Implementing Row-Level Security Across Platforms
As the use of sensitive data grows increasingly common, fine-grained access control has become crucial. Organizations must be able to restrict access to only the specific information a user is authorized to see. In contrast to high-level approaches such as database-level, table-level, and column-level security, row-level security (RLS) enables organizations to control data access down to the precise row. But implementing RLS across multiple platforms can be a complex process, especially in today’s hybrid and multi-cloud environments.
In this guide, we will explore how row-level security works and the benefits it provides. We’ll also explain how attribute-based access control (ABAC) enables a simple solution for RLS across platforms.
How Does Row-Level Security Work?
In a database, tables are organized into rows and columns. Each row represents a single record or entity, while each column represents a specific attribute or characteristic of that entity. For example, in a database table of weather data for various cities, a column titled “Average High” will contain many rows, each containing a value representing the average high of a single city.
Where column-level security broadly restricts access by columns, row-level security goes further, limiting access to specific rows. This means a user can view only the data in particular rows while the data in other rows within the same table remains hidden. Therefore, row-level security offers stricter, more granular control over individual records.
When row-level security is implemented, a database automatically applies designated access controls to the table at query run time. Access control can be based on numerous criteria, including user roles, departmental affiliations, geographic locations, and other parameters.
Row-Level Security in Action
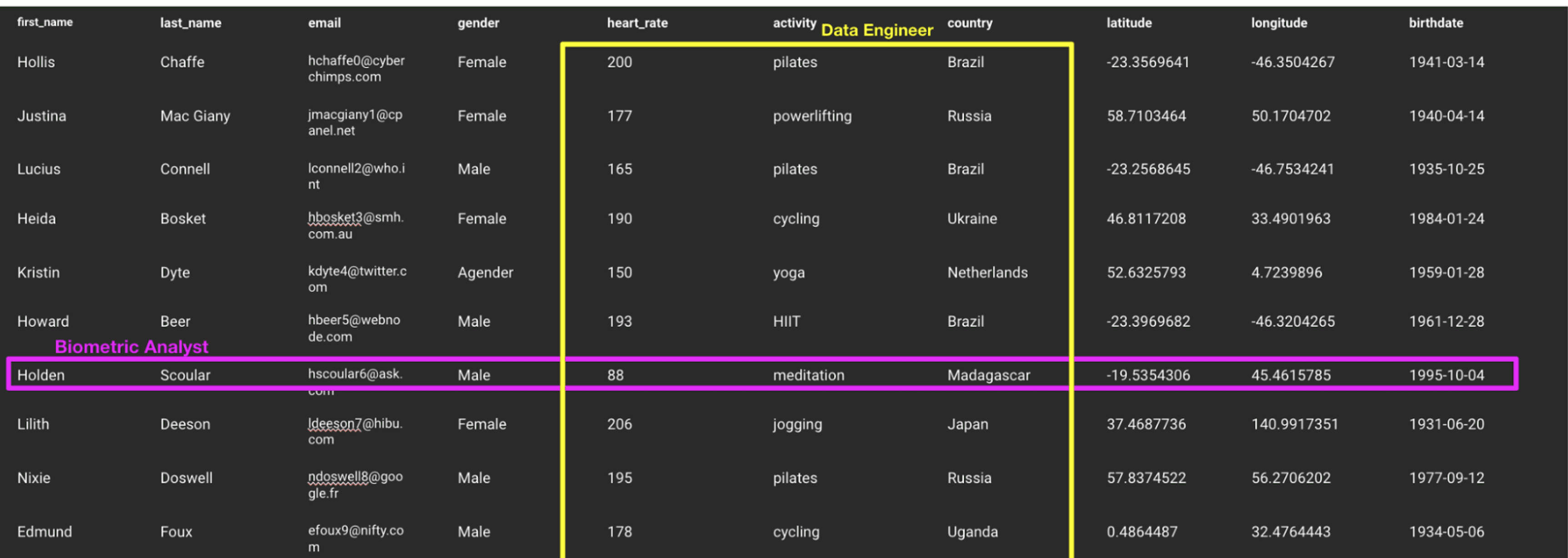
Row-level security is particularly useful in industries where data sharing is routine, such as healthcare and life sciences, public sector, and financial services. Let’s look at an example where a data engineer and a biometric analyst need to collaborate and share sensitive data gathered by a connected fitness tracking device and app.
The biometric analyst may only be authorized to view specific users’ data, while the data engineer can view any data, apart from identifying information. Row-level security allows them to share only the data they are both authorized to see, as illustrated below.
