Data Security for Google BigQuery
Immuta’s native integration with Google BigQuery automates data discovery, security, and monitoring for threat detection, so you can unlock value from even the most sensitive data. Data-driven organizations rely on Immuta to simplify operations, improve data security, and unlock value from their BigQuery data.
Try a DemoSimplify operations
Accelerate and simplify operations with 93x fewer data policies
Improve data security
Improve data security across hundreds of thousands of tables
Unlock data's value
Unlock data’s value with 100x faster
access to data
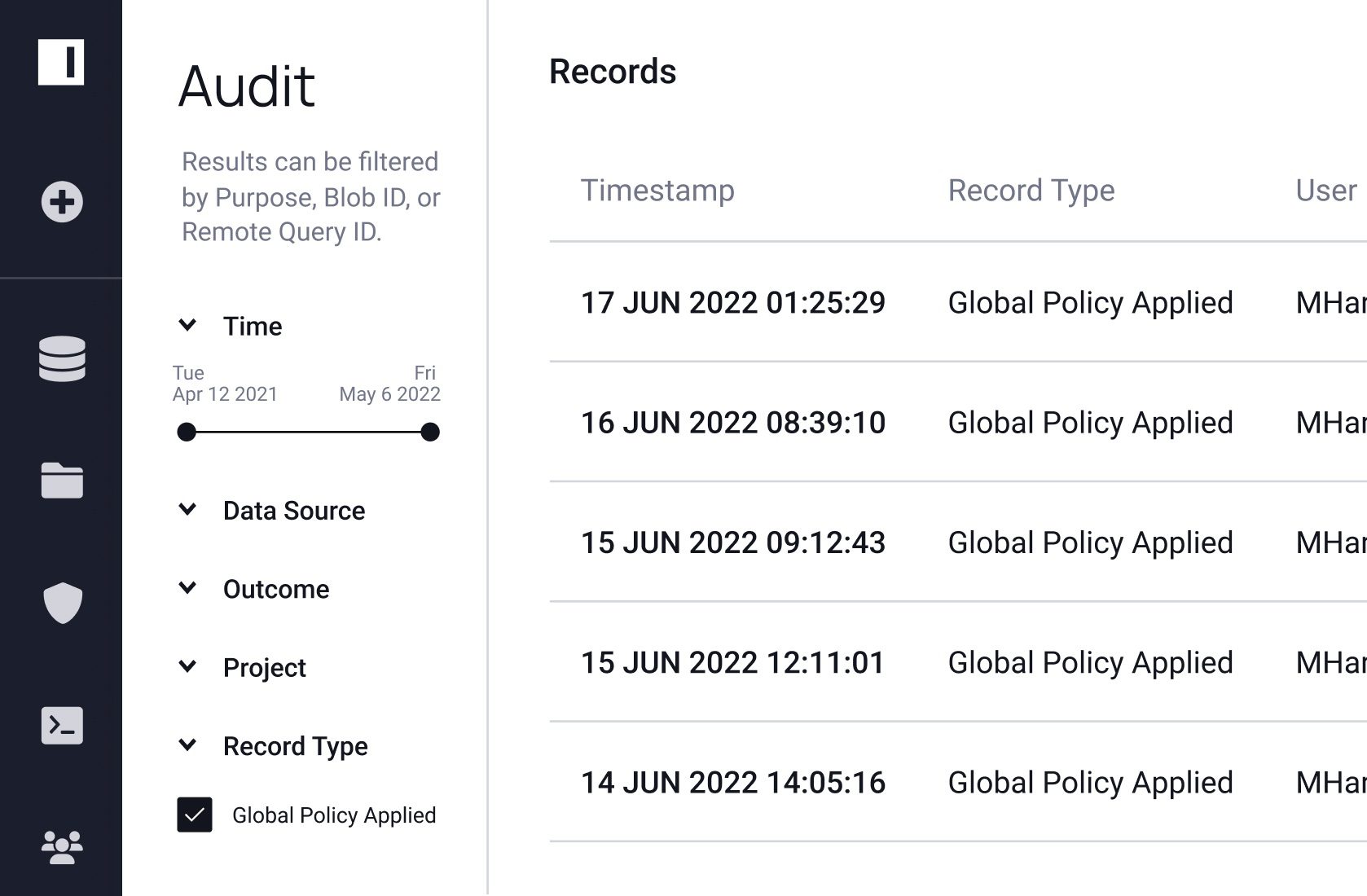
Discover
Discovery and Classify Sensitive Data
- Centralize data policy management
- Discover and classify sensitive data from millions of BigQuery tables
- Easily tag data like PII and PHI
