Data Security for
Azure Synapse
Immuta partners with Microsoft to ensure customers can protect and control their data on Azure Synapse. With Immuta, Synapse users can create data policies once and have them enforced across multiple data and cloud platforms, without managing roles. Organizations that compete with data rely on Immuta to simplify operations, improve data security, and unlock more value from their Azure Synapse data.
Request a DemoSimplify operations
Accelerate and simplify operations with 93x fewer data policies
Improve data security
Improve data security across hundreds of thousands of tables
Unlock data's value
Unlock data's value with 100x faster
access to data
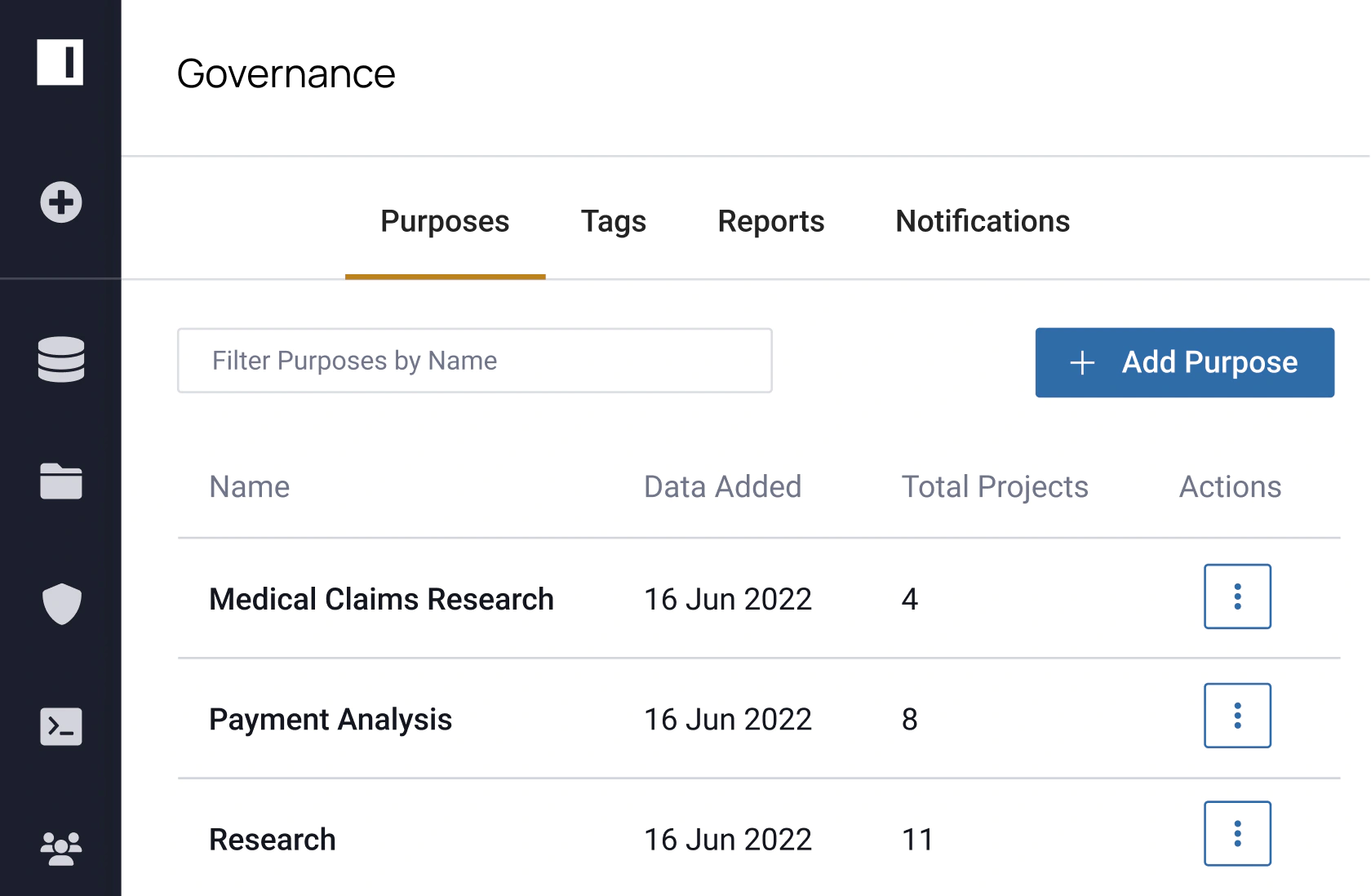
Discover
Discover and Classify Sensitive Data
- Centralize data policy management
- Discover and classify sensitive data from millions of Azure tables
- Easily tag data like PII and PHI
- Apply 60+ prebuilt classifiers, alongside domain-specific and custom classifiers
- Monitor for schema and user changes
- Integrate and sync user information from your IAM
Secure
Secure Data with Dynamic Controls
- Orchestrate data policies across Azure tables
- Build policies in plain language or as-code
- Enforce policies in real time when queries are run
- Enable attribute- and purpose-based access control
- Reduce policy complexity and eliminate role explosion
- Leverage privacy enhancing technologies (PETs)
Detect
Monitor Activity and Detect Threats
- Enable data security posture management via an analysis engine
- Easily analyze data sensitivity level and risk profile
- Receive timely insights into data and user activity
- Proactively identify and remediate risks
- Generate audit reports to prove compliance
- Manage policy version and change audit
Simplified Data Security
Immuta streamlines data security across your data ecosystem by using enterprise identity platforms to control access and enable zero trust. Separating policy from platform allows for consistent policy enforcement directly from Immuta across Azure Synapse and any other platform in your tech stack, so you can make sure only the right people can access the right data.

