Data Security Posture Management
Data security has become a critical concern for organizations of all sizes due to the increasing amount of data being generated, shared, and stored across hybrid, multi-cloud environments. The exponential growth of sensitive data, coupled with the rise in cyber threats and regulatory requirements, has compelled organizations to pursue and adopt a robust data security posture management (DSPM) strategy to address growing data security and privacy risks.
Data Security Posture Management (DSPM) is a newer category of solutions aimed at proactively identifying, assessing, monitoring, and mitigating data security and privacy risks. It encompasses the implementation of tools and processes to protect sensitive data, detect vulnerabilities, and ensure compliance with data protection regulations. It also helps organizations gain visibility into their data landscape, enabling them to understand the types of data they possess, where this data resides, and who accesses it.
Data Classification
Data classification plays a crucial role in identifying and categorizing data based on content and context. In doing so, it allows teams to determine both the data’s classification and its sensitivity level.
It’s a vital component in data security, allowing organizations to align their DSPM framework and implementation with appropriate industry standards and data compliance regulations–such as the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), or the Health Insurance Portability and Accountability Act (HIPAA)–as well as an organization’s internal compliance programs.
Sensitive Data Discovery & Classification
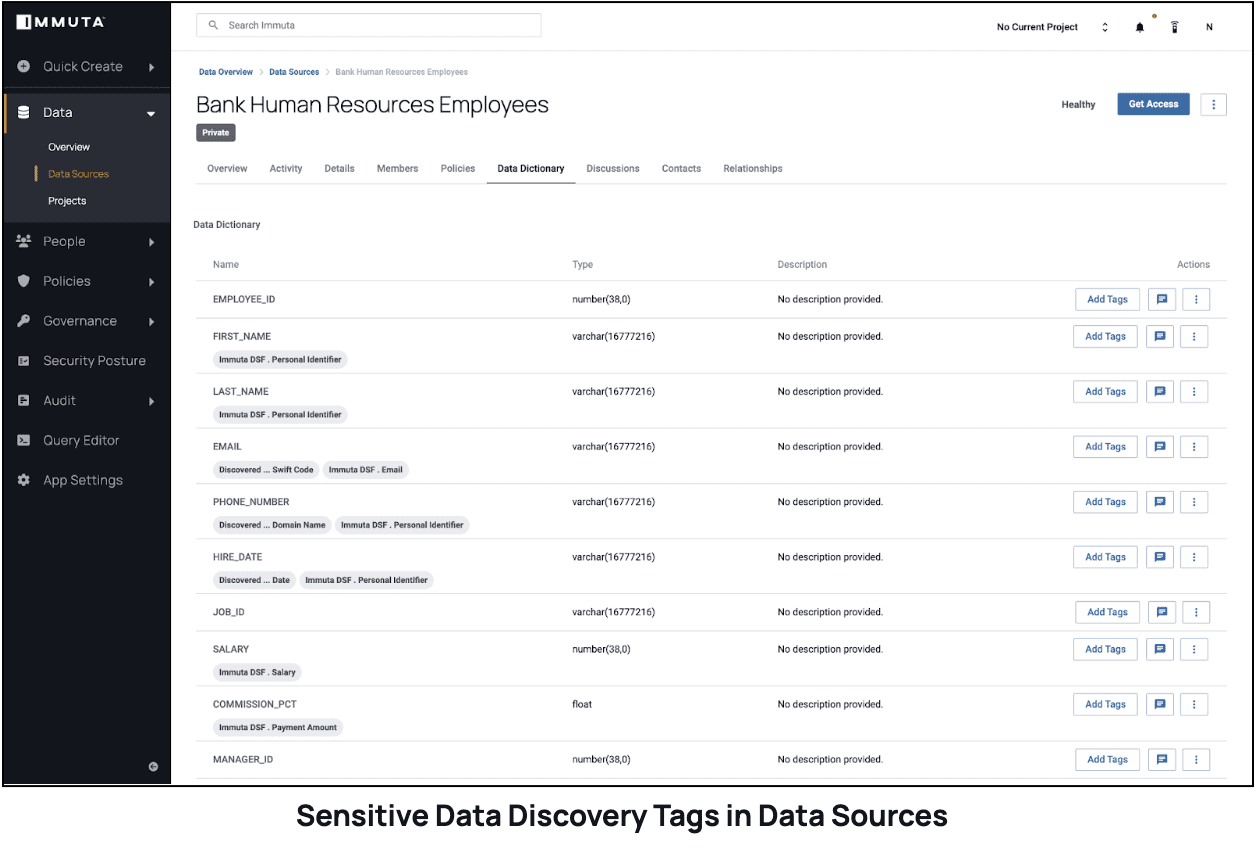
Immuta Discover is a component of Immuta’s industry-leading Data Security Platform and it provides sensitive data discovery & classification that automatically scans cloud data sources, generates standard tagging across multiple compute platforms, and classifies sensitive data such as personally identifiable information (PII) or protected health information (PHI). By leveraging Immuta Discover, organizations can eliminate manual, error-prone processes and have full visibility into all their data (see figure below with data attributes and tags). This tool also monitors data sources for schema changes, like the creation of new data sets or adding new columns to existing data sets. With Immuta Discover, organizations can accelerate the onboarding of cloud data sources, remove barriers, and gain rapid access to data-driven insights.
