Beyond Discovery: Intelligent Data Provisioning Arrives in Catalogs
At Immuta, our mission is simple: Make it easy for people to access the data they need — securely and from anywhere. Today, we help some of the world’s biggest companies do exactly that. Whether it’s separating buy and sell-side data in finance, protecting patient identities in drug trials, or...
Frictionless Data Access Is the New Mandate for Enterprise Data
Companies are pouring billions into cloud data platforms and AI initiatives, but 95% have yet to see an impact on their bottom line. What gives? The problem is that many organizations are missing the mark at the most fundamental level: giving people timely, trusted access to the data they need....
How to Enable Zero Trust Data Operations at the Tactical Edge
In the public sector, and for defense agencies specifically, mission analytics can be the difference between success and failure. Without real-time access to intelligence data, teams on the ground may be unaware of threats, targets, or other critical information required to carry out missions. To meet this growing need, the...
AI-Driven Data Provisioning Is the Future of Pharmaceutical Breakthroughs
In the pharmaceutical industry, speed is everything. The faster you can develop a new drug, test it in a clinical trial, and get it to market, the better the outcomes are for the patients and the business alike. But that all hinges on the ability to access data. Without insights,...
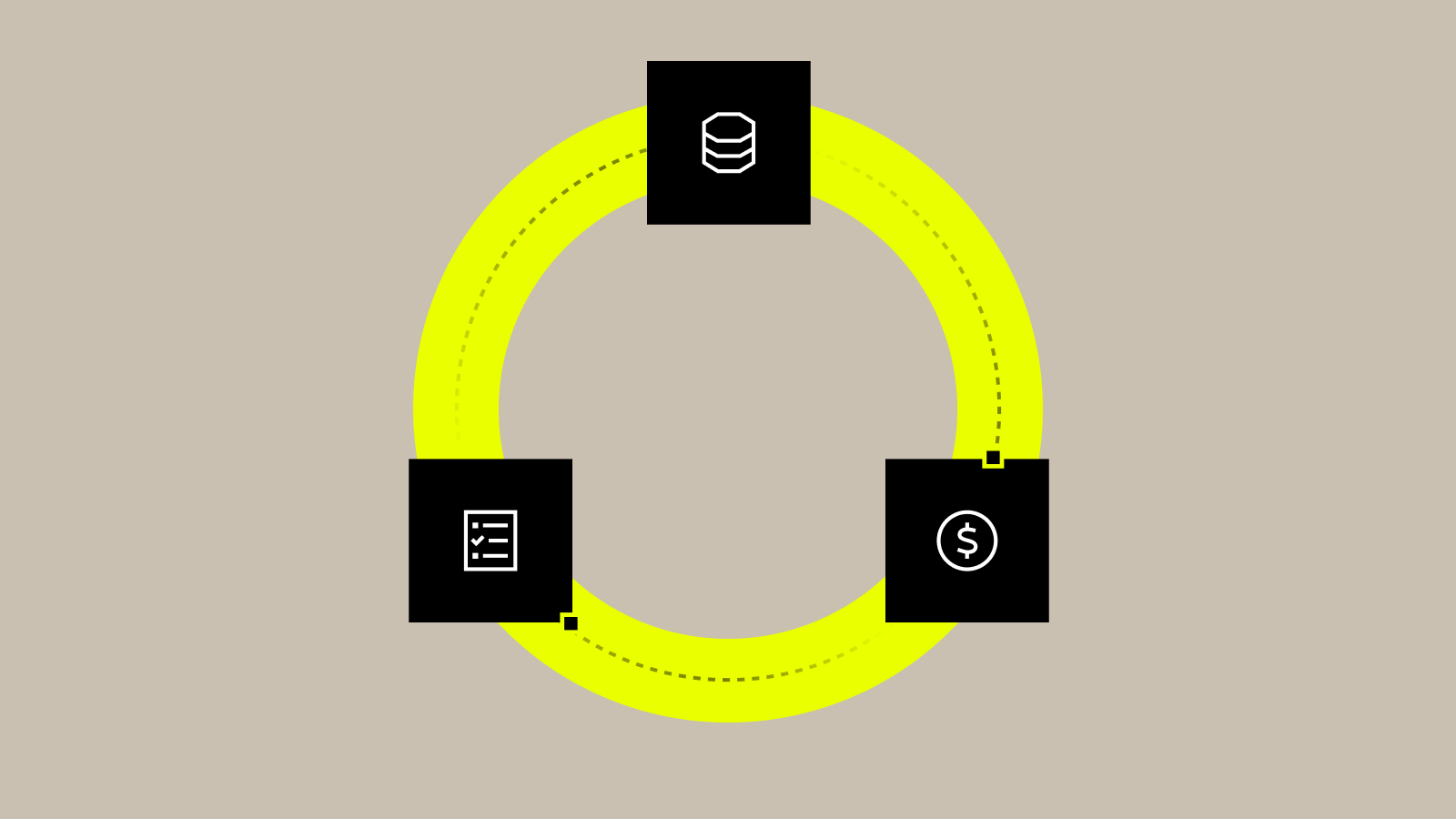
Quantifying the ROI of Data Governance: How to Get Buy-In
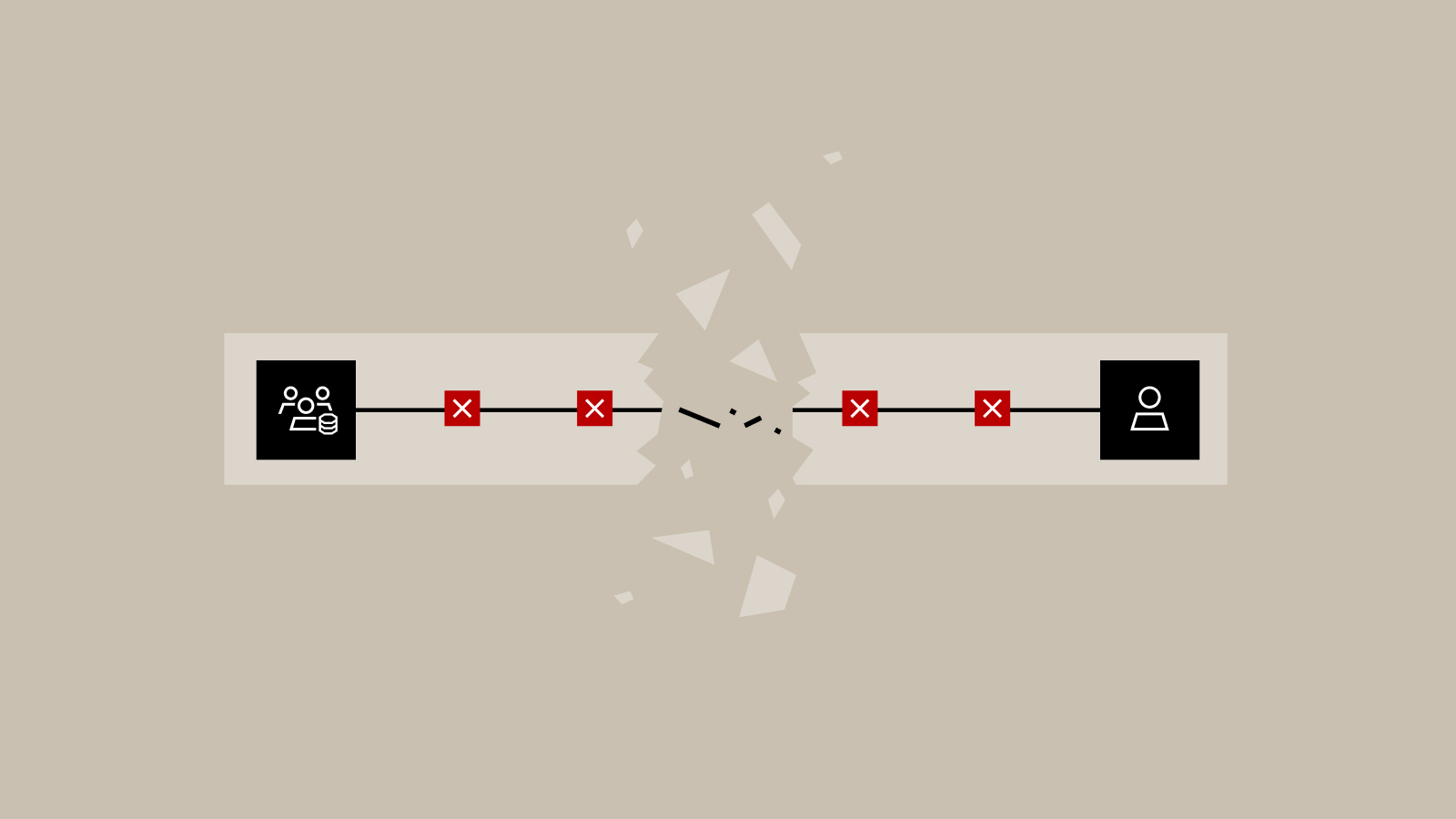
Why Data Provisioning Is the Missing Link for Data Catalogs
Loading the Elevenlabs Text to Speech AudioNative Player… Data catalogs are foundational in the modern data stack, delivering a single, searchable inventory of every dataset an organization owns. From engineers to business analysts, data catalogs give users a centralized knowledge base in which to explore and understand what’s available. But...
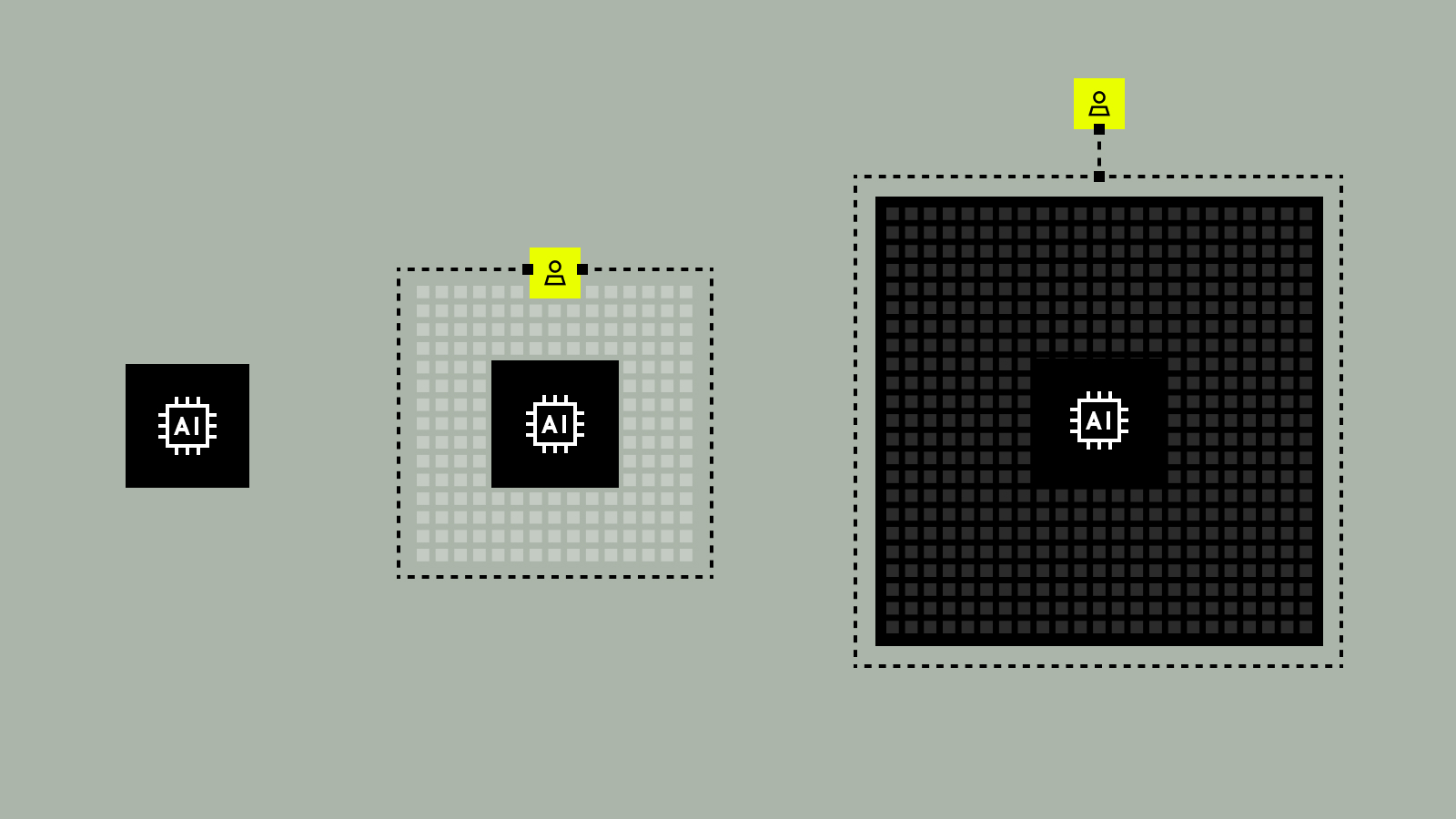
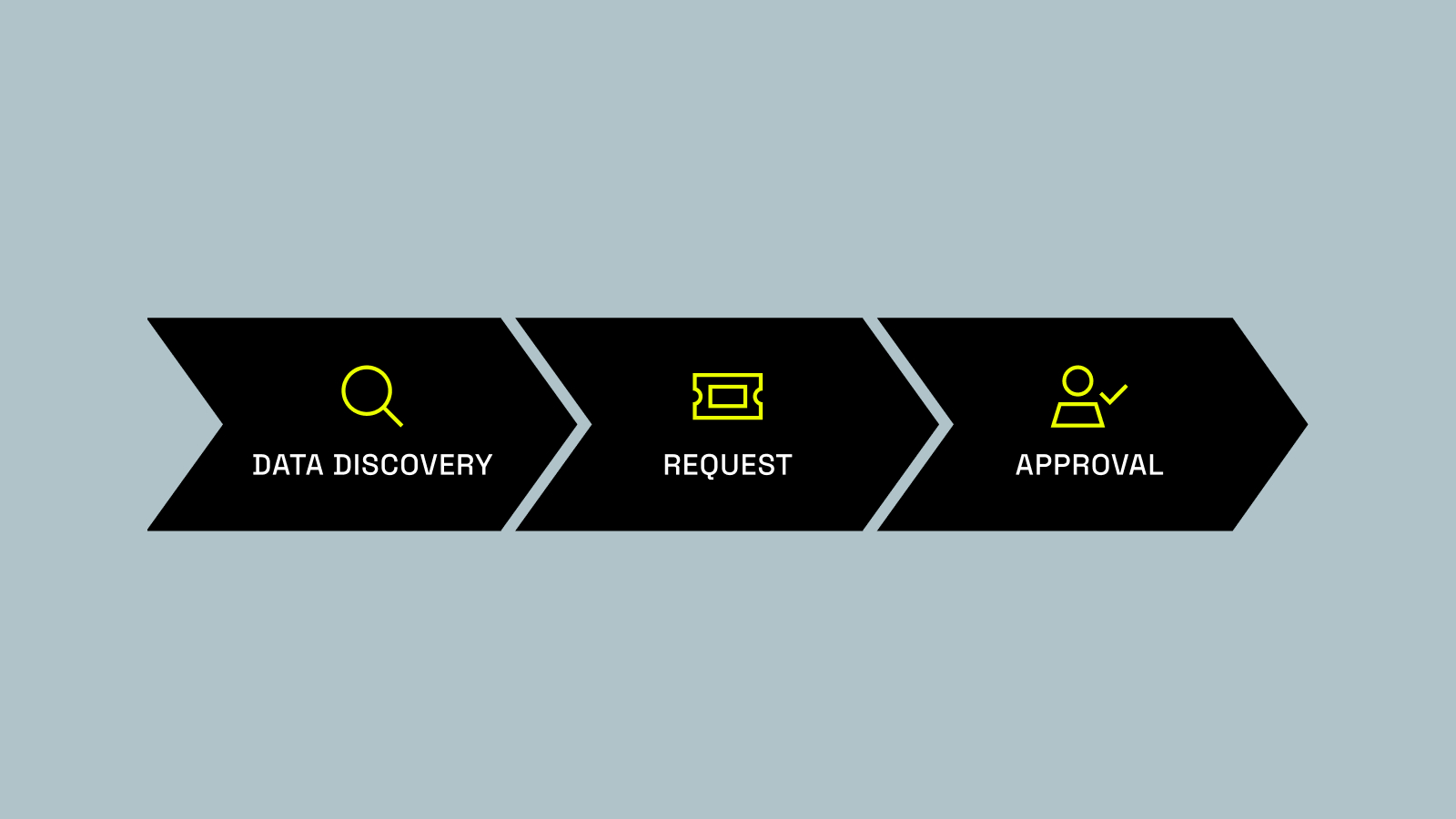
The 3 Phases of AI Implementation
Loading the Elevenlabs Text to Speech AudioNative Player… When I talk to CDOs and data teams – regardless of industry, location, or size – one question keeps coming up: How are other companies implementing Immuta with AI? It’s a natural curiosity. When you hear business leaders and industry analysts talking...

