
Immuta was born out of the Intelligence Community in 2015 to help organizations solve the most complex data access control challenges. These challenges have only grown since that time as our dependency on sharing sensitive data across platforms and groups to support decision makers has increased.
To meet the needs of this increasingly complex data environment, the United States Department of Defense (DoD) recently published a Data Strategy that outlines the vision, focus areas, guiding principles, essential capabilities, and goals necessary to transform the Department into a data-centric enterprise. These strategic goals are vital to the Department’s performance, as well as the nation’s security.
Immuta, the universal cloud data access control solution with deep roots in the Intelligence Community, addresses several of the DoD Data Strategy’s goals and their underlying objectives. In this blog, we will explain how Immuta’s platform-agnostic capabilities help make data an enterprise resource by ensuring data security and privacy; as well as how our public sector team is specifically positioned to help current and future customers achieve success with their data.
DoD Data Strategy Goal 1: Make Data Visible
“The goal of making data visible enables authorized users to discover the existence of data that is of particular interest or value. Data stewards, data custodians, and functional data managers are all responsible and obligated to make their data visible to authorized users by identifying, registering, and exposing data in a way that makes it easily discoverable across the enterprise, and to external partners as appropriate.”
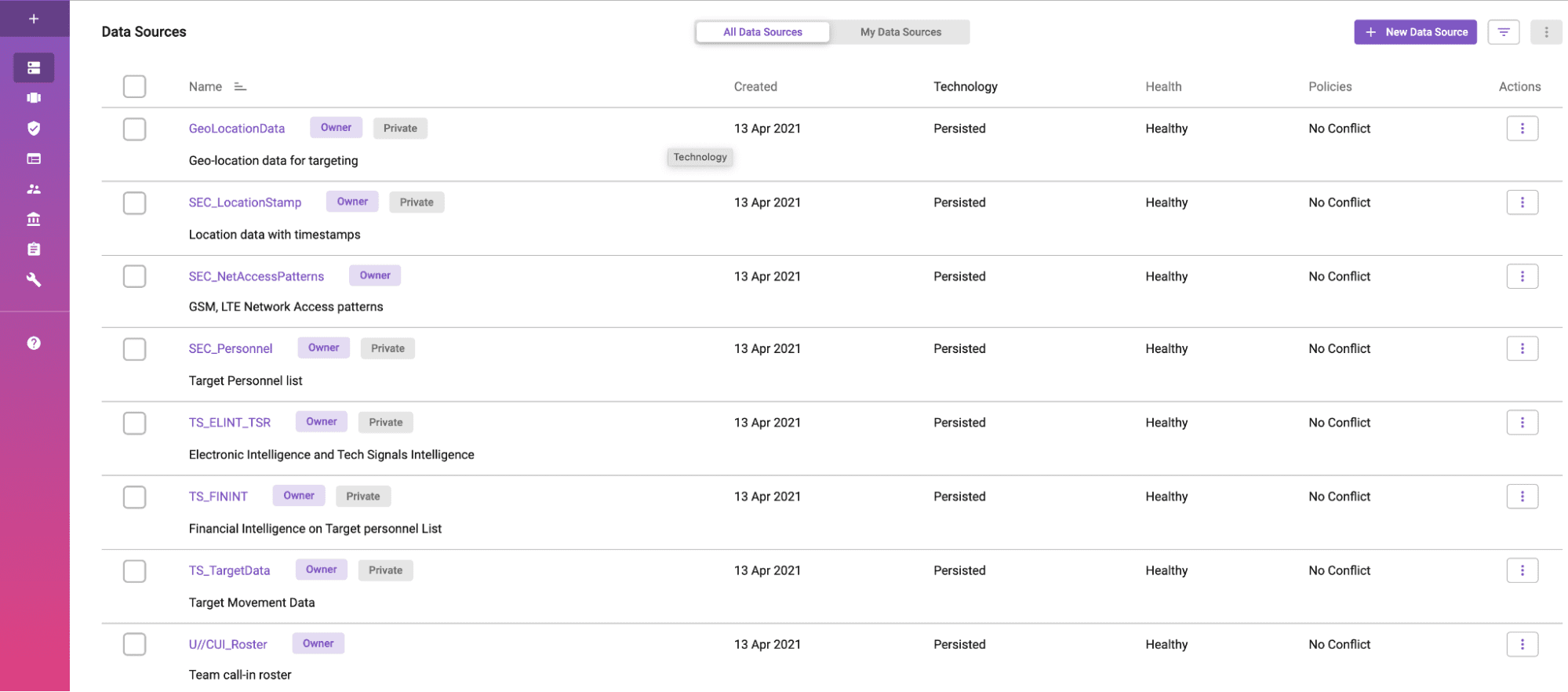
Immuta’s data catalog provides a simple view of data sources, the type of connection, and their health.
