When we think of threats to data, malicious hackers who are out to profit off our information tend to come to mind. But what about the risks that are hiding in plain sight? Outdated systems, shared passwords, and lax controls may all seem like low grade issues – until they end up at the root of a data leak.
With growing consumer awareness about how data is collected, stored, and used, organizations simply can’t afford to ignore these concerns – literally. Penalties for mishandling and leaking data are in the millions, not to mention the trust and revenue that companies stand to lose in the aftermath.
In this blog, we’ll take a closer look at data leaks, including what to watch out for and how to put safeguards in place to keep your data secure.
What is a Data Leak?
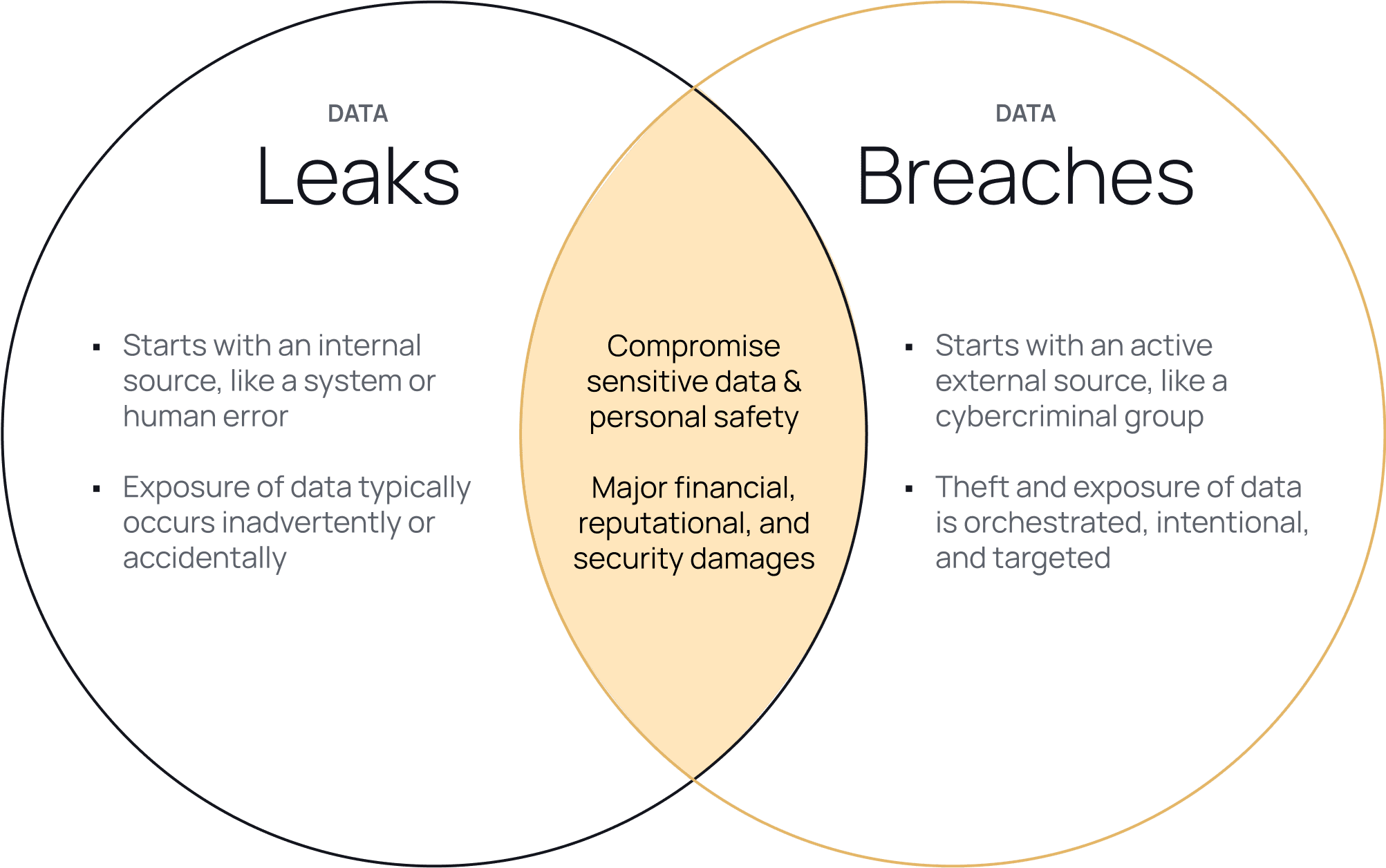
Data leaks are incidents in which an internal party exposes sensitive or private information to unauthorized individuals, usually unknowingly or accidentally. Leaks are often conflated with data breaches, which are orchestrated and intentional attacks on data and networks by external parties like cybercriminals. Still, the two are inextricably linked since data leaks make incidents like breaches, identity theft, and ransomware installation faster and easier to execute.