Why AD Groups Are Holding Back Your Governance Goals (And How to Fix It)
For decades, groups and birthright access have been the default for managing enterprise data permissions, operationalized through static Active Directory (AD) groups. This approach promised simplicity: central IT granted employees sweeping access based on role, department, or title, which they bundled into broad groups and applied during onboarding. On the...
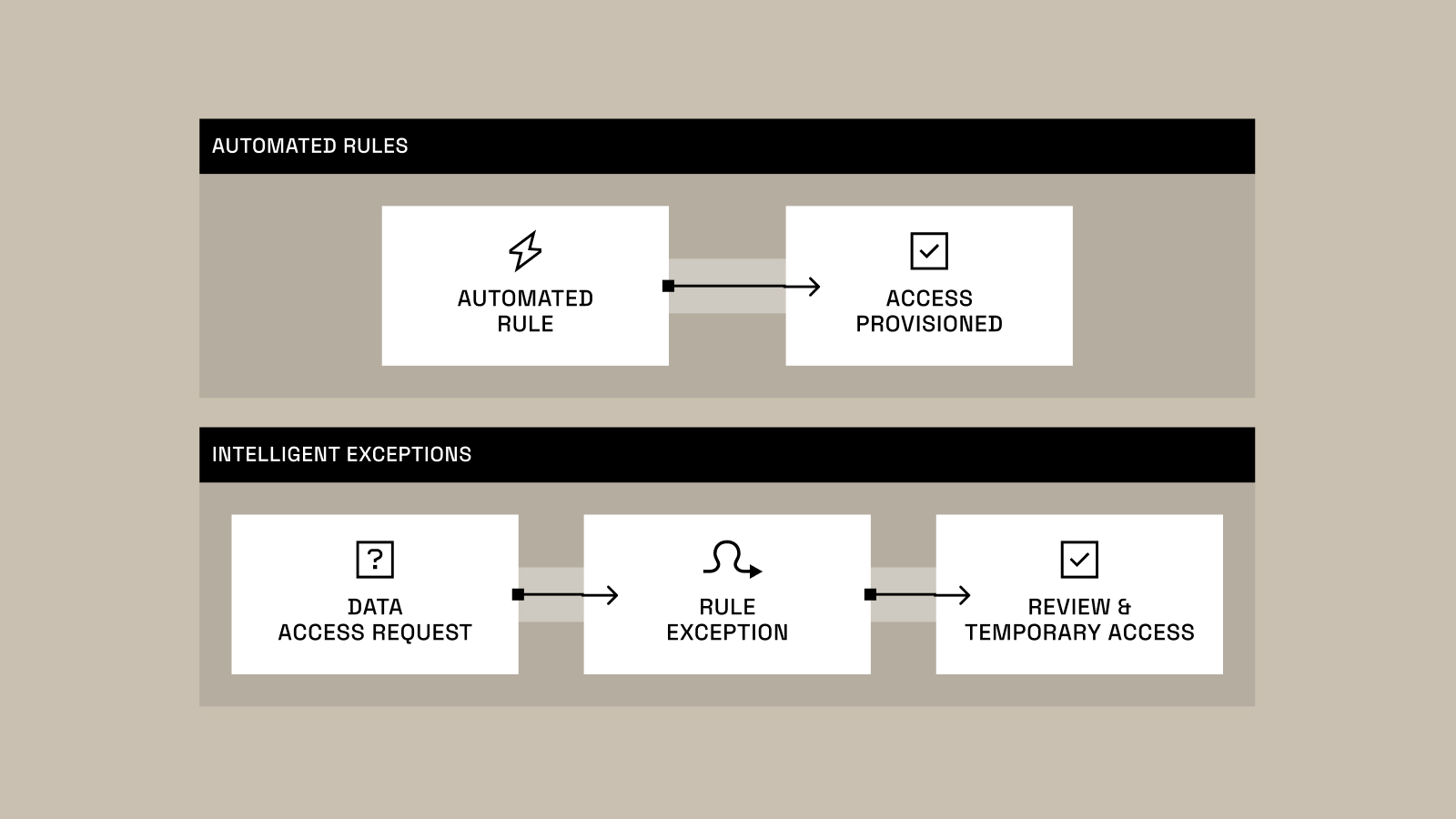
Handling Access Exceptions at Scale: Automated Rules & Intelligent Exceptions
As professionals in the data space, we’ve seen countless organizations struggle with data access, particularly as they grow and scale. From endless ticketing systems to manual approvals that bottleneck innovation, the struggle to balance data utility with robust security has been a persistent challenge. And as AI adoption accelerates, things...
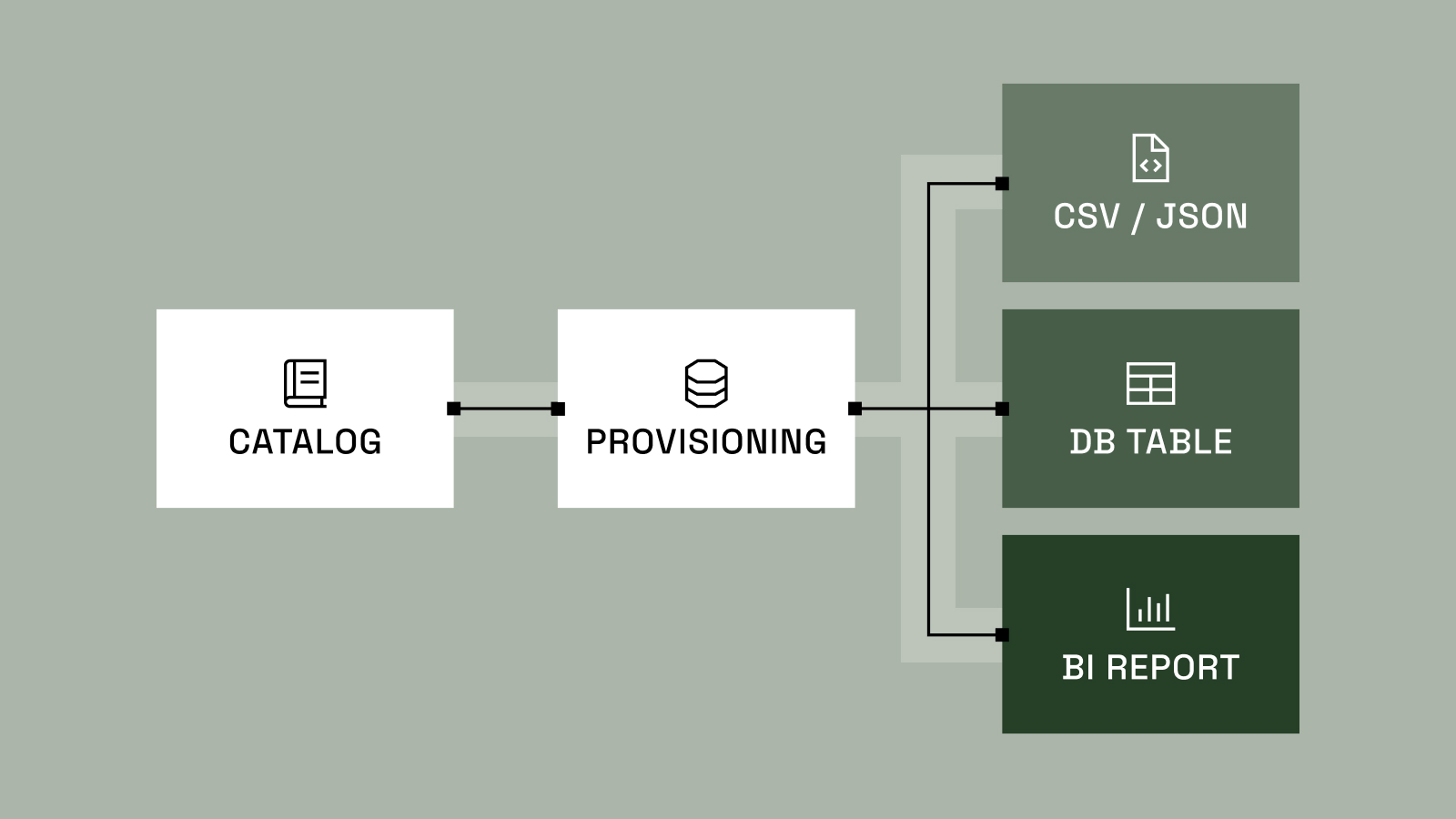
The New Approach to Provisioning Data in the AI Era
Remember when you were in school – your teacher assigned you a report on Monday that was due on Friday. You went to the library, searched for the book you needed, got it stamped by the librarian at the front desk to log that you had it, and received a...
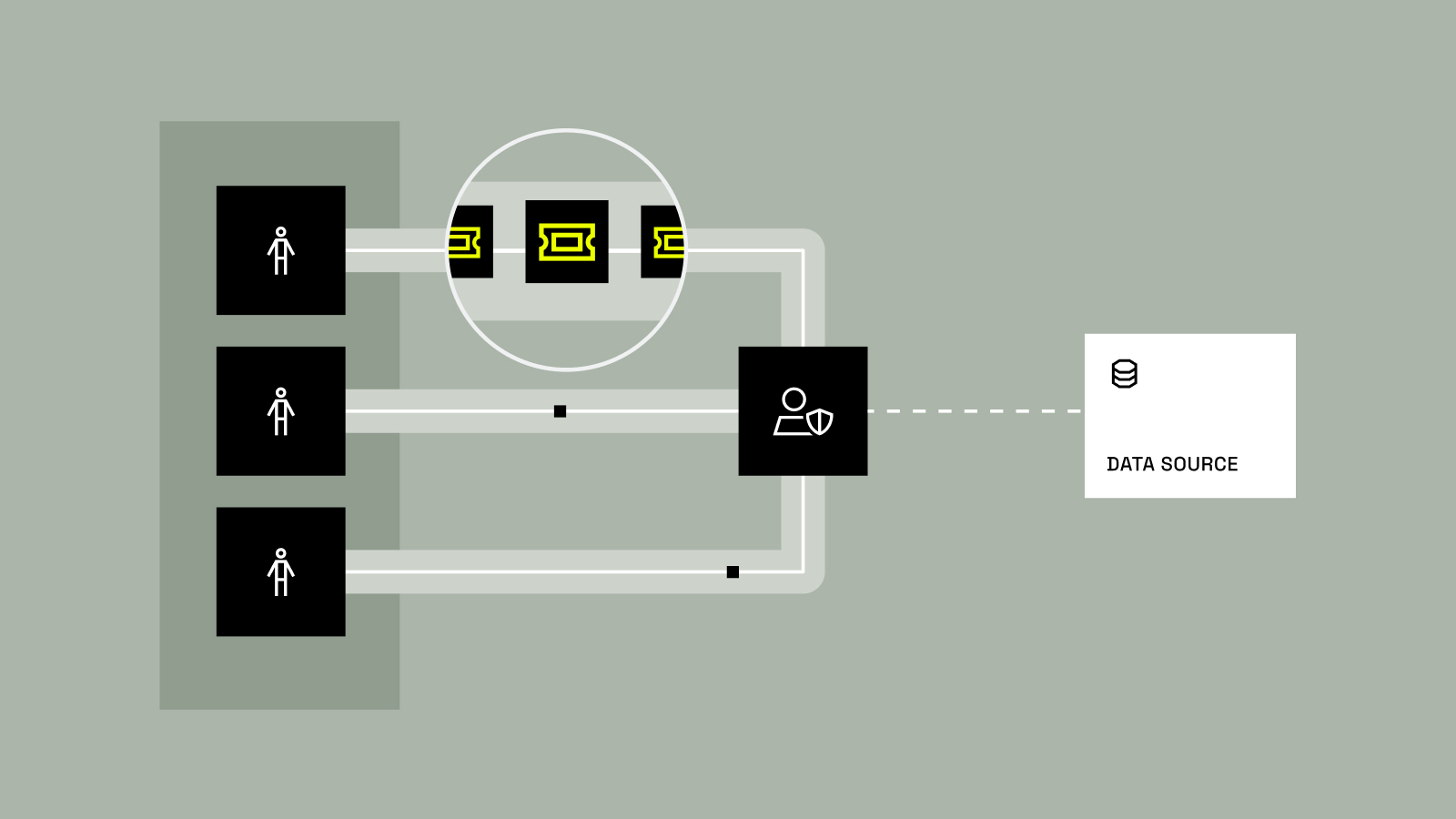
Solving the Data Provisioning Crisis That’s Crushing Enterprises – With AI
Loading the Elevenlabs Text to Speech AudioNative Player… I’ve been having the same conversation for months now. Whether I’m in Hyderabad, London, or San Francisco, when I ask data leaders “How’s provisioning access to data going?” the response is universal: a groan, followed by “managing tickets is painful.” And it...