Data sharing and collaboration are imperatives across the Department of Defense and the IC — and a lack of data sharing upends mission gains. Immuta’s automated cloud data access control platform addresses both of these issues, while providing agencies the highest combination of data utility and data privacy.
Focusing specifically on Objective 1 of this goal, the strategy states that progress has been made when data is advertised and available for authorized users, when and where needed. Immuta not only makes data visible, but also puts it into an easy-to-discover format, and is only advertised when the user has permission to see it. Our active data catalog is built on a strong security foundation with “always-on” governance and access control. Since Immuta’s UI simplifies sensitive data discovery and integrates with existing data catalogs, it is ideal for data scientists, technical analysts, and business analysts, as well as non-technical stakeholders in governance or legal/compliance teams. With this capability, organizations can provision self-service user access to any data – even the most sensitive – while eliminating cumbersome approval workflows.
DoD Strategy Goal 2: Make Data Accessible
“The goal of making data accessible enables authorized users to obtain the data they need when they need it, including having data automatically pushed to interested and authorized users. Data accessibility must comply with Public Law (P.L.) 115-435, the Foundations for Evidence-Based Policymaking Act of 2018. DoD is making data, including warfighting, intelligence, and business data, accessible to authorized users.”
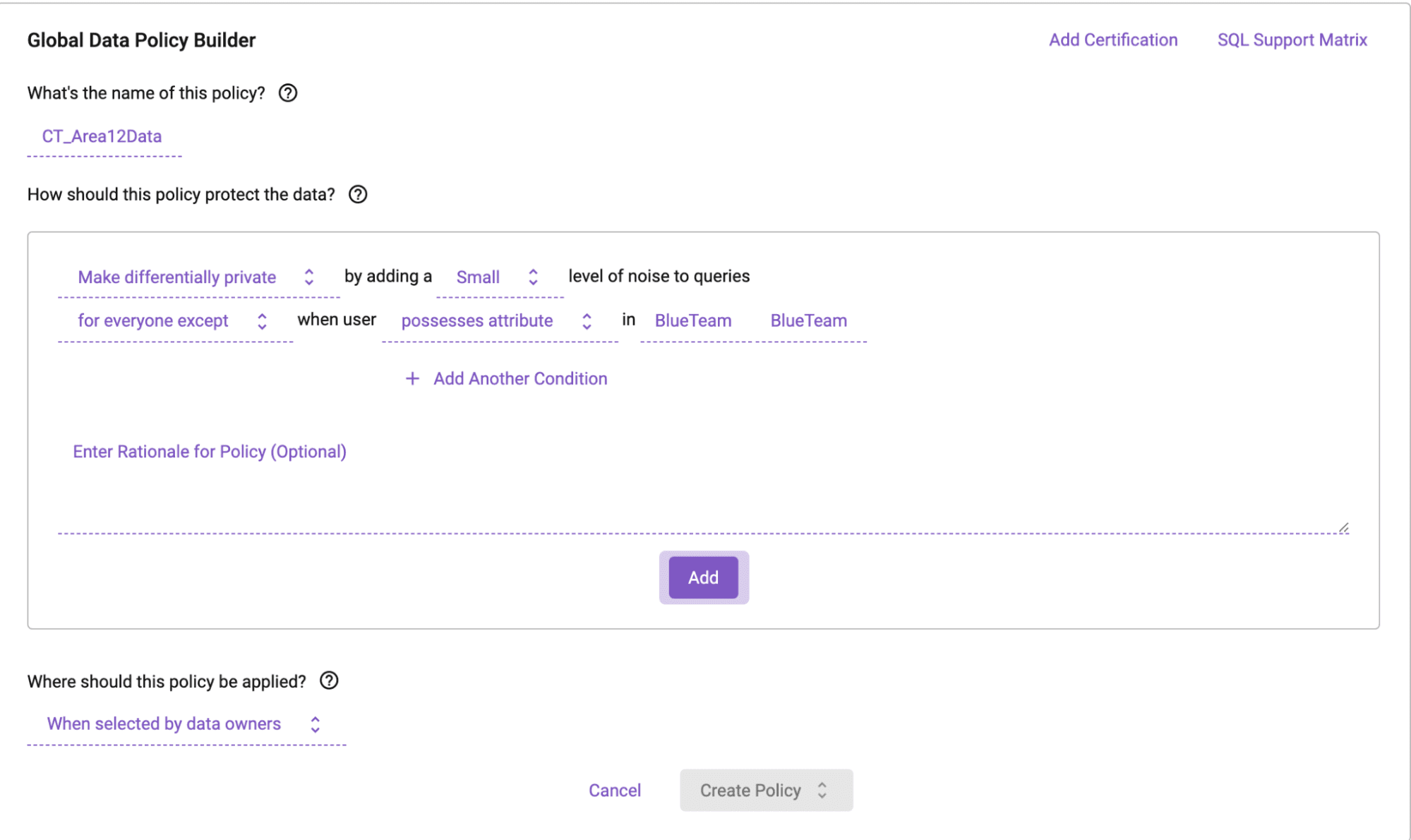
Immuta’s policy builder allows for simple, no-code policy generation by anyone of any skill.
Inability to access sensitive data undermines success and slows down decision science, both on the battlefield and in the cybersecurity space. The DoD Data Strategy states, “accessibility requires that protective mechanisms (e.g., security controls) are in place for credentialed users, to ensure that access is permitted in accordance with laws, regulations and policies.”
One of Immuta’s core capabilities is data access control, in which automated, fine-grained access to sensitive data starts with a no-code policy builder. Data stewards and engineers can author policies “as code” in plain English, so all security and governance stakeholders understand how data access control is both managed and protected. Whether policies are created at the global level (federal law, regulations, etc.) or the local level (built specifically by data stewards), Immuta enables organizations to give their data both utility and privacy.
The key to Immuta’s approach is attribute-based access control (ABAC), which allows data teams to automatically enforce policies based on a set of dynamic attributes, such as title authority, geography, or purpose, while avoiding static role-based approaches that are unscalable and often lead to role explosion. For members of the DoD, this ensures that the right people can access the right data at the right time, without delaying mission-critical decisions.