- Apply 60+ prebuilt classifiers, alongside domain-specific and custom classifiers
- Monitor for schema and user changes
- Integrate and sync user information from your IAM
Secure
Secure Data with Dynamic Controls
- Orchestrate data policies
- Build data policies in plain language or as-code
- Enforce policies in real time when queries are run
- Enable attribute- and purpose-based access control
- Reduce policy complexity
- Leverage privacy enhancing technologies (PETs)
Detect
Monitor Activity and Detect Threats
- Enable data security posture management via an analysis engine
- Easily analyze data sensitivity levels and risk profile
- Receive timely insights into data access and user activity
- Proactively identify and remediate risks
- Generate audit reports to prove compliance
- Manage policy version and change audit
Data Sharing
When it comes to data sharing, data analytics rarely occur in a vacuum. Analysts collaborate and share scripts, dashboards, and models as they attempt to extract value from their organization’s most critical business asset: data. However, most controls protect only the raw data but not and fail to consider the security implications of production-level data. Immuta provides critical capabilities to enable enterprise data sharing through Projects, permission equalization, masking techniques, and data fingerprinting.
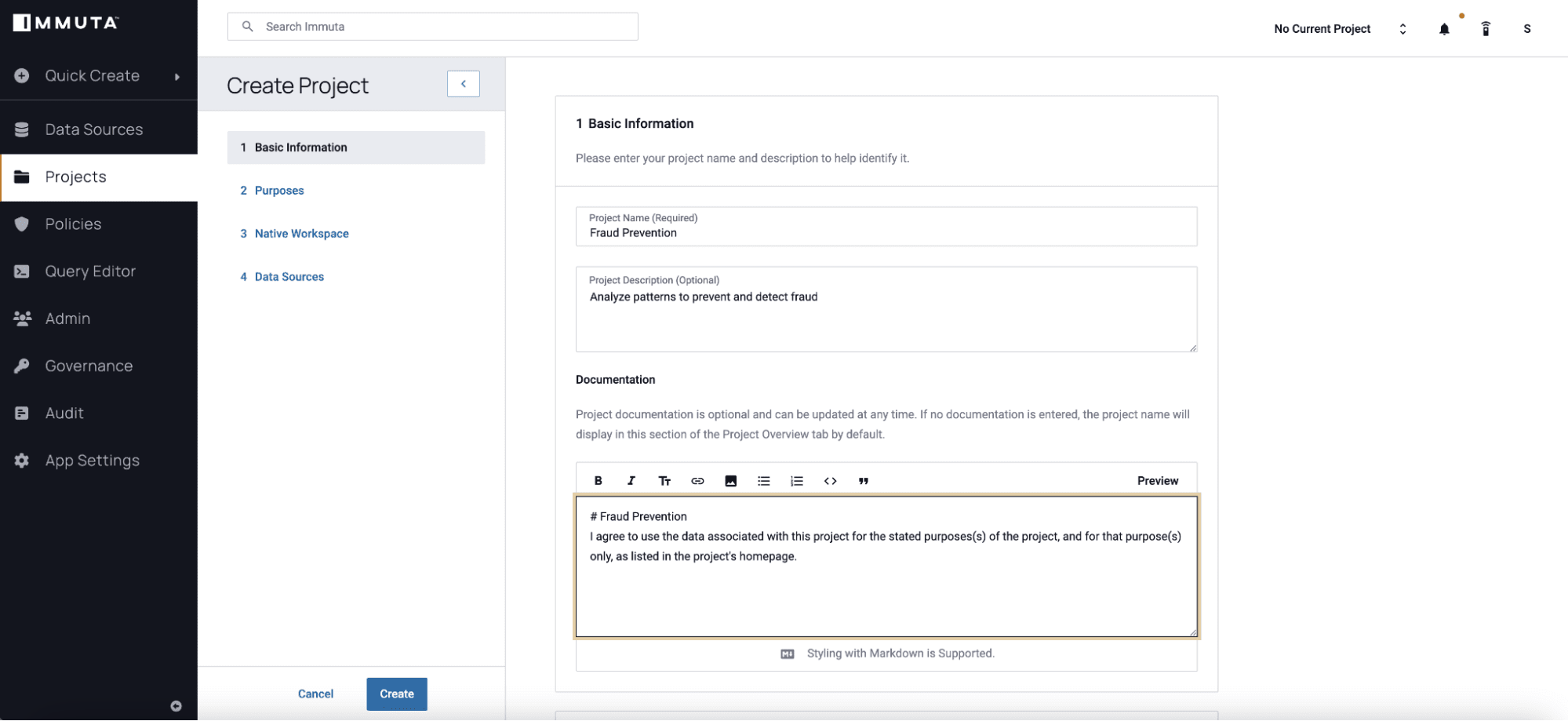
Data Access Control
As data teams modernize data stacks for the cloud, it’s becoming more difficult to control enterprise-wide data access. Each cloud provider has its own native access controls, making it difficult to control access across multiple systems, and