Organizations today are under more pressure than ever to deliver data quickly and securely. Data scientists, analysts, and business users all need fast access to trusted data to make decisions and power analytics.
To meet this demand, many companies are decentralizing access decisions — giving domain stewards and data governance teams the authority to provision access themselves instead of waiting on centralized IT. This shift is essential for agility, but it poses a big question: How do you keep control when more people are responsible for granting access?
As access decisions become distributed, the potential for error grows. A single mistaken approval can expose sensitive data or create compliance issues.
That’s why we need guardrail policies — the built-in safeguards that ensure even if someone makes a mistake, the data stays protected.
What is a guardrail policy?
A guardrail policy is a non-negotiable eligibility filter for data access, which determines who can be considered for access to a dataset.
Guardrail policies prevent users from subscribing (that is, actually gaining access) to a dataset unless they meet specific conditions. Even if a steward or manager accidentally approves a request, the guardrail blocks access if the user doesn’t meet those conditions.
They work alongside grant or subscription policies, which handle the normal process of granting access. In short, guardrails define who may ever be eligible; grant policies decide who among them actually gets access.
If multiple guardrail policies apply, they combine using “AND” logic — meaning a user must meet every condition before they can be eligible for access. Guardrails merge only with other guardrails or global ABAC (attribute-based) policies, which actually do the work of subscribing users and are based on user attributes, data tags, or environmental context.
Why guardrail policies matter
Modern data provisioning relies on striking a balance between speed and security. As data ecosystems scale, more stewards make more access decisions, and governance teams need assurance that mistakes won’t lead to breaches or violations.
Guardrail policies create that assurance. They embed compliance directly into the data layer, enforcing boundaries automatically — before a single query ever runs. They don’t make access easier; they make it safe to decentralize. Decentralization improves efficiency and decision-making across the entire enterprise.
Even as access becomes more automated and domain-driven, guardrails keep compliance constant.
How guardrails fit into the data provisioning framework
Here’s how guardrails work inside Immuta’s provisioning flow:
- A user requests access to a dataset.
- Before any approval takes effect, guardrail policies check whether the user is eligible at all.
- If any guardrail condition fails, access is denied automatically — no exceptions.
- Immuta continues checking eligibility as user attributes or data tags change, instantly revoking access when a condition is no longer met.
This dynamic model allows you to decentralize access without losing control or consistency.
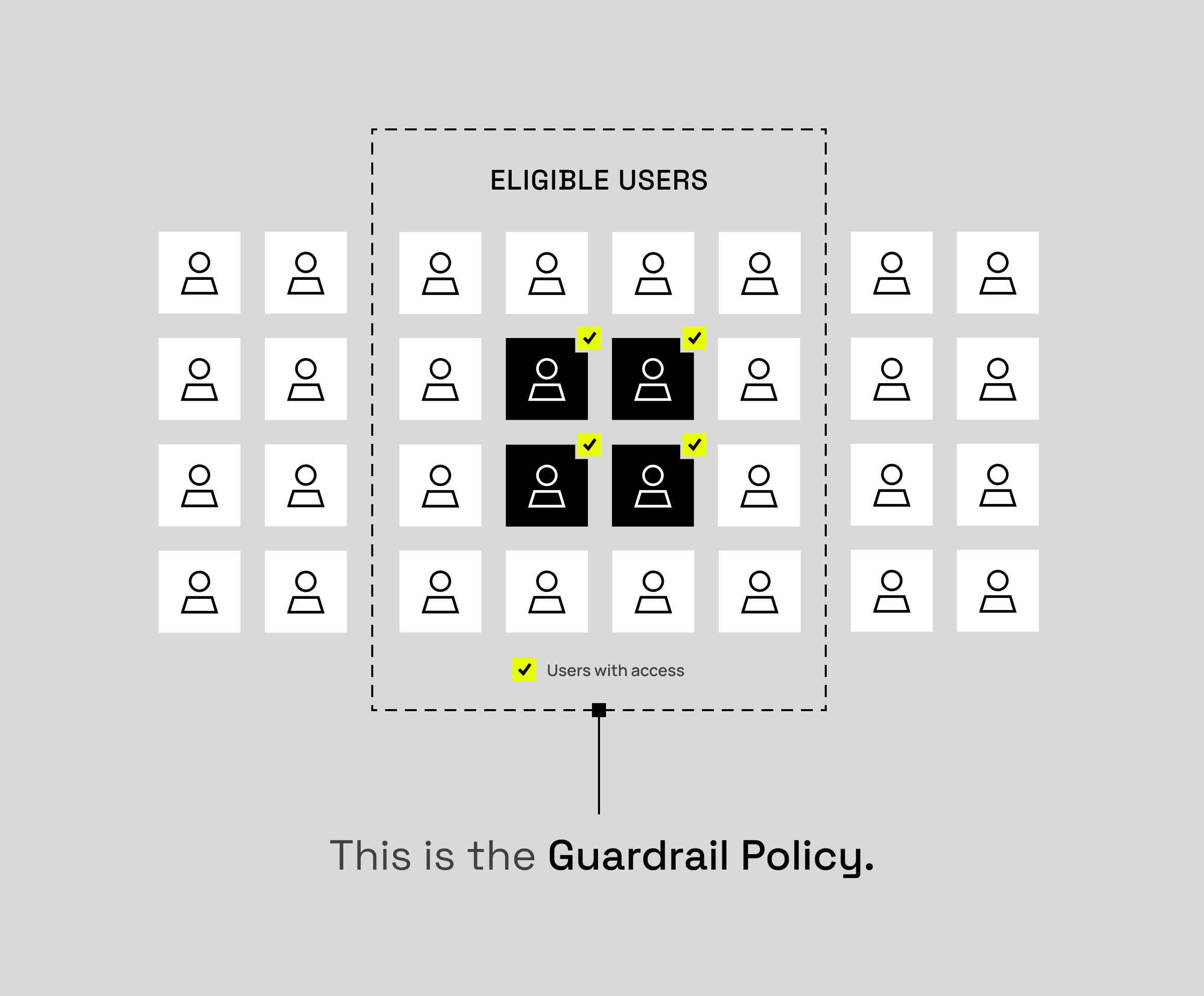
The diagram below illustrates how guardrail policies isolate different groups of users based on eligibility rules. Even as multiple stewards and domains manage access, guardrails ensure each group remains securely confined within its approved boundaries. This allows you to publish single versions of your data rather than multiple security-level versions of your data.