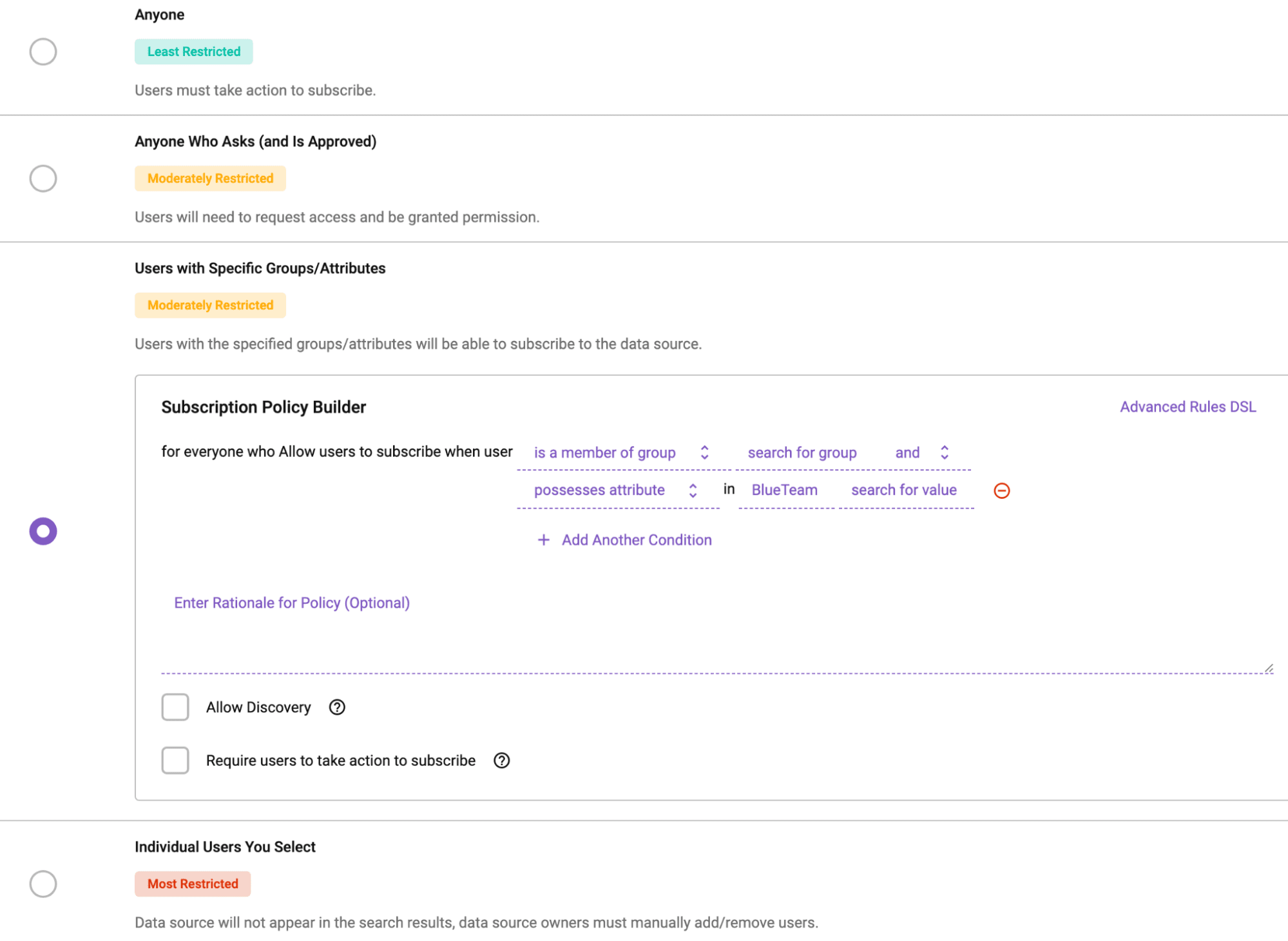
Immuta’s policy engine utilizes attribute-based access controls to govern access to sensitive data.
Data engineers can also use Immuta’s platform-agnostic, rich APIs to make policies extensible to other tools in the data stack, enabling consistent enforcement of access controls across any platform and reducing the need for repetitive or manual processes. Immuta can further integrate and federate the external metadata from other data classification and catalog tools to improve search and discovery, and to create richer policies based on existing ontologies or schemas.