Data leaks may be caused by a number of factors, including:
- System Vulnerabilities: Unpatched software, outdated systems, and misconfigured security settings all open the door for sensitive data to slip through the cracks.
- Weak or Inconsistent Access Controls: When access control frameworks are brittle or applied haphazardly, it introduces risk of the wrong people gaining access to sensitive information.
- Lack of User Verification: Identity and access management (IAM) tools like Okta that guard access to systems and apps by continuously verifying users’ credentials are foundational to network security.
- Human Error: If employees are not educated on how to properly handle sensitive data, secure their equipment, or protect their networks, they’re more likely to inadvertently expose information. For instance, failing to regularly change passwords or responding to phishing schemes could leak internal data.
- Insider Threat: Although most data leaks are accidental, organizations must always consider the possibility of current or former employees leaking information. Insider risk management helps reduce the likelihood of this scenario.
With increasing rates of data creation, collection, and usage across every industry, leaks are all but inevitable. High profile leaks constantly make headlines, including:
- Twitter: In early 2023, outlets reported on a vulnerability in Twitter’s API that allowed malicious actors to see the email addresses and phone numbers associated with individual Twitter accounts. The glitch went unnoticed from June 2021 until January 2022, and allowed hackers to publish more than 200 million Twitter users’ email addresses.
- ChatGPT: In March 2023, a bug in the Redis client open-source library exposed the billing information of 1.2% of ChatGPT Plus subscribers over a nine-hour period. Separately, three Samsung employees were found to have leaked sensitive proprietary information to ChatGPT, including source code and meeting recordings, prompting the company to limit usage and investigate those responsible.
- Meta: In April 2021, the personal information of more than 533 million people who used Facebook between 2018 and 2019 was exposed on an internet hacking forum. A system vulnerability (that had been patched in 2019) allowed bad actors to access users’ full names, phone numbers, locations, and birthdates, and Meta was subsequently fined more than $275 million by Ireland’s Data Protection Commission.
What could these companies have done to proactively strengthen their approaches to data leak prevention?
Data Leak Prevention: 4 Proactive Methods
The examples above underscore the importance of building robust data security frameworks into standard workflows and processes. Too often, inadequate system configurations or human attentiveness cause data leaks that are costly and preventable.
Data leak prevention starts with a proactive approach to protecting information. Here are four tactics that should be table stakes for any data-driven organization:
Scalable Data Access Controls
Access control management is fundamental to securing data, but the complexity of modern cloud architectures, volume of data, and number of data users can cause it to quickly get out of hand. Data platform teams need to ensure that the right controls are consistently enforced; governance, risk, and compliance (GRC) stakeholders must verify that those controls satisfy pertinent rules and regulations; and data security teams are constantly tracking potential threats to IT infrastructure. All this must happen quickly, effectively, simultaneously, and at scale, without creating delays that prevent data consumers from doing their jobs.
Reliance on legacy RBAC (role-based access control) requires significant manual effort and oversight that could easily heighten the risk of a data leak. For instance, if an employee changed departments but the system admin neglected to update their role, they would inadvertently have access to both departments’ data. Accidentally exposing one department’s data to unauthorized users or external partners would be considered a data leak.
Attribute-based access control (ABAC) is a more resilient, dynamic, and scalable alternative to RBAC that avoids such scenarios by automatically applying policies at query time, based on traits about the user, data, environment, and intended action. An ABAC model reduces the number of policies that data platform teams need to manage by 93x and mitigates the risk of human error, which are key for scalable data leak prevention. Ensuring only the right people can access the right data at the right time helps guard against insider threats and provides a safeguard against potential unknown system vulnerabilities.