Data Product Provisioning: The Manual vs. Automated Debate
Despite advances in cloud technology, 64% of data leaders report facing significant challenges provisioning timely and secure data access. Data governors and stewards are caught in the middle of this dilemma, tasked with ensuring that data products are readily accessible and valuable, while also being secure and compliant. Traditional methods...
The Evolving Role of Data Governance Teams — And How to Adapt
When we talk about slow data access, the blame tends to be pinned on two factors: outdated technology and manual data governance processes. The 2025 State of Data Security Report validates that perception: 41% of respondents say that not having the right tools blocks efficient data access and management, while...
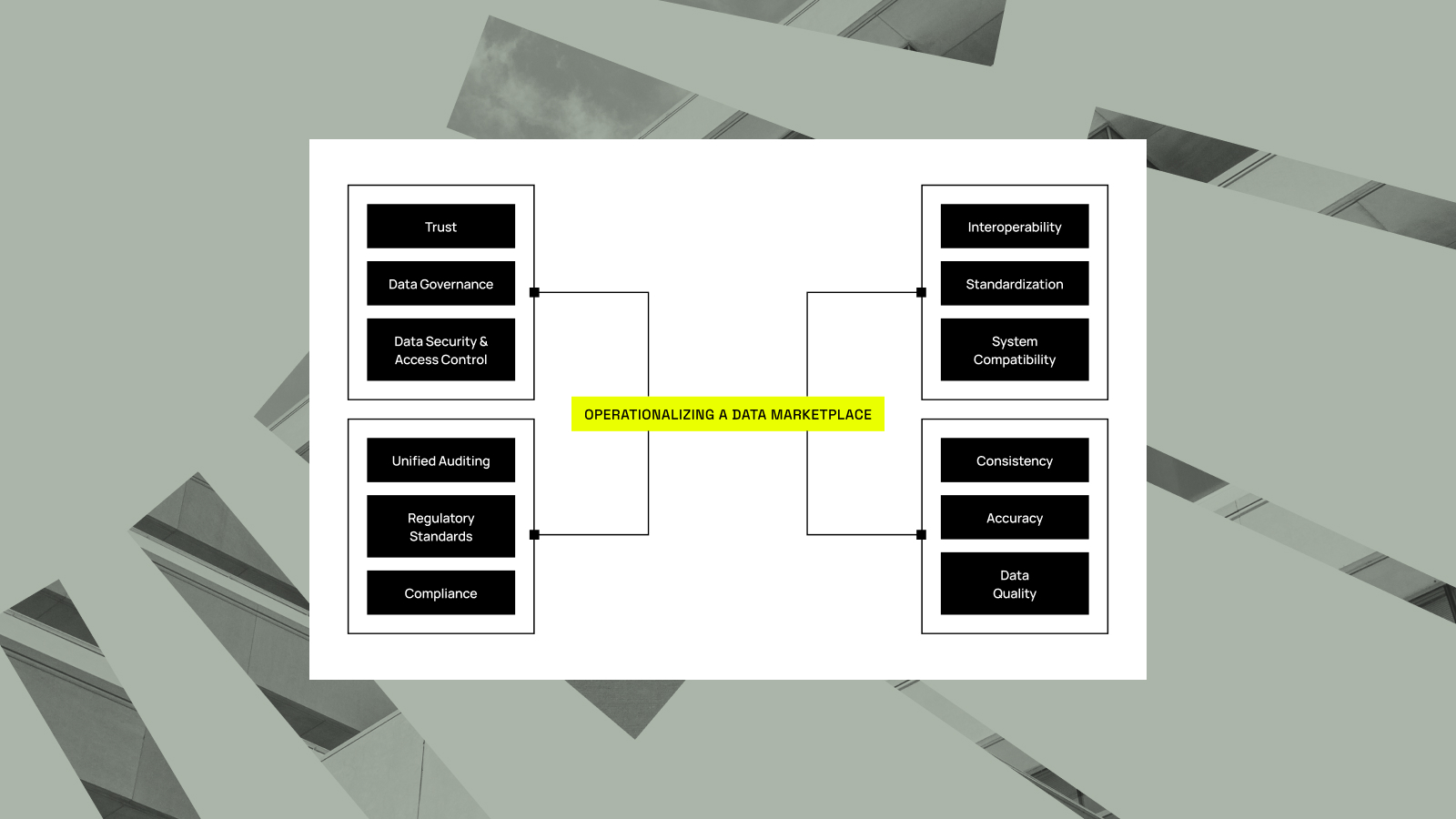
The 5 Stages of Advancing Data Marketplace Maturity
Data powers everything in today’s market, from insights and innovations, to competitive advantages. Without it, organizations struggle to grow, compete, and function efficiently. Yet, for many teams, accessing, managing, and leveraging data effectively remains a significant challenge. Whether you’re a data consumer seeking streamlined access to insights or a data...

