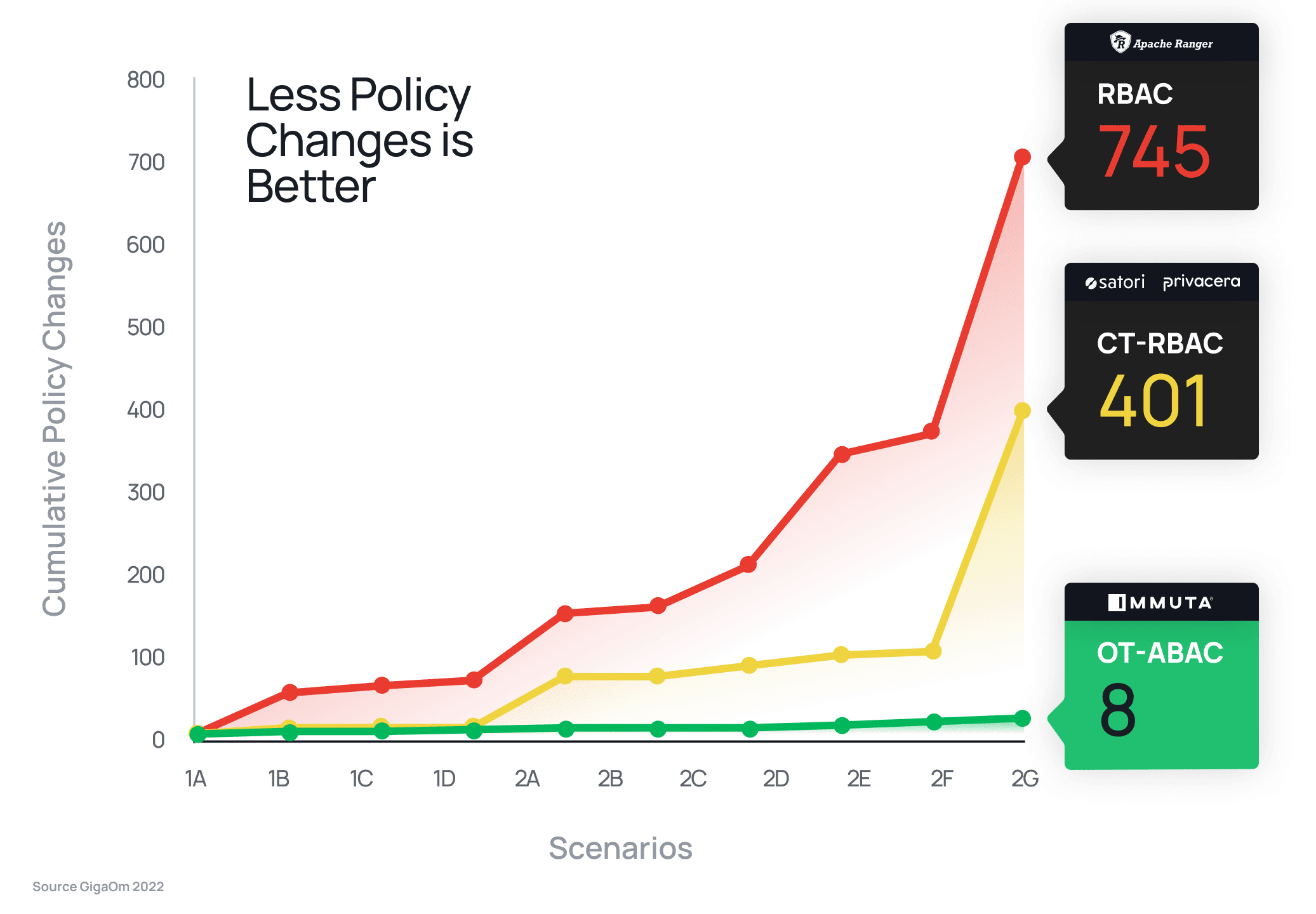
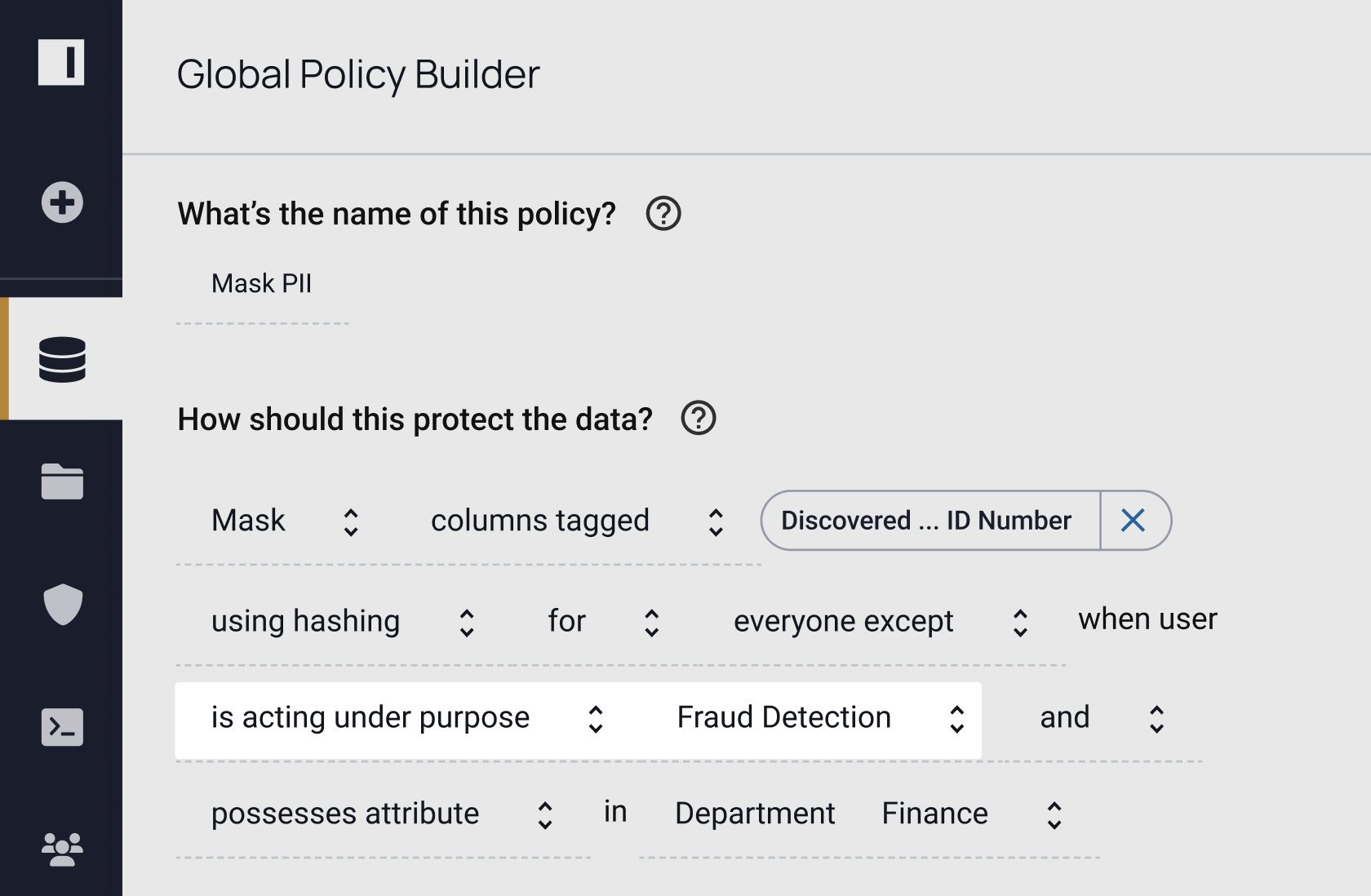
"ABAC simplifies managing the data sets that you're building up. It means we don't have to proliferate our dbt projects and models quite so much, and it can be a lot more flexible over time."
Covering the Full Data Security Spectrum
Attribute-based access control is an integral part of data security. But you need to know what data you have before you can write the appropriate policies, and you need a way to ensure those policies are working as intended. Immuta helps you easily do both – without sacrificing speed or utility.