Immuta Detect
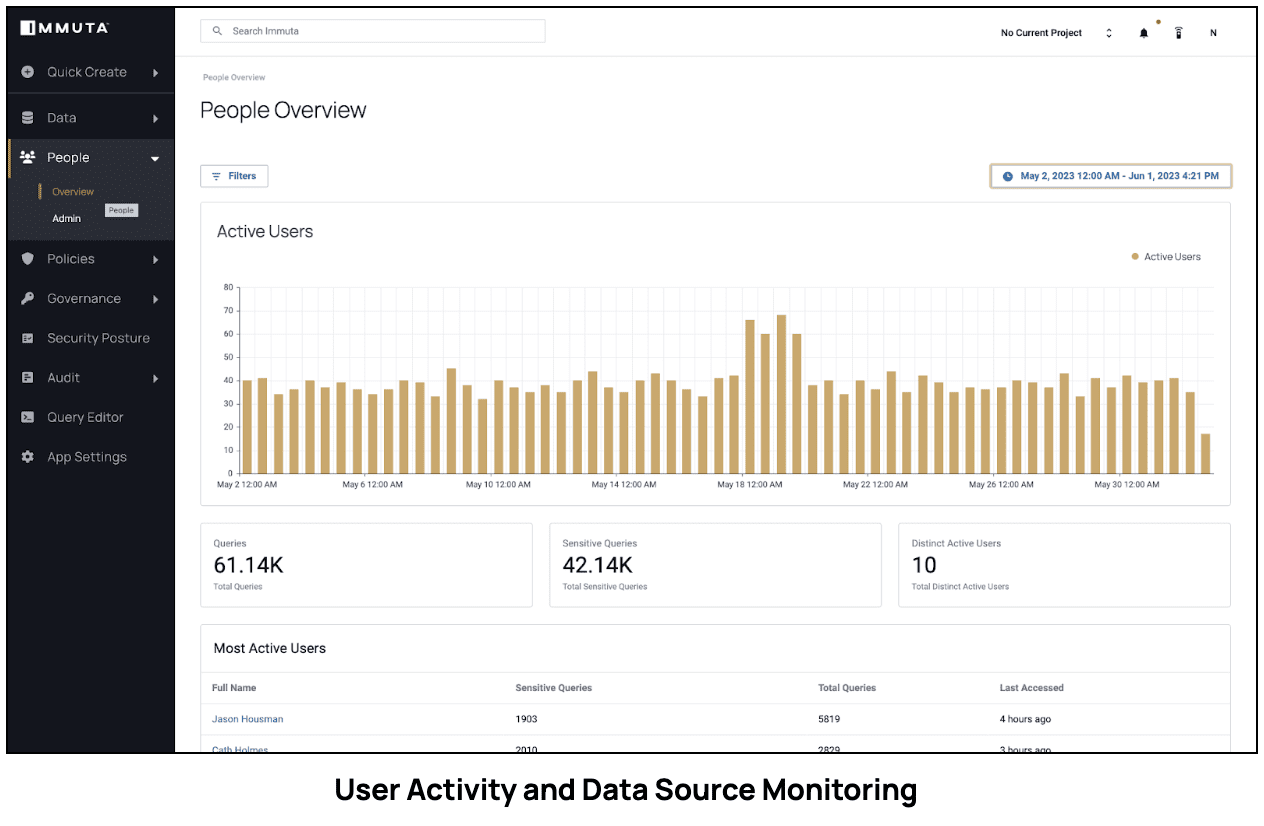
Immuta Detect is another component of Immuta’s Data Security Platform that provides timely insights into risky user data access behavior, enabling processes like data security posture management and risk remediation. Through continuous monitoring and analysis, Immuta Detect provides insights about organizations’ most active data users, their most accessed data sources, and the various events happening within their data environment. See the chart below displaying with sensitive query access analytics.