[Read More]: Role-Based Access Control vs. Attribute-Based Access Control
Data Masking & Privacy Enhancing Technologies (PETs)
Data masking adds a layer of protection by obscuring, transforming, or otherwise de-identifying sensitive information so that even if it were to end up in the wrong hands, it would be useless. This preserves data’s utility but minimizes the chance that, if leaked, it could be used by bad actors to expose personally identifiable information (PII), protected health information (PHI), or other data.
Privacy enhancing technologies (PETs) such as data obfuscation, k-anonymization, and differential privacy provide mathematics-backed assurance that even if an authorized employee accesses and shares sensitive data, the recipient of that information will not be able to use it to re-identify an individual, expose trade secrets, or otherwise use it for any meaningful task.
[Read More]: What Are the Most Common Types of Data Masking?
Data Monitoring & Threat Detection
While data access control and dynamic data masking are highly effective at reducing the risk of data leaks, they cannot eliminate the possibility entirely. Continuously monitoring data to detect anomalies and suspicious activity helps to proactively identify risky behavior that may cause a data leak.
For instance, if a specific user that works solely with internal teams suddenly begins sharing data with external sources, that should raise a red flag for security teams. In the event they have fallen for a social engineering scam, this data sharing activity could expose sensitive data to bad actors and make the entire network more vulnerable. Additionally, tracking policy enforcement and performance metrics helps data platform and security teams identify and address weaknesses in their systems and processes that could cause leaks like those at Twitter, ChatGPT, and Meta.
To supplement these control mechanisms, all enterprises should have an incident response plan so they can efficiently mitigate the impact of data leaks.
[Read More]: 5 Steps for an Effective Data Breach Response
Data Culture & Enablement
Since data leaks originate internally, building a culture of awareness around data security and enabling employees with information about how to handle sensitive data is perhaps the easiest (and cheapest) way to mitigate risks. Many organizations provide online training to employees about how to recognize and report social engineering techniques like phishing emails. But it can be easy to simply check a box and move onto the next task at hand. Going a step further to educate employees about different sensitive data classifications and potential consequences of a data leak provides important context that can help ensure they stay hypervigilant.
Additionally, reinforcing good password hygiene, like mandating regular updates and encouraging individuals to use different passwords across platforms, empowers your employees to be a strong first line of defense against data leaks.
How to Manage Data Leak Prevention in Modern Tech Stacks
Technology is evolving and advancing so quickly that today’s controls could be rendered ineffective tomorrow. By way of example, RBAC used to be considered the gold standard for access control, but as diverse cloud ecosystems and paradigms like data mesh have become more popular, teams are recognizing its limitations and looking for a new solution in ABAC.
This begs the question, what will data platform and security teams need in order to enable data leak prevention as modern tech continues to evolve? Here are four predictions:
- Automation will be key to orchestrating and enforcing data access controls; enabling real-time threat detection and response; and providing scalable data protection.
- Connectivity across cloud platforms will be an absolute requirement for integrating and centralizing controls, consistently enforcing policies, and efficiently managing data assets across distributed environments.
- AI and ML will use advanced pattern recognition capabilities to detect anomalies, provide user behavior analytics, and generate predictive insights to stay ahead of threats.
- Streamlined auditing will allow visibility into data access, usage, and modifications, simplify regulatory compliance, and identify potential vulnerabilities and unauthorized activity.
The Outlook on Data Leak Prevention
Threats abound in today’s data-fueled environment, and while you can’t eliminate the possibility of data leaks entirely, implementing the right data security measures can vastly improve your odds. Immuta is built to handle the complex, decentralized nature of modern tech stacks by automating security and privacy controls – no additional time or overhead required.
Immuta’s data access governance and provisioning capabilities provide comprehensive protection against risks – both internal and external – to ensure that the right people are able to access the right data. With Immuta, teams can simplify operations and improve data security, allowing them to reduce policy burden by 93x while accessing data 100x faster.
Data Risk Management 101
Start building your strategy for protecting sensitive data with these best practices.