Benefits of Row-Level Security
With row-level security, organizations can protect sensitive data in multiple databases, ensuring only authorized users can access privileged data. The key is that RLS allows this to happen in a way that avoids locking down broad swaths of data, which means organizations can safely unlock more data. Paired with a data security platform that supports ABAC, organizations can easily enforce fine-grained policies, enable self-service data access, improve collaboration, and seamlessly integrate data security into modern data workflows.
Here are four reasons to implement row-level security:
Enhanced Data Security
Row-level security allows database administrators to control access to sensitive information at a much more granular level. This method protects the confidentiality and integrity of sensitive data by ensuring users only have access to the specific data they are authorized to view.
Improved Compliance
Compliance with data privacy regulations such as GDPR, HIPAA, and CPRA has become more challenging as sensitive data use increases and more teams handle data as part of their jobs. For example, analytics teams are crucial in helping line of business users access insights. Still, the GDPR and CPRA prevent them from viewing sensitive data without explicit, authorized purposes. Row-level security enables detailed access control enforcement for sensitive data, helping businesses improve compliance.
Simplified Data Management
Row-level security can play an important role in simplifying the process of granting and revoking access. Paired with a data security platform with a policy builder that lets users author policies in plain language, it can reduce the workload of database administrators, allowing them to delegate data access management to business units.
Increased Flexibility
Row-level security offers a more flexible approach to data access control. Using RLS, organizations can craft complex access rules based on various criteria, such as user role, location, and data sensitivity level. This enables organizations to evolve to meet changing data access requirements and protects against emerging security threats.
Automating the enforcement of data access, privacy, and governance policies is essential for organizations to realize the full potential of data-driven modernization. Automated policy enforcement is the backbone of modern data operations, which enables self-service data access and expedites businesses’ digital transformations by removing data access bottlenecks.
Row-Level Security Use Cases
As regulatory pressure and consumer awareness around data privacy builds, organizations in nearly every industry have much at stake in protecting the data they collect. Let’s explore five common use cases for row-level security, examining how RLS can be applied to different data types and organizational needs.
Financial Services & Insurance
Financial and insurance data is subject to stringent compliance laws and regulations such as PCI-DSS. Row-level security can be implemented to guarantee that only authorized users have access to the personal records and specific information within those records that they are authorized to view. RLS protects sensitive financial and insurance data, such as bank account numbers, credit card information, and credit history, and can help minimize the fallout from a security breach or data leak.
Healthcare & Life Sciences
HIPAA governs the sharing of patient health data, and the consequences of violating regulations can be significant – healthcare data breaches are the most expensive of any industry. The level of control provided by RLS ensures that healthcare providers can only access the health records of their own patients, and that support staff’s access to patient data is restricted to just the information they require to complete their work. For life science companies, RLS streamlines secure data sharing and collaboration to expedite initiatives like vaccine development.
Education
Many types of student data are subject to privacy regulations such as Family Educational Rights and Privacy Act (FERPA). Row-level security can help enforce compliance and protect confidential information, including grades, attendance records, and eligibility for federal programs such as special education. See how AstrumU was able to protect its users’ education data while revolutionizing insights for higher education.
E-commerce
E-commerce businesses store large amounts of sensitive data on their customers, including names, addresses, credit card information, and order histories. For online retailers operating in multiple countries, data localization and sovereignty requirements can be difficult to manage, with each jurisdiction having its own standards. Row-level security can restrict access to only the information an employee is authorized to view according to the relevant countries’ regulations.
The Role of Attribute-Based Access Control Policies in Enforcing Row-Level Security
Despite its benefits, many organizations fail to implement row-level security, primarily because it can be challenging to set up and maintain when multiple databases and platforms are involved. Attribute-based access control is an ideal solution for streamlining implementation. ABAC considers dynamic user subject attributes, such as geography, time and date, clearance level, and purpose (represented as policy variables) to make context-aware access decisions at query time. If a new data set is entered into the system or relevant metadata about a user changes, access policies will automatically adjust as necessary – no manual human intervention required.
ABAC also helps data teams resolve issues stemming from “role explosion,” a situation frequently encountered with static, role-based policies that require the manual management of hundreds or thousands of user roles to control access to data in specific tables or databases. Compared to RBAC, research has found that ABAC requires 93x fewer policies to manage, which could equate to a cost savings of $500,000 in operational efficiency.
Protect Your Sensitive Data with Row-level Security
RLS enables organizations to focus on leveraging the value of sensitive data while protecting that data and staying compliant. Implementing row-level security across platforms can be a complex and challenging process. But it’s simple to unlock the full value of RLS by using a data platform that supports a dynamic ABAC approach.
Read RBAC vs. ABAC: Future-Proofing Access Control Methods to learn more about attribute-based access control.