Immuta AI: Data Provisioning at the Speed and Scale of AI
Artificial intelligence is more than just a buzzword; it’s a force that’s changing the way we work, learn, and live. In every industry — from healthcare to entertainment — AI is sparking new conversations, debates, and initiatives as organizations race to harness its potential. Case in point: A survey of...

Bridging AI and Data Governance: How the Immuta Marketplace Solution Elevates RAG Systems
Technologies like retrieval-augmented generation (RAG) are transforming how organizations apply AI to tackle real-world challenges. By merging generative AI with curated, real-time data retrieval, RAG systems provide accurate, relevant, and actionable results, without the resources needed to build a custom LLM from scratch. However, the data powering these systems is...

How to Drive Business Value with Data Sharing & Governance

How to Share Insights & Success with Data Marketplaces
The rise of the internal data marketplace When Clive Humby described data as “the new oil” back in 2006, he was mainly talking about the huge strategic value that it can deliver. Two decades on, and his assertion holds true. In that time, though, it’s also become clear there’s a...

Driving Change: Automotive Innovation in the Data & AI Era
Autonomous vehicles From “basic” features like lane assist and self-parking, through to advanced capabilities like sensor fusion and pattern recognition, data is — quite literally — the driving force behind autonomous vehicles. Self-driving cars also generate a great deal of sensitive information, such as location data and driving habits. Ensure...

AI in Automotive, Explained
As topics go, they don’t come much hotter than artificial intelligence (AI). AI isn’t just another buzzword or passing trend. It’s a technology that promises to have a genuinely transformative impact on the automotive industry. From the supply chain to the powertrain, AI promises to revolutionize everything from design and...

Driving Data: How Smart Cars Collect and Put Data to Work
The car isn’t just a car anymore. It’s the center of a dynamic — and ever-expanding — data ecosystem. From design and development through to services and subscriptions, data has become the driving force in automotive today. For manufacturers, that creates challenge and opportunity in equal measure. Extracting the right...

The E-Trade Moment for Data
Before 1992, if you wanted to buy a stock, you’d call your stockbroker to place, buy, or sell orders. The stockbroker would then communicate the order to the trading floor or exchange desk. The process created a barrier of entry for average consumers, and the banks involved leveraged manual, people-driven...
Why Internal Data Marketplace Adoption Is Growing Faster Than Ever

What To Expect Throughout Your Data Governance Implementation
Standing up a data governance framework is a critical step for any organization. According to reporting from Gartner and Immuta, it topped the list of leaders’ priorities – beating out initiatives related to AI and analytics. But as technology evolves, so does the process of implementing an effective, future-proof data...

The 10 Commandments of an Internal Data Marketplace
Like most data initiatives, data marketplaces are meant to deliver value. But unlike those other initiatives, data marketplaces have an edge – they increase the potential of the entire business by clearly defining the roles, rules, and capabilities that lead to success. To truly maximize the value that data marketplaces...

Why a Data Marketplace and Catalog Are Required to Fuel Collaboration and Insights
One of the most consistent challenges that we have seen when working with large global enterprises is a tendency to treat data catalogs and data marketplaces as the same objective, rather than separate ones. Conflating the two may also explain why data and analytical engineering teams, along with business users,...

Unique Data, Unique Solutions: Customizing Sensitive Data Discovery
In the world of data management, not all sensitive data fits neatly into predefined categories. Many organizations deal with unique data types and formats that standard data discovery frameworks fail to recognize. As data protection regulations become more stringent, the ability to identify and manage sensitive data accurately is crucial. However, the...

Navigating Organizational Change When Implementing a Cloud Data Governance Strategy
The adage that “we are a software company” is quickly becoming “we are a data company.” In today’s world, software is only as good as the data within it – and the ability to deploy it. As the wave of organizations leveraging cloud data platforms like Snowflake and Databricks continues to build, enterprises must...

How Immuta Earned AWS Data and Analytics Competency Status
We are thrilled to announce that Immuta has achieved the prestigious AWS Data and Analytics Competency status. This recognition from Amazon Web Services (AWS) highlights our dedication to delivering top-tier data security and analytics solutions for joint customers, and is an exciting next step in our long-standing partnership with AWS. Earning AWS Data and...

Bolstering LLM Security to Protect Against OWASP Top Ten Threats
We’re all witness to the buzz around Generative AI (GenAI). These offerings, which convert user prompts into model-generated text, images, and videos, have permeated our professional and personal lives as they become increasingly accessible. One incredibly prevalent type of GenAI is the Large Language Model (LLM), which includes the likes...