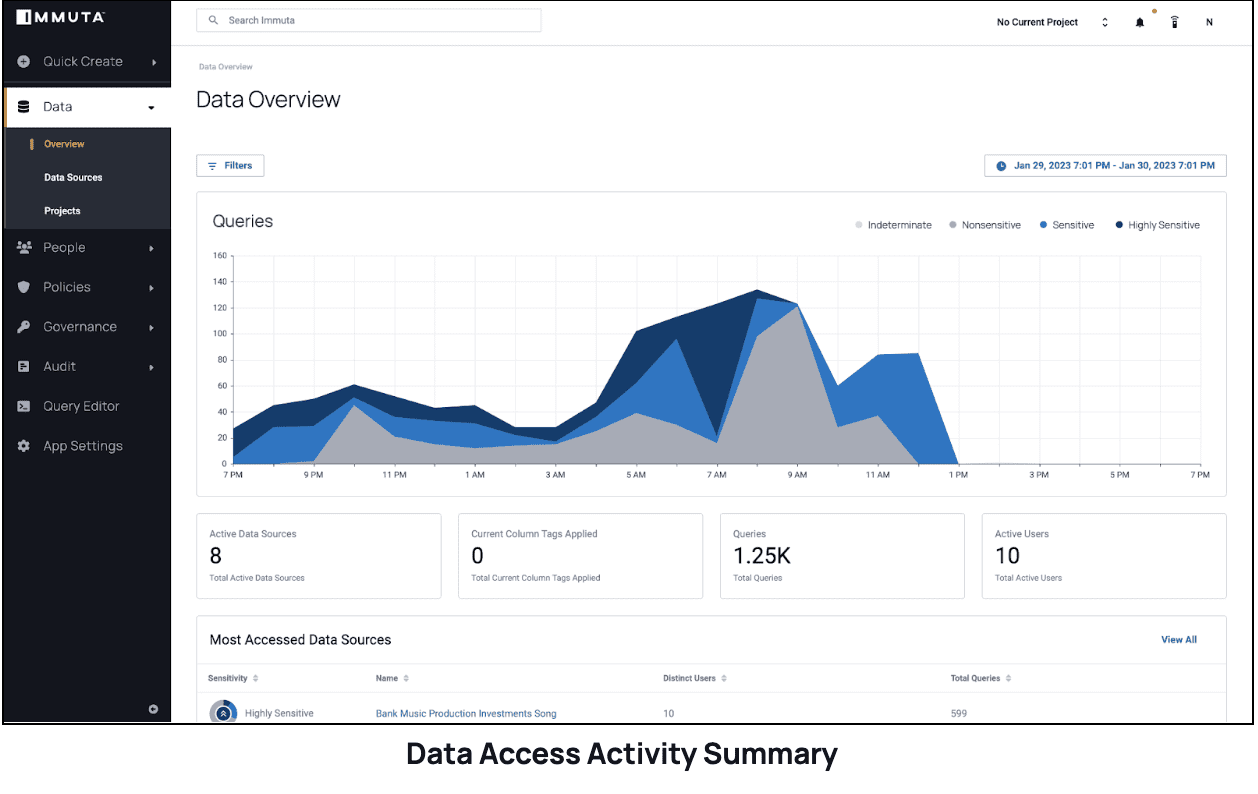
Organizations can use these insights to evaluate and improve security posture, identify any weakness or gaps in security controls, apply appropriate controls to safeguard sensitive data, and respond swiftly to any data security breaches in order to minimize any potential damage.
Detection with Data Classification
Immuta Detect offers dashboards with visualizations of audit events, including user query behaviors and data source activities. When classification is enabled, Immuta provides enhanced insights about both the sensitive data accessed by users and the data sources containing this data. The data is categorized by different sensitivity levels, such as Highly sensitive, Sensitive, Non-sensitive, and Indeterminate. See the chart below for data source activities by sensitivity level.
