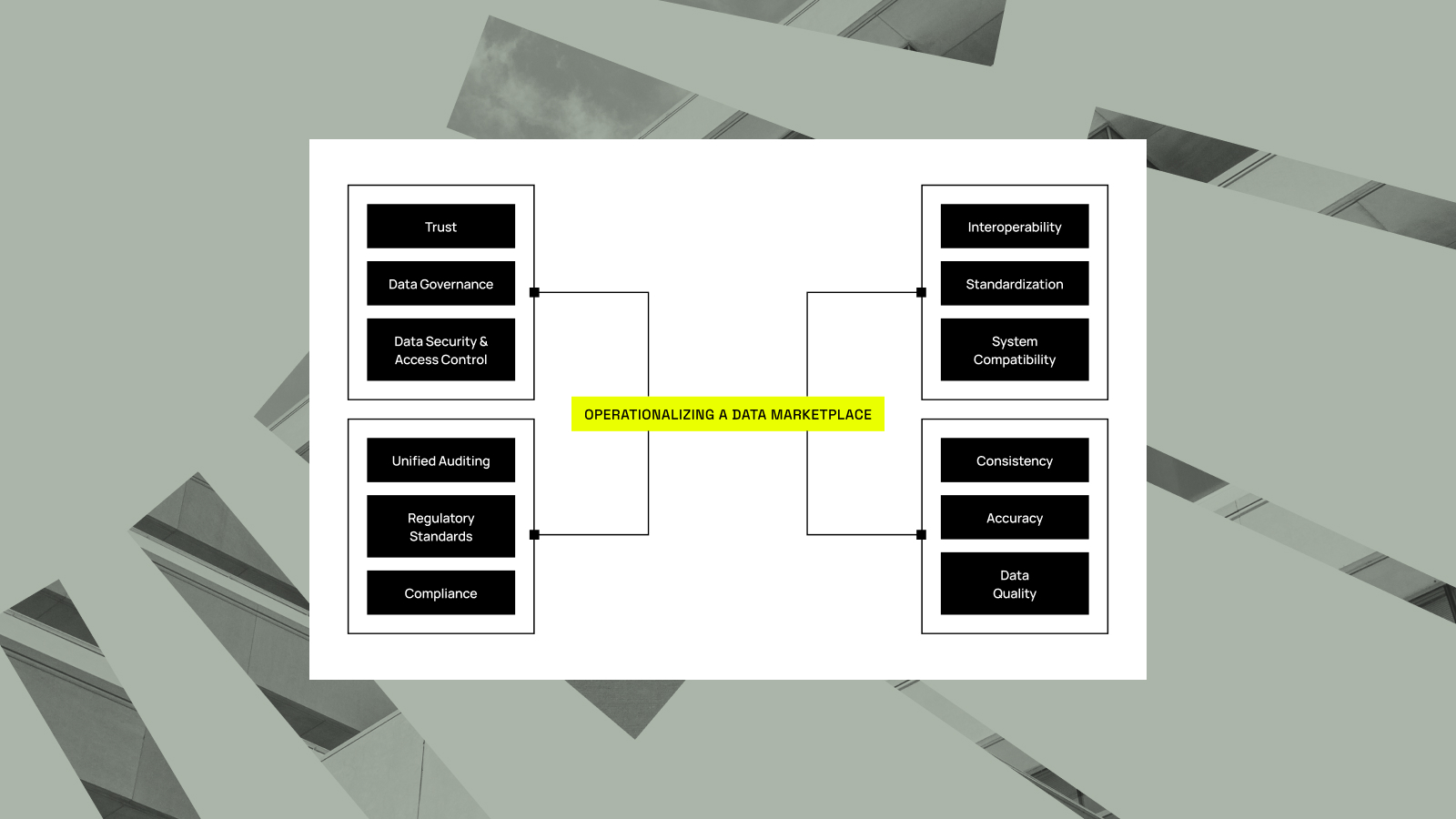
Loading the Elevenlabs Text to Speech AudioNative Player… I’ve been having the same conversation for months now. Whether I’m in Hyderabad, London, or San Francisco, when I ask data leaders “How’s provisioning access to data going?” the response is universal: a groan, followed by “managing tickets is painful.” And it...