Does Your Business Speak Data? An Argument for Data Literacy
In our super-connected world, data is everywhere, influencing every choice, interaction, and experience we have each day. Simply having data isn’t a bragging right anymore – it’s table stakes. The real game-changer for a modern company is its knack for turning that raw data into a goldmine of insights. Think...
What Major Data Breaches Can Teach Us About Layered Security
Recent data breaches at Ticketmaster and Santander have underscored the critical vulnerabilities that exist in enterprise data security strategies. These haven’t just interrupted operations – they’ve impacted hundreds of millions of customers, eroding trust in well-known and widely used brands. This is particularly pronounced for Ticketmaster, given the company’s recent headlines. Since before Immuta existed,...

How Merck’s Governance Strategy Balances Innovation & Security
Many data teams – especially at large enterprises – fall victim to a difficult paradox: while they generate vast amounts of data across lines of business, actually accessing and using it is incredibly difficult. Take Merck for example, the world’s third largest pharmaceutical company by revenue. Data flowing in from their R&D,...

3 Steps for Countering Bias in AI/ML Data Sets
Advancements in Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing the way we work with data across sectors. By enabling enhanced decision-making and faster operations, these models present us with unparalleled capabilities – but they are not immune to some very human problems. One of the most critical challenges...

Immuta Introduces Multi-Layered Security for RAG-Based GenAI

Combining Data Mesh and Data Fabric for Next-Gen Data Security
While they may be different on a conceptual level, data fabric and data mesh aren’t mutually exclusive concepts. Within the right data strategy, the two frameworks can actually work together, with data fabric providing a unified data access layer for a larger data mesh architecture. The choice of whether it makes sense to leverage...

How to Secure Your Data in the Snowflake Financial Services Data Cloud
The world of financial services never sleeps — and in this always-on industry, delays, mistakes, or indecision can literally cost millions. But speed can’t come at the expense of compliance, which puts data teams in a unique and complex position. Do you grant access to data at the speed of...

What the Power Grid Can Teach Us About Data Sharing
British mathematician Clive Humby is credited with coining the phrase “data is the new oil.” Respectfully, this statement no longer rings true – and data sharing is one of the main reasons why. A lot has changed since 2006, when Humby first made this comparison. To put it into perspective, Twitter launched...
Why Collaboration and Controls are Central to Data Risk Management
We operate in a world of risks. Whenever we get behind the wheel of a car, flip a light switch in our home, or enjoy an alcoholic beverage, we are accepting an inherent level of risk associated with each activity. But this doesn’t stop us from doing them. Similarly, cloud data...

How Vizient Delegates Data Ownership to Optimize Operations
Vizient is the nation’s largest provider-driven healthcare performance improvement company, serving more than 65% of the nation’s acute-care hospitals. The company provides analytics-enabled solutions to improve care quality, as well as spend management. To ensure efficient control of how data is managed and accessed, while also complying with legal, industry, and...

Now is the Time for Risk-Aware Data Security & Access Controls
From artificial intelligence and machine learning advancements, to decentralized cloud storage and analysis, and other novel use cases, we’re seeing data innovations happening before our eyes. At the same time, data breaches and noncompliance penalties are increasingly common and costly, and threats to data will only continue to grow. In...

Enabling Cloud Infrastructure Security for Storage & Compute
Pushes toward self-service data use, advancements in AI, and the demand for real time, granular data insights have led to a surge in unstructured data volumes and usage. Research shows that 90% of new enterprise data is unstructured, and it is growing at three times the rate of structured data. This begs...

Clinical Trials Reimagined: The Impact of Secure Data Sharing on Pharma R&D
Life sciences organizations have traditionally been early adopters of data science and analytics practices, which have revolutionized how they conduct research, develop life-saving therapies, deliver personalized medicine, and optimize their operations. Central to these advances is the ability to share data among healthcare providers, researchers, regulators, and more. Data sharing fosters...

Balancing Collaboration and Compliance with Data Marketplaces
Although we are living in an age of unprecedented data generation, none of it matters if we can’t make that data available for analysis in a secure and timely manner. In order for users to analyze and derive insights from data, it must be discoverable and accessible. Streamlining accessibility has...

Implementing Privacy Controls for Genomics
Genomic data holds significant promise in advancing personalized medicine, streamlining disease treatments, and improving health outcomes. By leveraging individual genetic profiles and biomarkers, genomic data allows researchers to improve treatment accuracy and efficacy. But this promise carries significant privacy risks. The volume and high dimensionality of genetic data introduces a...

Scaling Secure Data Access Management and Use with Immuta Domains
One of the most persistent challenges modern data-driven organizations face is the divide between IT teams and business units. With data ownership largely in one camp and data use in the other, this gap hinders effective data collaboration, resulting in disjointed efforts and missed business opportunities. At the heart of...

Data Leaders’ Top 4 Security Trends for 2024
It’s easy to talk about trends in absolutes. “This new development will affect jobs across every sector,” and “this new platform is going to be everywhere” – these kinds of blanket statements remove nuances that can be incredibly important when discussing trends. Instead, we should focus on questions like “How...

Discover Frameworks: Bridging the Gap Between Regulation & Application
“What data do we have?” Data’s entire life cycle – from collection, to analysis, to insights and business-driving application – begins with this question. Understanding your organization’s data remains critical to effectively using and protecting it, especially as platforms, users, and data sets constantly evolve. But gaining a contextual understanding...

How to Make Data Mesh a Reality: An Implementation Roadmap
We recently conducted an intriguing webinar exploring the data mesh concept, and how it’s transforming the way enterprises decentralize data to enable cross-functional, self-service products tailored to users’ needs. Though appealing for most organizations, executing a data mesh poses real complexities. At phData, we’ve implemented several successful data mesh platforms for our customers, and...

3 Emerging Data Security Laws and What They Mean for You
The past few months have been particularly hectic for lawmakers across the European Union (EU). With Ursula von der Leyen’s leadership of the European Commission set to conclude after the 2024 elections, lawmakers have felt the pressure to advance critical files and policies as quickly as possible. Amid this legal...

Unlocking Education Data Analytics for the Future of Work
It goes without saying that employee engagement is a key indicator of organizational performance – Harvard Business Review reports that having happy, engaged employees increases productivity by 13%, not to mention its impact on retention and culture. Yet, studies show that employees are more dissatisfied and apathetic than before the pandemic. While many different...

The Intersection of Data Security and IAM
As more capabilities become automated as part of cloud services, we find that our customers are reluctant to give up control over data security. The complexity of managing policies and granting access involves a degree of hands-on management, and customers want to own that responsibility. In the Gartner report, Predicts 2024: IAM and Data...

What Is the EU-US Data Privacy Framework & How Should You Plan?
The General Data Protection Regulation (GDPR) is one of the most wide-reaching and stringent data compliance laws and regulations, with penalties for violating its terms reaching 4% of an organization’s prior year worldwide turnover. Although some of its provisions, such as Chapter 5, have fed more debate and litigation than others, it’s...

The “One Policy” Approach to Policy-Based Access Management
In his Lord of the Rings series, J.R.R. Tolkien writes of 19 rings of power that give their bearers wealth, dominion, and control. Of these, the most powerful is the “One Ring,” which affords its bearer control over all other rings and, by extension, the entire world. What do rings have to...

AI Acceptable Use Policy: Where to Start?
Generative artificial intelligence (AI) are prediction algorithms that are able to create any type of content, be it text, code, images, audio, or video – think ChatGPT, Bing Chat, Bard, Stable Diffusion, Midjourney, and DALL-E, for example. With the emergence of generative AI-as-a-Service – which has lowered barriers to entry – generative AI is spreading to most...

4 Simple Steps to Mature Your Data Security Strategy
In today’s digital landscape, safeguarding your data is more important than ever. Whether you’re a data platform owner, a data engineer on a busy team, or just a concerned professional who values an improved data security posture, taking steps to secure your data is crucial. But where do you start?...

Social vs. Technical: Leaders Weigh in on Data Mesh Challenges
Immuta CTO and Co-Founder Steve Touw sat down with Paul Rankin, Head of Data Management Platforms at Roche, and Sanjeev Mohan, Principal at SanjMo, for an in-depth discussion about data mesh architectures. Below is an edited transcript from a portion of their conversation. To listen to the full recording, click here. Steve Touw: This...