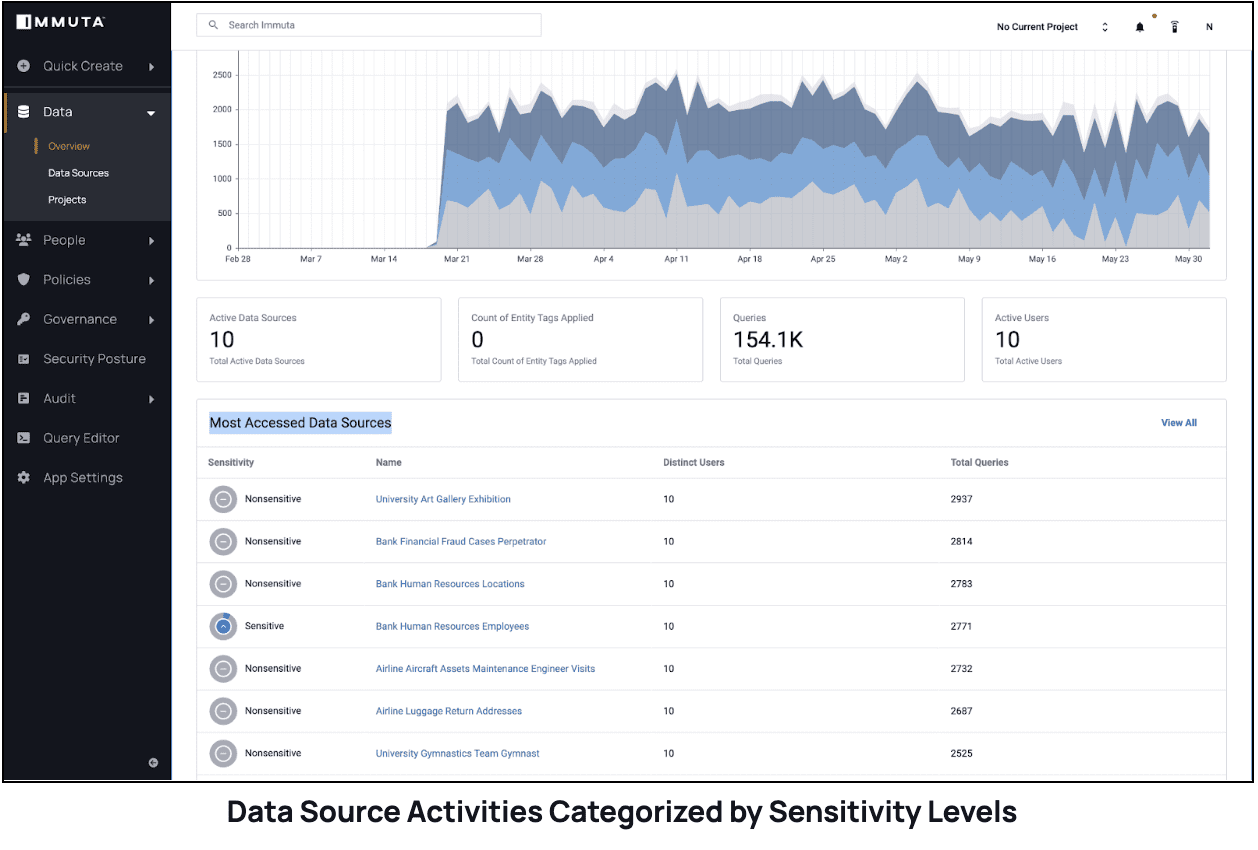
This valuable sensitivity information offers organizations the following benefits:
- Enhanced compliance
- Informed data access decisions
- Expedited auditing responses
- Streamlined data classification efforts
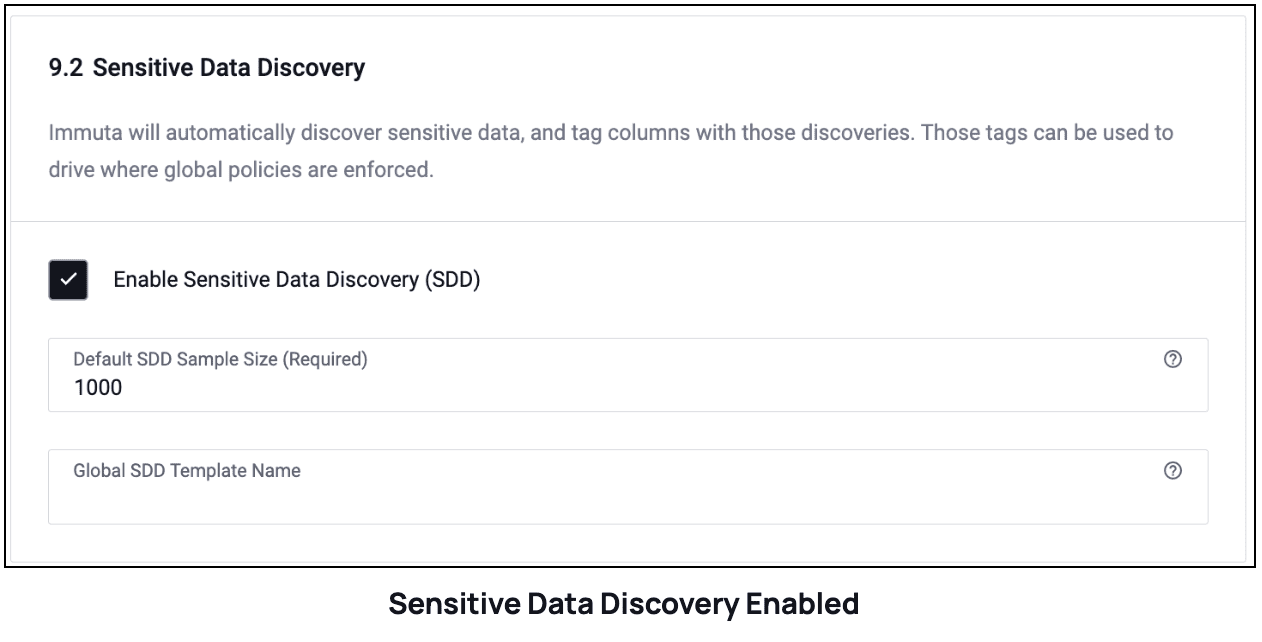
How to Enable Data Classification
To enable data classification in Immuta, you navigate to App Settings > Other Settings > Sensitive Data Discovery.
Detection without Data Classification
Some teams may not be able to enable data classification, or may choose not to do so for a variety of reasons, leaving their data unclassified. One of the most common reasons this may occur is that the process to apply tags, classify data, and assess the result is time consuming.
Nonetheless, these teams can still leverage Immuta Detect’s user activity behavior monitoring capabilities to gain insights from the data users and data events within their organization’s data environment. The Immuta Detect dashboards provides visibility into data activity patterns for both data sources and users, enabling users to identify the most recently accessed data sources and active columns.
While users won’t be able to see this audit event categorized by sensitivity level without classification enabled, teams can still greatly benefit with the following:
- A quicker and easier onboarding experience
- Zero configuration requirements
- Better prioritization of data classification efforts
While it is possible to switch back and forth between detection with classification and detection without classification, it’s important to note that the user and data source activity audit data remains consistent with the classification it has at the time of ingestion. If data classification is enabled, all data from that point onwards will have classification tags, while any audit data prior to that will retain its unclassified status. Conversely, if data classification is disabled, the classification tags will remain on past audit data, and any future data will be unclassified.
Conclusion
With Immuta Detect, organizations have the flexibility to implement detection with or without data classification enabled in order to monitor and improve their data security posture. Each of these options offers distinct benefits that cater to their organization’s needs and requirements.
To achieve the best value, enabling Immuta Detect with data classification enables organizations to gain a granular understanding of their data security landscape and implement security posture improvements tailored around specific sensitivity category levels. If an organization prefers not to enable classification, Immuta Detect without classification still offers a quicker and easier onboarding process for customers without any additional configuration requirements. This option allows organizations to prioritize their security efforts and data assets for future classification, focusing on immediate security monitoring needs.
If you are interested in learning more about Immuta Detect for data security posture management and risk mitigation, you can view this YouTube video or request a demo to learn how Immuta can help protect your sensitive data, streamline data governance efforts, and provide valuable insights into your data landscape.