DoD Strategy Goal 5: Make Data Trustworthy
“DoD data requires trust to deliver the needed value to its Service members, civilians, and stakeholders. Lacking confidence in the data may result in less timely decision-making or, consequently, no decision when one is warranted.”
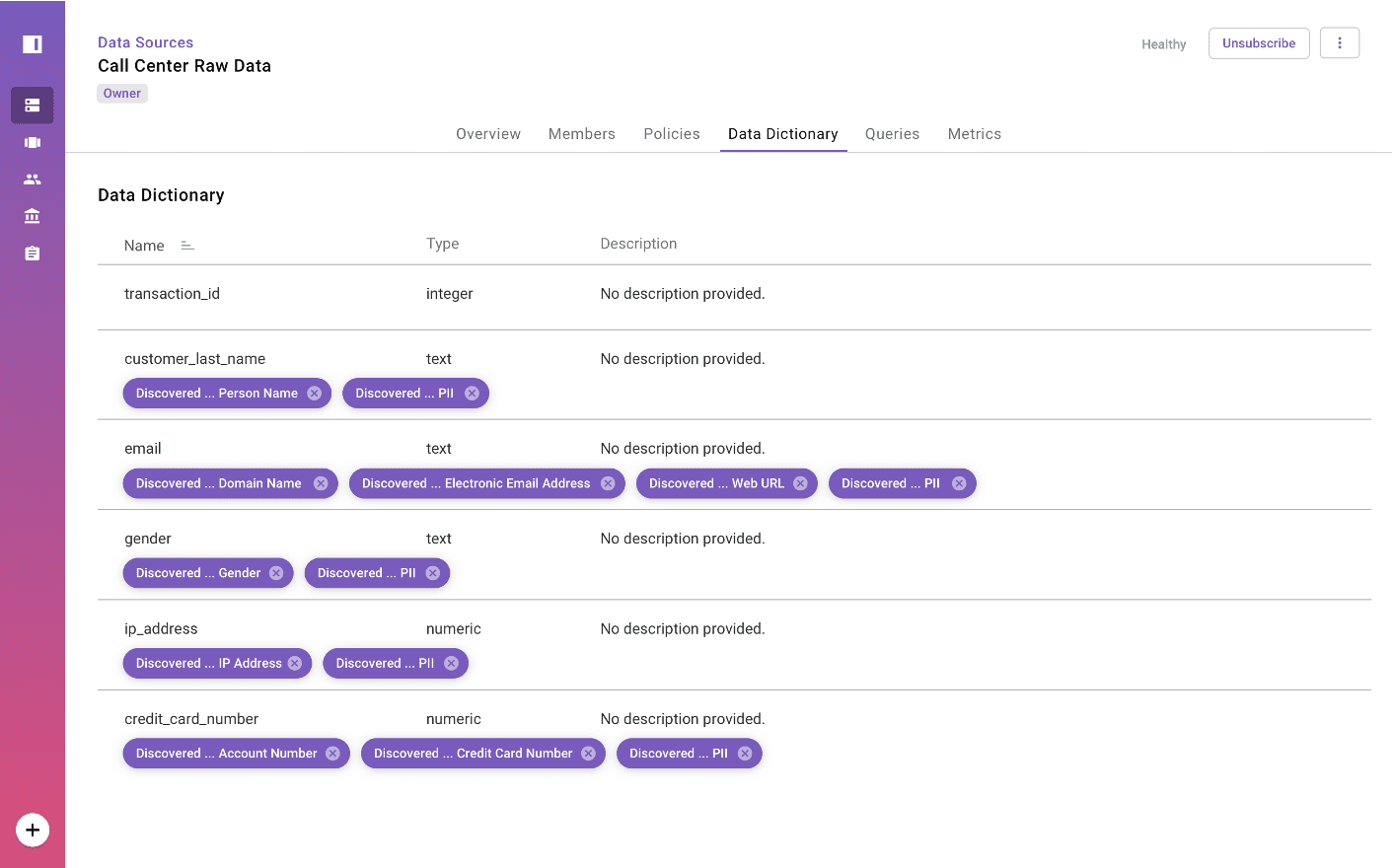
Immuta’s platform allows for comprehensive data tagging, to enrich the data catalog.