SQL: The Forgotten API
Data mesh has become a hot topic as organizations look to foster self-service analytics to make evidence-based decisions. There are plenty of articles discussing data mesh, including Zhamak Dehghani’s original blog post introducing the topic from 2019. To get back to basics, data mesh is a socio-technical approach to creating a decentralized analytical...

Data Mesh Implementation for Highly Regulated Industries
The concept of the data mesh architecture is widely recognized and often sought after by data teams across a variety of industries. Given its range of promising benefits – including enhanced data democratization and business-driving data products – this should come as no surprise. But with the technical, structural, and organizational overhauls required to...

Securing AI Systems: AI Threat Knowledge Bases
Artificial intelligence (AI) systems have recently gained significantly greater visibility and use by the general public. In the next five years, the AI market is expected to grow by 368%, reaching more than $400 billion by 2027. Numerous industries are exploring new ways to monetize AI in the form of AI-as-a-Service...

3 Solution Patterns for Data Security Success
You’ve just adopted a data security solution – congratulations! Now what? As with any new piece of technology, it can be tempting to jump in feet first to solve all your problems. After all, the sooner you achieve ROI, the better – right? Not necessarily. Often, we see customers struggle...

What’s the Worst That Could Happen? A Guide to AI Risks
While generative artificial intelligence (AI), foundation models, and Large Language Models (LLMs) are often described as the future of AI as we know it, their mass adoption is not necessarily straightforward. The emergence of these types of AI models has sparked concerns recently, leading to a series of open letters, enforcement orders (against...

Types of AI and Input Models Explained
ChatGPT is one of the fastest-growing artificial intelligence (AI)-powered apps of all time, but it is just the tip of the generative AI iceberg. The pace of AI’s advancements makes it difficult to keep up with the latest terminology, let alone understand how it may impact your day-to-day responsibilities. In...

How to Assess and Defend Against the Cyber Threat Landscape
According to the United States’ Cybersecurity & Infrastructure Security Agency (CISA), 47% of American adults have had some amount of their personal information exposed by cyber criminals. With the volume of data that today’s organizations collect, store, and leverage on a day-to-day basis, no one wants to be responsible for...

The Pros, Cons, and Real-World Impact Data Democratization
As data is being analyzed in new ways to deliver better insights, organizations across industries are focusing on democratizing its use in order to capitalize on its business-driving capabilities. In fact, one survey found that 90% of data professionals are prioritizing data democratization at their companies. This sentiment is also present in...

What is Sensitive Data and How Should I Protect It?
If you’ve done any work with data, you’ve likely heard the term “sensitive data.” Data compliance regulations like the GDPR, HIPAA, CCPA, and more make repeated mentions of “sensitive personal data” and “sensitive personal information,” and many privacy statements include similar language. A quick search of the term “sensitive data” returns more...

How to Mitigate Risk by Mastering Cloud Storage Security
The volume of cloud data is increasing at an exponential rate. But with this growth comes an increased attack surface, heightening the risk of dangerous data breaches or leaks. To support the operations of modern businesses and agencies across the world, data resources require storage that can remain secure at...

Data Mesh vs. Data Fabric: What’s the Difference?
When two different concepts sound or act alike, it can be easy to conflate them. We see this in everyday life: jelly vs. jam, weather vs. climate, latitude vs. longitude, concrete vs. cement, the list goes on. In the ever-expanding world of data jargon, this kind of problem can easily...

How Immuta’s ISO 27001/27701 Compliance is Enhancing Data Security
As the world becomes increasingly digital, data security has become a critical concern for businesses of all sizes. Threats to data are evolving as technology and bad actors become more sophisticated, which makes the challenge of protecting sensitive information that much more complicated. Ensuring that data protection processes and policies...

Why Tech Companies Should Care About Healthcare Data Breaches
Health data is one of the most valuable assets organizations in the healthcare and life sciences industry can possess. It’s also one of the most vulnerable. Over the years, legal steps have been taken to protect healthcare data security and patient privacy. The Health Insurance Portability and Accountability Act (HIPAA), passed by...
Forrester TEI Study Shows How Immuta Can Drive 175% ROI Over 3 Years
Forrester’s new Total Economic Impact™ (TEI) study provides a detailed financial model based on interviews with six Immuta customers in order to assess the ROI of the Immuta Data Security Platform. The study concludes that Immuta can provide benefits totaling $6.08M, an ROI of 175% over three years, and a payback period...
Moving from Legacy BI Extracts to Modern Data Security & Engineering
Before we can talk about modernizing from a legacy Business Intelligence (BI) extract, we need to answer the questions: why are they used? And what are they? The “why” behind extracts boils down to improved query performance on published dashboards. You can see more details about the “why” for data extracts in...

Scaling Identity Management in Healthcare
The average hospital has seen a 90% turnover of its workforce in the last five years, and 83% of RN staff. Nurses are not just protesting about their inability to deliver great care – they are leaving the healthcare field altogether. And they’re not the only ones. From the doctors to those...

Why Data Breach Detection is Crucial for Data Security
When a data breach occurs, time is of the essence. On one level, modern compliance laws and regulations have set standards for the window of reporting data breaches, often requiring organizations to do so within 72 hours to avoid penalization. But monetary and legal penalties are not the most important outcomes of...

Survey Reveals 5 Insights for Implementing Zero Trust
The concept of Zero Trust is not new, but it is gaining traction as data security becomes more scrutinized. Also referred to as “perimeter-less security,” Zero Trust has traditionally focused on employing network-centric tools that enable automated access controls, network microsegmentation, and continuous monitoring of connected devices. Following a 2021 Zero Trust executive order, government...

The Next Generation of CCPA Compliance Requirements
The 2020 elections not only saw record turnout, but also ushered in a suite of new laws and lawmakers. Voters in California had a dozen propositions on the ballot, but one that has far reaching implications for citizens and organizations alike is Proposition 24, the California Privacy Rights Act (CPRA) — or...

The 3 Most Common Data Engineering Challenges
Today’s data engineering teams face various challenges wrangling massive volumes of data, dispersed stakeholders with competing priorities, and distributed data architectures. But of all these variables, which is the most taxing? In this blog, we’ll delve into the most common data engineering challenges as reported by 600 data engineers, and how...

What Is Privacy Engineering – And Do You Need It?
Do you have complete confidence in your organization’s privacy law compliance? If your answer is no, you’re in the majority. According to the International Association of Privacy Professionals (IAPP), only 20% of respondents report being fully confident in their company’s approach to data privacy compliance. But data privacy concerns aren’t subsiding anytime soon...

3 Key Obstacles of Military Data Ops and What They Indicate
There are many lessons that I learned throughout my civilian and military careers, but one that continues to hold true is that obstacles to accessing the data national and strategic analysts need are not caused by a lack of reporting in the field. Rather, it is the technical burdens, lack...

What is Data Access Management?

How to Harness the Power of The Modern Data Stack
For Dave DeWalt, Founder and Managing Director of advisory firm (and Immuta investor) NightDragon, the modern data stack–like dragons–has a compelling dual nature. Balancing power with danger, both evolving data stacks and dragons contain immense potential strength that can (quite literally) go up in flames if not managed properly. DeWalt, John Cordo,...

The Data Privacy Regulation Roundup: What Data Teams Need to Know
When the General Data Protection Regulation (GDPR) entered into force, US privacy law was still in its infancy. Though enforced by the European Union (EU), the GDPR had wide-ranging implications for organizations well beyond Europe. And though it has become the regulatory standard in data privacy since it became applicable...

Redefining Data Sharing for Financial Services
As business continues to shift to increasingly digital environments, the aggregation and sharing of financial data is predicted to have a staggering impact on the global economic future. According to research by McKinsey, “economies that embrace data sharing for finance could see GDP gains of between 1 and 5 percent by...