Real-world use cases
Guardrail policies aren’t just theoretical — they were built in partnership with our customers. Organizations across industries, from pharmaceuticals to financial services, pushed for a way to automate access eligibility as they scaled data provisioning and decentralized governance. Their requirements directly shaped how we designed guardrail policies to enforce compliance without slowing teams down.
Below are a few examples inspired by those customer partnerships — real-world scenarios showing how different sectors use guardrails to enable secure, scalable, and compliant data access.
Pharmaceuticals and life sciences
Clinical trials contain protected health information (PHI) and patient data governed by HIPAA, GDPR, and 21 CFR Part 11. Guardrail policies ensure that only Institutional Review Board (IRB)-approved researchers who’ve completed good clinical practice (GCP) training and are located in approved regions can view subject-level data.
allow if user.role == "ClinicalResearcher"
and user.hasTag("IRB_Approved")
and user.training_status == "GCP_Completed"
and user.location in ["US", "EU"]
Even if a steward accidentally approves a user without these attributes, Immuta blocks access automatically — protecting patients and sponsors alike.
Financial services
Banks and trading firms must maintain strict separation between departments to comply with industry regulations. Failure to do so increases the risk of insider trading, conflicts of interest, and fraud, not to mention the steep penalties associated with them.
allow if user.department NOT "EquityResearch"
and dataset.tag NOT "MergersAndAcquisitions"
This guardrail guarantees that analysts never see M&A data, no matter who approves them, keeping firms compliant with SEC and FINRA rules.
Healthcare providers
Healthcare organizations often rely on global teams to manage infrastructure, run analytics, and support operations. For example, a healthcare company may have IT or engineering staff based in India supporting systems that serve U.S. patients.
Because of HIPAA and cross-border data residency laws, those offshore employees must not have access to any PHI belonging to U.S. customers — even if they work within the same environment.
Guardrail policies automate enforcement of this rule by evaluating both user location and dataset sensitivity before access is ever granted.
allow if user.location NOT "India"
and dataset.tag NOT "PHI"
and dataset.region NOT "US"
This ensures that offshore IT personnel can still perform their system maintenance or analytics duties — but without ever seeing or querying patient-identifiable data. It eliminates the risk of accidental exposure while maintaining compliance with HIPAA and cross-border privacy laws.
The big “so what”
As organizations democratize data, the challenge isn’t simply giving more people access — it’s making sure that access remains safe, compliant, and trustworthy. Guardrail policies are the foundation that makes this possible.
They aren’t just technical rules; they’re the safety net of modern data provisioning.
Yes, they prevent human error and enforce compliance automatically. But their real power lies in creating confidence. When access decisions are decentralized, you suddenly have dozens or hundreds of new approvers — stewards, analysts, product managers — making decisions that carry risk. Most of them don’t have deep regulatory or data-domain expertise, and that can create hesitation and fear.
Guardrail policies remove that fear. They give novice approvers peace of mind, knowing that even if they make a mistake, the system itself will block anything unsafe before it happens. That psychological safety makes participation in governance possible — and that’s what turns policy into progress.
A good data-provisioning platform doesn’t just protect data; it empowers people. Guardrails make it safe to say “yes” to data access without second-guessing every decision. They lower the barrier to collaboration while keeping the organization — and its people — protected.
In the end, that’s what guardrail policies really deliver: trust, confidence, and control. They make data democratization sustainable — allowing organizations to move fast, innovate freely, and still stay safe.
Take a closer look.
Explore guardrail policies in practice.