To combat the issue of data reliability, Immuta lets organizations operationalize existing catalogs and makes it easy to add new ones. By federating the external metadata, users can query from one catalog while accessing many, without the need for costly cloud migrations or connections. Using the information already gathered and implemented in these catalogs, Immuta enables data stewards to build policies that help assure users that the data they’re accessing falls within compliance regulations, while giving data stewards peace of mind that unauthorized access won’t occur.
DoD Strategy Goal 6: Make Data Interoperable
“Properly exchanging data between systems and maintaining semantic understanding are critical for successful decision-making and joint military operations. Achieving semantic as well as syntactic interoperability using common data formats and machine-to-machine communications accelerates advanced algorithm development and provides a strategic advantage to the Department.”
A key challenge faced by analysts and data scientists within DoD is that data resides in different places and networks, and on different platforms, which may or may not be interoperable. It’s therefore often the case that the full spectrum of data is not available, and the end product does not represent the full picture. The move to common data formats and fabrics, and the push towards artificial intelligence and machine learning readiness, make this one of the most important goals within the DoD Data Strategy.
With Immuta, data sources are combined and connected to the end user based on their subscriptions and attributes, without the need to copy data from its current location, while being environment- and platform-agnostic. This means a user can query across fabrics and formats, without the need to use different machines, operating systems, or networks, all while policy is dynamically enforced on the data. Data tagging for interoperability also works for global data policy enforcement, allowing a much more maintainable system for policy execution. This shifts the goals of the organization away from finding the time and funding to make costly data migrations happen, and allows them to put their full focus on data discovery and data science operations.
DoD Strategy Goal 7: Make Data Secure
“As per the DoD Cyber Risk Reduction Strategy, protecting DoD data while at rest, in motion, and in use (within applications, with analytics, etc.) is a minimum barrier to entry for future combat and weapon systems. Using a disciplined approach to data protection, such as attribute-based access control, across the enterprise allows DoD to maximize the use of data while, at the same time, employing the most stringent security standards to protect the American people.”