multiplying the risks, costs, and maintenance as new platforms are added. Immuta is the data security and access control solution for cloud data ecosystems, enabling BigQuery data teams to accelerate data delivery, simplify administration, reduce risk, and safely unlock more data.
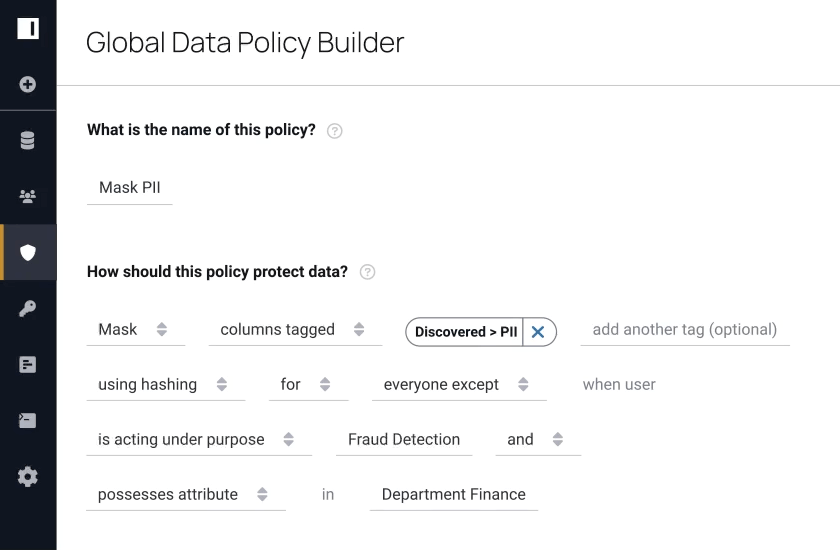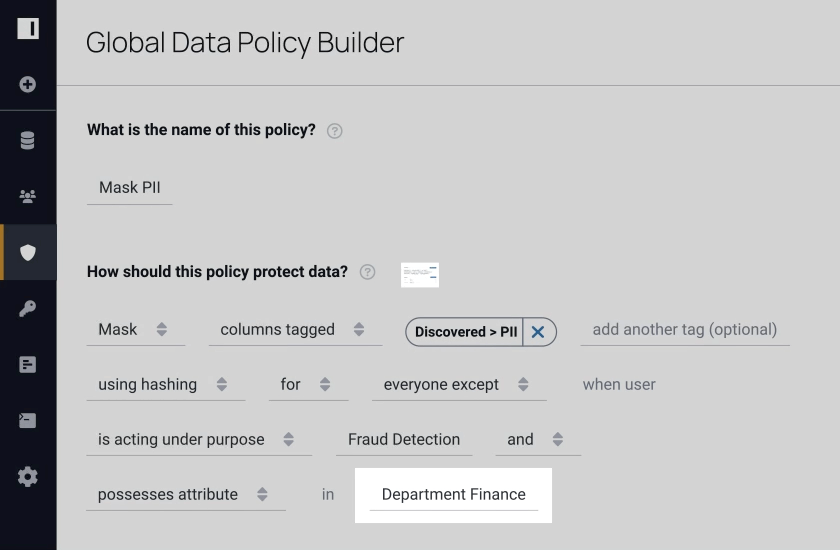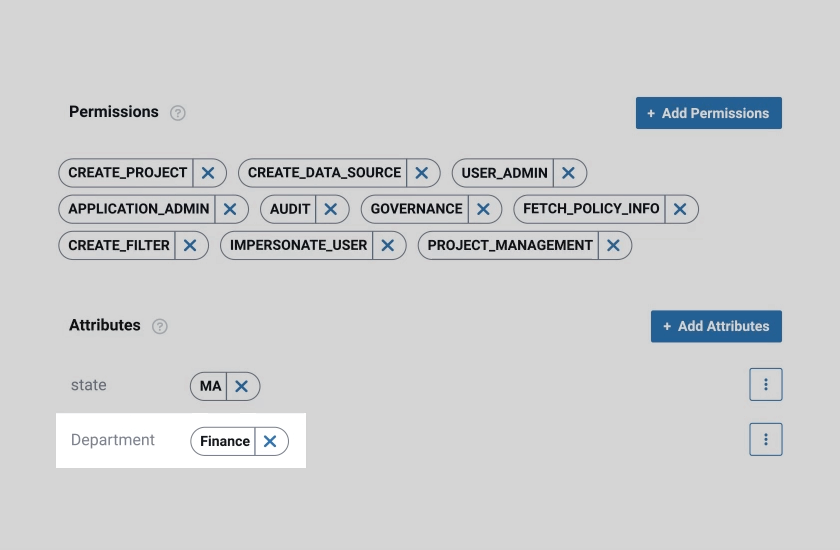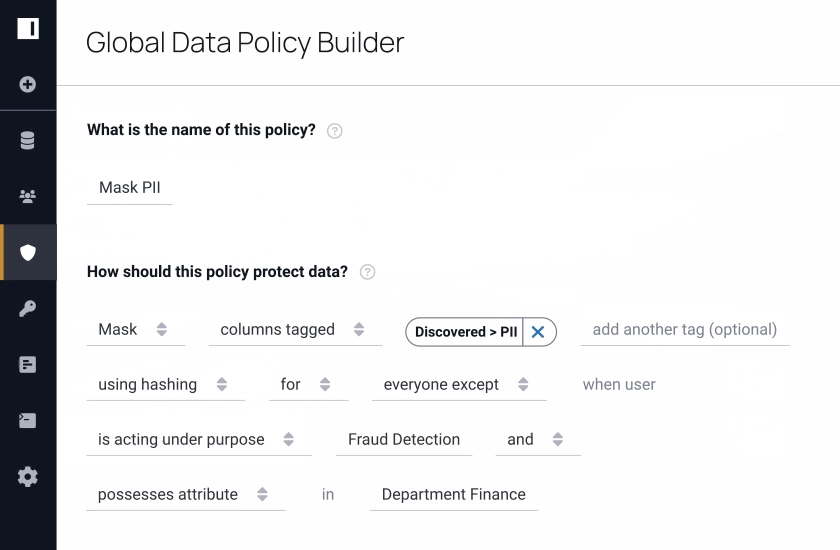
Data Regulations
As data rules and regulations rapidly increase, Immuta’s flexible security and access control allow users to create attribute- and purpose-based restrictions, simplifying compliance with regulatory requirements such as GDPR and CCPA. Immuta also monitors user activity and provides detailed audit logs, so governance teams can easily prove compliance or investigate incidents.