What is Policy-as-Code and Why is it Important?
In the cloud computing era, ensuring data policy is co-created with data is essential. Historically, data access and security policies were an afterthought, leading to sub-optimal implementations. These implementations give rise to confusion, data leaks, and unsustainable maintenance burdens. In order to be effective, organizations need to separate policy from cloud platforms....

Implementing a Data Security Platform for Cloud Storage Security
As data storage and analysis continue to migrate from on-premises frameworks to those based in the cloud, the market for cloud storage and data security platforms (DSPs) has expanded. In fact, the global cloud security market is projected to grow from $29.3 billion in 2021 to $106 billion by 2029. This highlights...

What Types of Data Controls Are There?
Data controls refer to the tactics, policies, and procedures that organizations use to meet their data governance and data management objectives. Put another way, they are the rules and systems that businesses rely on to ensure that only authorized users can access their data, ensuring its security and integrity. Data...

Data Masking vs. Tokenization: What’s the Difference?
As cloud technology has become more advanced, data teams are better able to mitigate the risk of unauthorized access. In fact, the array of choices regarding how to protect data at times makes it confusing to know which is right for your organization’s data. When you’re trying to strike a...

Demystifying Data Security and Privacy in the Digital Age
As data evolves, so does the threat landscape. Facing the possibilities of targeted breaches from external players, risky or negligent activity from insiders, and mounting pressure from the informed public, organizations need to be more intentional than ever with how they protect their data. At the same time, both data...
Resilient, Agile, and Future-Ready: A Roundtable on the Modern Data Stack
The modern data stack bears the immense responsibility of storing, protecting, analyzing, and operationalizing a resource that is constantly in flux. As data continues to increase and evolve, these tools need to make sure it is both being used effectively and kept safe from leaks. This issue and potential solutions...

How to Comply with the Zero Trust Executive Order
Since the White House released its Executive Order (EO) on Improving the Nation’s Cybersecurity in 2021, federal agencies have begun developing long-term zero trust security architectures across their networks while also adopting near-term goals. Officials from the Office of Management and Budget (OMB), the Cybersecurity and Infrastructure Security Agency (CISA), and the White House’s...

What Is Data Masking?
What Is Data Masking? Why Do I Need Data Masking? What Are Some Data Masking Techniques? When Do I Need Data Masking? Top Use Cases How Do I Apply Dynamic Data Masking?

The Costs of Cloud-Based Access Control: DIY vs. Automated
It’s no surprise that nearly 90% of organizations rely on a multi-cloud strategy to get value from their data. Yet, despite budgets for data management solutions continuing to increase, 57% of data leaders say that “their tools and tech definitely need improvement.” This may indicate a lack of cohesion across cloud platforms, but it...

Industry Leaders Share Perspectives on the State of Cloud Adoption
With the world of data analytics and governance constantly changing, it is critical for organizations to stay on the cutting edge. The sharing of ideas between innovators and industry leaders help provide a glimpse into the dynamic core of this field, highlighting the trends central to staying competitive both today...

Modernizing From an RBAC to ABAC Model: Is It Hard?
The good news is no. The better news is you are already 90% of the way there and probably don’t even know it!

Data Privacy Technology Is No Longer Optional – Here’s Why

How to Put Zero Trust Principles to Work for National Security
It is something along the lines of common wisdom to describe cybersecurity as one of the biggest strategic challenges confronting the United States. And that challenge is growing in scope; In 2023, US federal agencies experienced a 5% increase in cybersecurity incidents — totaling over 32,000 — compared to the...

The Top 3 Data Supply Chain Challenges – And Their Business Impacts
Increasing demand for data and its evolving uses – particularly personal and sensitive data – are turning traditional data supply chains upside down. Today’s environment necessitates real-time data access to drive decision-making, which in turn requires a continuous, efficient flow of data throughout organizations. It’s clear why manual processes and...

What Is a Data Mesh?
A data mesh is an increasingly popular data architecture framework that moves away from the monolithic approach of data warehouses and data lakes in favor of a more decentralized method of cloud data management. This approach distributes data ownership to individual business domains, so that data access and management decisions are context-aware. As...

What is a Data Supply Chain?
We’re all familiar with supply chains in the realm of manufacturing. Well, the same concept applies to data management. In data management, there are data supply chains that involve raw inputs from source data systems that go through a number of processing steps and emerge at the end as a...

What is Data Orchestration?
Data orchestration is the process of bringing together data from various storage locations, combining it in a coherent form, and then making it available for use by an organization’s data analysis and data management tools. This process is usually software-driven, connecting multiple storage systems and allowing your data analysis platforms...

The Evolution of the Modern Cloud Data Warehouse
Someone starting a small business – think custom t-shirts, candlemaking, etc. – could probably operate out of their home, keeping their basic supplies and inventory in a spare room, closet, or garage. If their business were to take off and experience exponential growth, however, this type of operation would quickly...

Data Intelligence vs. Data Analytics
The terms ‘data intelligence’ and ‘data analytics’ may as well be enshrined in marble for any modern business looking to capitalize on the power of information. But does your business have a handle on what data intelligence and data analytics are, and more importantly, what they mean for your company?...

Immuta vs. Ranger: Research Comparison Finds Immuta’s ABAC Reduces Policy Burden by 75x
The role-based access control versus attribute-based access control debate has been going on for decades. Now, as organizations move away from on-prem and Hadoop-era technologies in favor of modern, cloud-based data environments, the differences between the two security approaches are coming into sharper view. A new study from GigaOm comparing the two approaches head-to-head,...

The Top 5 Barriers to Data Sharing and How to Overcome Them
Technology has made our world increasingly interconnected and interdependent, and as a result, the need to share data to remain competitive is more important than ever. Yet, despite the competitive advantages associated with data sharing, many organizations still treat it strictly as a data function instead of a business priority. According...

SQL Is Your Data Mesh API

Data Lake Governance: What Is It and Do You Need It?
Data lakes have become essential tools for businesses in the era of Big Data. But keeping those data lakes secure has never been more important as cyberthreats are constantly on the rise. Here’s everything you need to know about data lake security and how Immuta can be an essential partner...

Why Your Data Governance Strategy Is Failing (And How to Fix It)
Loading the Elevenlabs Text to Speech AudioNative Player… At-a-glance: Data governance strategies typically fail due to manual processes and legacy tools, inability to scale, data classification issues, silos and fragmentation, reactive approaches, lack of clear KPIs and executive buy-in, and failure to adapt to AI. By embracing automation, decentralizing data...

How The Center for New Data Saved $1 Million with Immuta
By the time COVID-19 was classified as a pandemic, it was already spreading like wildfire. As healthcare professionals, scientists, and federal agencies tried to understand the nature of the virus and implement appropriate mitigation measures and public health guidelines, it was quickly seeping into all corners of the globe. As...

What is Data Governance? Everything You Need to Know
Organizations are increasingly recognizing their data as a valuable asset that can significantly shape and enhance business outcomes. As organizations continue to navigate digital transformation and the inevitable growth of big data, effective data governance frameworks have become essential to maximizing data’s value throughout its entire lifecycle. In this guide, we’re taking...

Role-Based Access Control vs. Attribute-Based Access Control
The terms role-based access control and attribute-based access control are well known, but not necessarily well understood — or well defined, for that matter. If attribute-based access control includes user roles, then what is role-based access control? Where is the line drawn? Fundamentally, these data access control terms — role-based access control and attribute-based access control...

What is a Data Catalog? 5 Features of a Modern Data Catalog
Imagine going to a library in search of a specific book with a piece of information needed to finish an assignment. Did we mention you’re on a deadline? Good luck. This example may seem extreme, but for organizations that don’t have a data catalog, it’s not unfathomable. In either scenario,...

A Call for a Risk-Based Assessment of Anonymization Approaches
Why it’s time to reexamine the binary dichotomy between personal and aggregate data, and what aggregation, synthesisation and anonymisation mean for the future of data privacy. Privacy-enhancing technologies are typically used to transform data to enable sharing of private data with third parties. However, not all techniques reduce re-identification risks;...