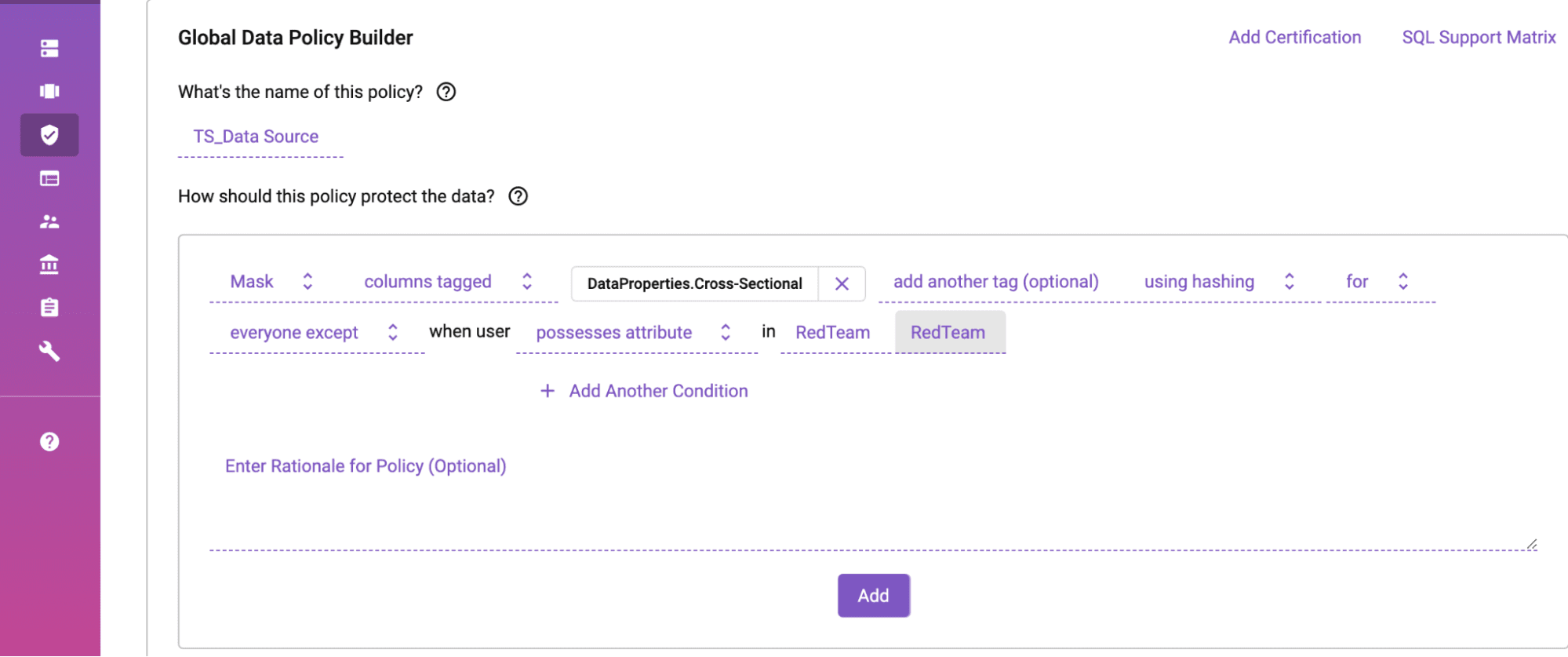
Attribute-based access controls dynamically govern data to provide organizations the highest level of privacy and utility.
The final and perhaps most important goal of the DoD Data Strategy is to make data secure. This involves granular privilege management, the need for compliance, access, and handling restrictions on metadata, and proper auditing of data use, access, and disposition.
Objective 1 of this goal speaks to granular management implementation to govern the access, use, and disposition of data. Immuta’s platform is based on attribute-based access control, which is the only way to effectively manage data at scale. Traditional role-based access controls rely heavily on manual maintenance of data sources and user permissions, and tend to require frequent code updates to maintain data pipelines. Due to the increasingly complex nature of data policy and the need for near real-time data access, this model struggles to keep up with demand.
In contrast, modern fine-grained access controls are what Immuta is all about. By combining a zero-code policy engine with plain English rules, it’s easy for data engineers and data stewards to effectively manage and maintain enterprise policy and to scale across users. For data that isn’t meant for the end user, privacy-enhancing technologies (PETs) like row-level redaction, and column- and cell-level masking, give data stewards granular control over access and visibility. Through the use of attribute-based access controls and global level policies, metadata tagging can easily be implemented and maintained.
Meanwhile, Objective 7 states that metadata and data are bound data in an immutable manner, eliminating the ability to falsely copy or tamper with protected data sources. Since Immuta works across platforms and enforces policies on data from any source as it’s queried, data scientists and analysts are able to query data without copying or migrating it. This creates one unified and federated metadata store, where access is governed and policy is dynamically enforced, and avoids the elevated risk associated with data copies and data silos.
Finally, Objective 8 deals with the need for a fully-audited solution. When using Immuta, the enterprise can prove who used what data, when, and why, and can access this information in rich, plain-English data audit reports. This allows for compliance with any regulation or compliance rule, while reducing the risk of security violations or data breaches. Automated reporting allows for straightforward and timely analysis and review of action.
