“Because we don’t have to worry about the problems Immuta is solving, we move a lot faster in trying to solve the problems that are inherent to large mountains of data sitting in one place. ”
What Is Data Access Control?
Data access control refers to permitting or restricting the ability to view, access, or utilize data within a specific system or database. It is a fundamental aspect of data security because it helps ensure that only authorized users are able to access and use data for permitted purposes.
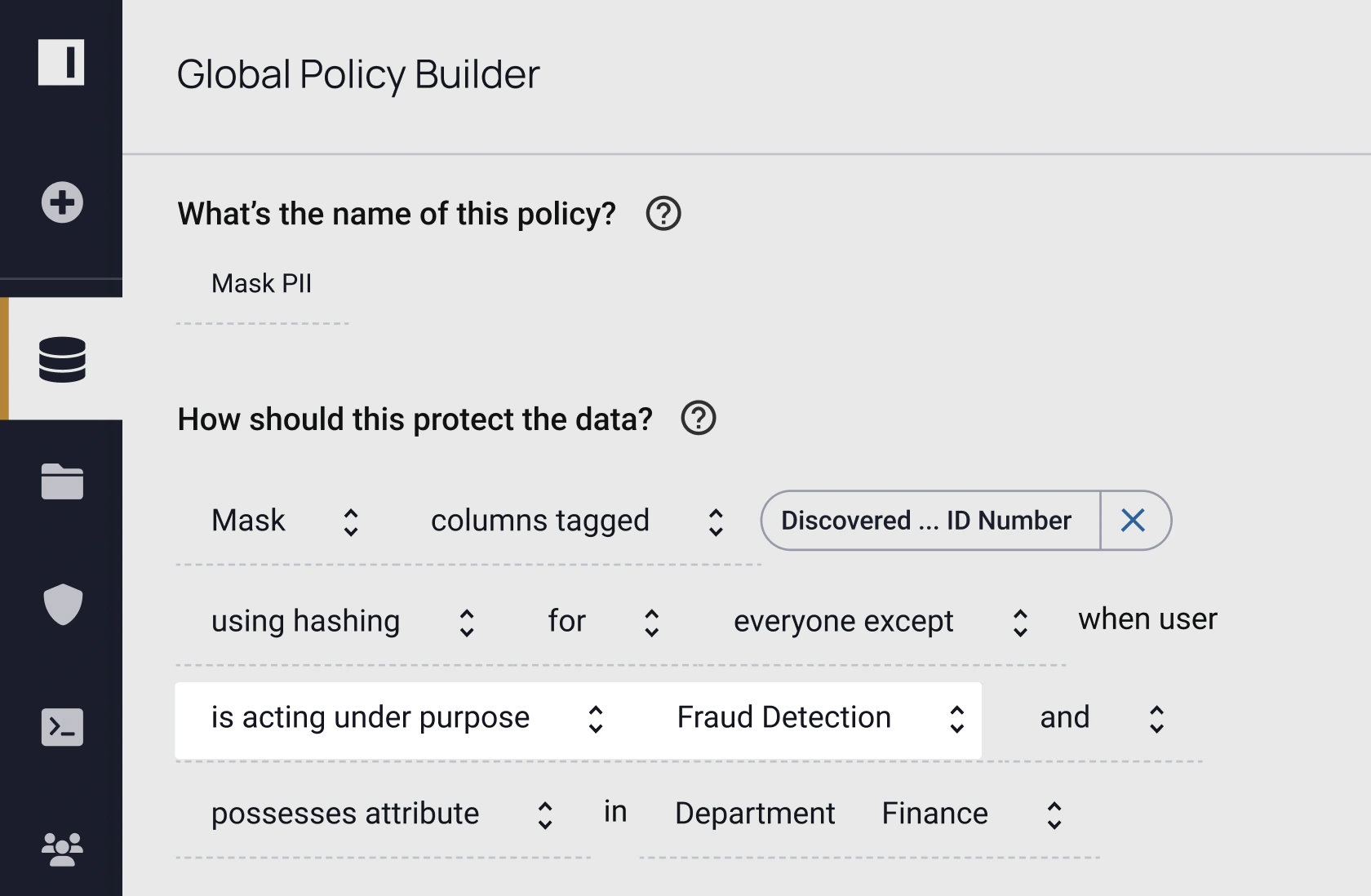
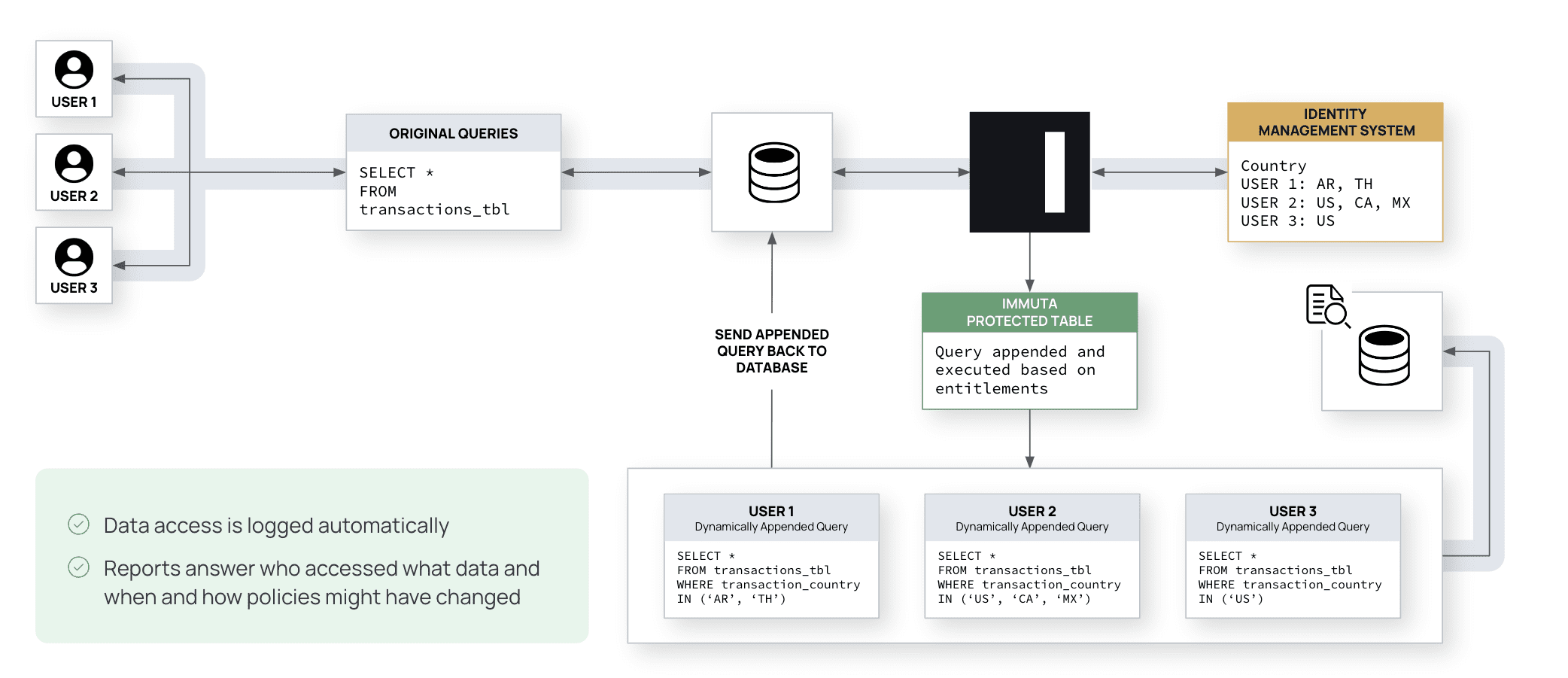
Data access control implementation starts with discovering and classifying sensitive data, then building data policies to enforce access authorization.
The Data Access Control Challenge
The exponential growth of data volumes, users, and regulatory requirements is preventing many organizations from achieving value from their cloud investments. Organizations are faced with a choice between halting progress to ensure data use is secure and compliant, or leaving it completely exposed.
Legacy approaches to data access control are simply no longer feasible. Static, role-based controls quickly lead to role explosion, requiring data teams to manually manage hundreds or thousands of user roles. Homegrown or platform-native controls pose similar challenges. Based on customer evidence and published research, this data access dilemma can cost hundreds of thousands of dollars in lost productivity, and raises the potential for sensitive data to slip through the cracks.