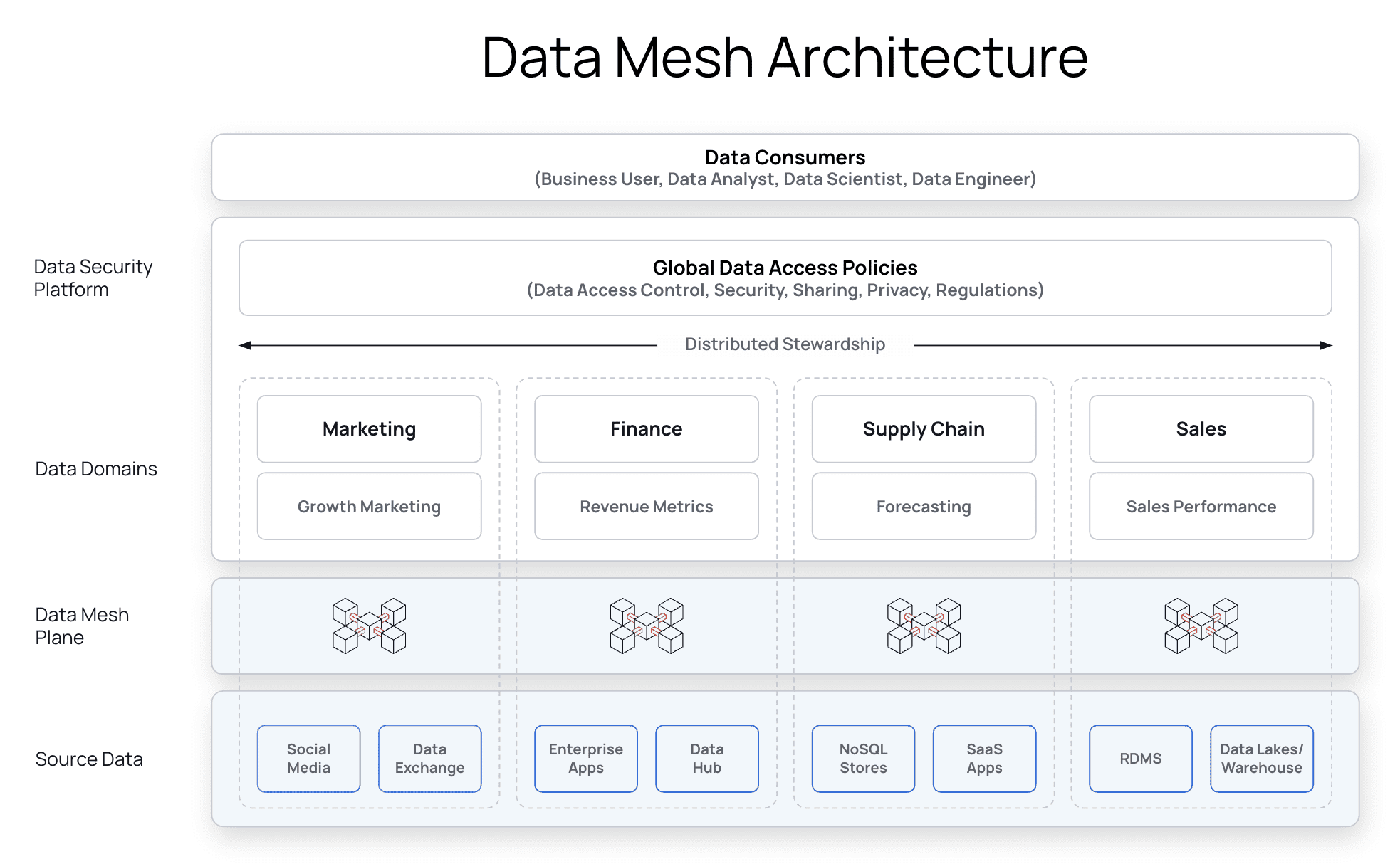
Data Mesh
Data mesh architectures give domain owners control over their data, freeing up IT bottlenecks and supporting data use across teams. Immuta increases agility and scalability for Azure Synapse customers leveraging data mesh by decentralizing governance, simplifying data product ownership, and enabling fast, secure data access.
Regulatory Compliance
Amid increasing regulations dictating data use, Immuta’s plain language policy builder and purpose- and attribute-based access controls simplify compliance. Immuta also provides detailed audit logs and reporting, so security and governance teams can easily prove compliance for auditors or investigate incidents.