Immuta for Amazon Redshift Security
For Amazon Redshift customers, Immuta delivers comprehensive data discovery and classification, security and access control, and monitoring and auditing. As an AWS Advanced Technology Partner, Immuta runs transparently alongside Redshift, allowing data users to use their BI tools, editors, workbenches, and notebooks of choice, without impacting performance or risk.
Request a DemoSimplify operations
Accelerate and simplify operations with 93x fewer data policies.
Improve data security
Improve data security across hundreds of thousands of tables.
Unlock data’s value
Unlock data's value with 100x faster
access to data.
Discover
Discover and Classify Sensitive Data
- Centralize data policy management
- Discover and classify sensitive data from millions of Redshift tables
- Easily tag data like PII and PHI
- Apply 60+ prebuilt classifiers, alongside domain-specific and custom classifiers
- Monitor for schema and user changes
- Integrate and sync user information from your IAM
Secure
Secure Data with Dynamic Controls
- Orchestrate data policies
- Build data policies in plain language or as-code
- Enforce policies in real time when queries are run
- Enable attribute- and purpose-based access control
- Reduce policy complexity
- Leverage privacy enhancing technologies (PETs)
Detect
Monitor Activity and Detect Risks
- Enable data security posture management via an analysis engine
- Easily analyze data sensitivity levels and risk profile
- Receive timely insights into data access and user activity
- Proactively recognize and remediate risks
- Generate audit reports to prove compliance
- Manage policy version and change audit
Data Access Modernization
For organizations looking to modernize efficiently with Amazon Redshift, Immuta’s plain language and as-code policy authoring puts policy management capabilities in the hands of technical and non-technical stakeholders alike. Users are empowered to create policies and implement dynamic attribute-based access controls, with no bottlenecks or technical expertise required.
Simplified Data Security
By separating policy from platform, Immuta consistently enforces policies across Redshift and any other platform in your tech stack, so you can control access and prevent unauthorized data usage. Leveraging enterprise identity platforms to control access streamlines data security across existing infrastructure and enables zero trust.

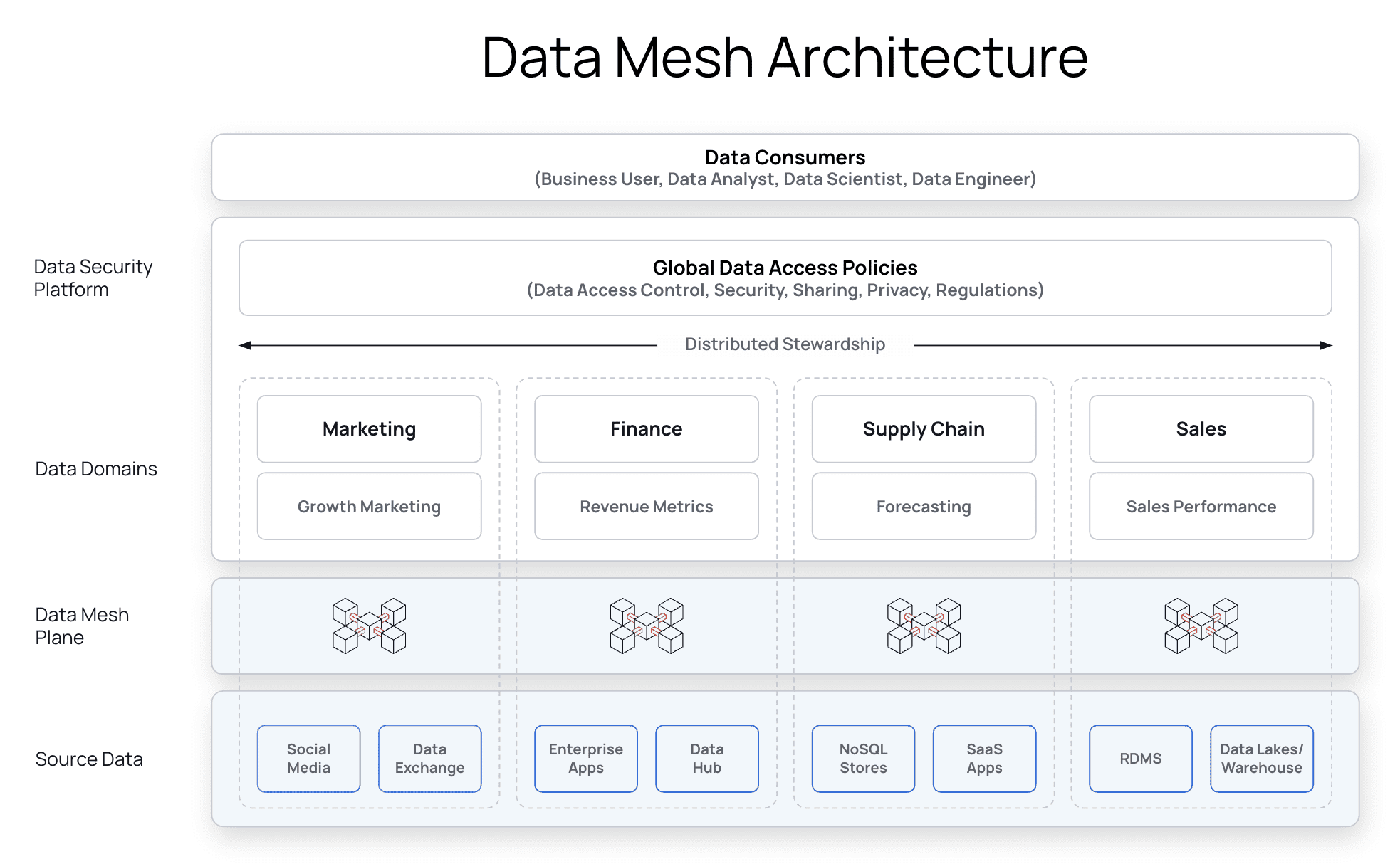
Data Mesh
For organizations leveraging Redshift within a data mesh architecture, Immuta decentralizes governance and gives domain owners responsibility for their own data management. This frees up IT bottlenecks and supports data use across domains, allowing organizations to increase agility with speed and scale.