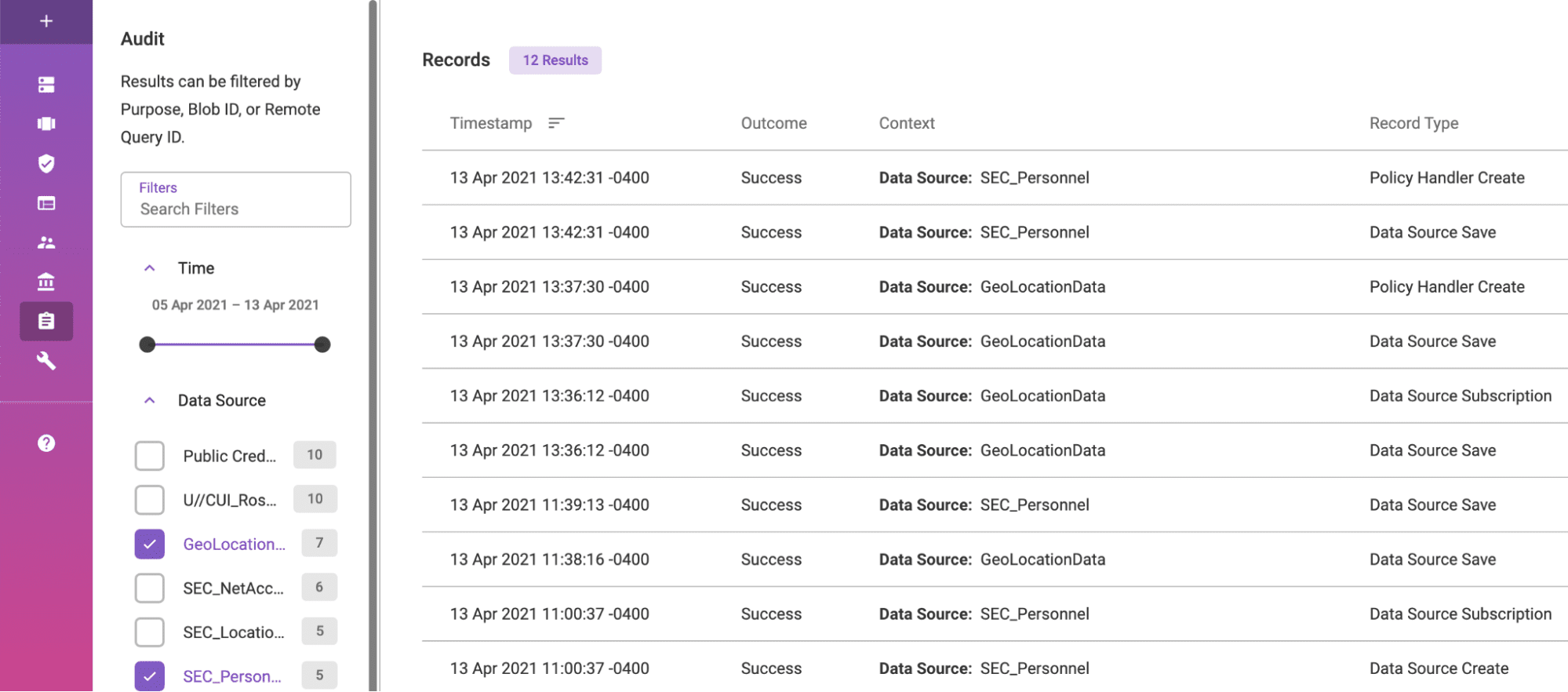
Immuta’s plain English audit capability ensures that all data access is logged and timestamped.
DoD Data is an enterprise resource, and the fuel that goes into every DoD process, algorithm, and weapon system, and as such, the requirement for strong and effective data management is crucial to the successful implementation of the DoD Data Strategy. Immuta’s automated, universal data access control platform is the modern solution for data management, and our capabilities uniquely position us to help our partners deliver on these goals.
Ready to learn more? Explore how Immuta enables secure data use for the Public Sector and request a demo of Immuta today.










